In this section, we will acquire knowledge on safeguarding ourselves from malicious delivery methods. One effective approach is utilizing tools such as XArp or static ARP tables, which can help prevent a potential man-in-the-middle attack and restrict access to unknown networks. Additionally, it is essential to ensure the use of HTTPS when downloading updates, as this can mitigate the risk of downloading a counterfeit update. By implementing these precautions, we can improve our security posture and reduce the likelihood of falling victim to an attack.
In this section, we’ll become acquainted with another useful tool called WinMD5. This program enables us to detect any modifications made to a file’s signature or checksum, indicating that it is no longer the original file. To confirm this, we’ll download and run WinMD5, which will allow us to compare the signature and checksum of the file. If both values match, the file is safe. To obtain WinMD5, we can use the following hyperlink: http://www.winmd5.com/.
In the given screenshot, the highlighted portion illustrates the signature of the tool.
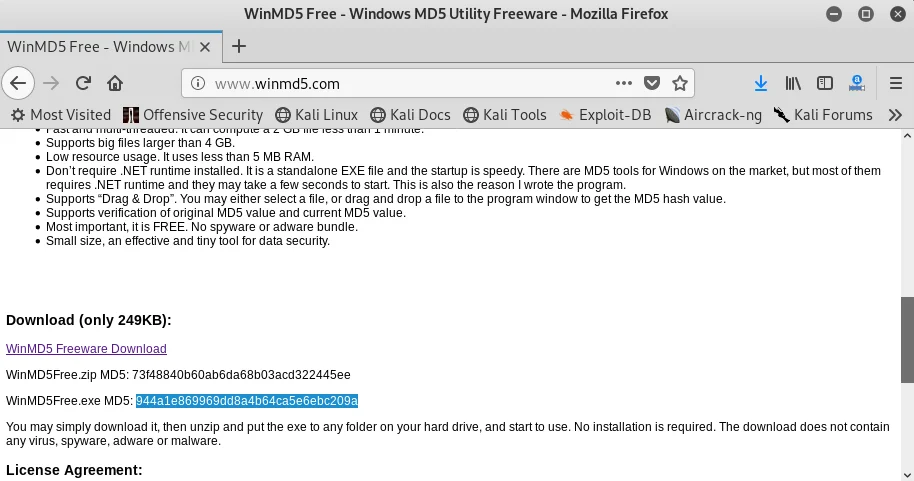
When browsing, the signature files are displayed, and in this instance, we will choose the downloaded file for the tool. We will proceed to compare this signature with the one on the website, and as shown in the screenshot, the signatures match. Therefore, we can conclude that the tool has not been altered and was downloaded from the website.
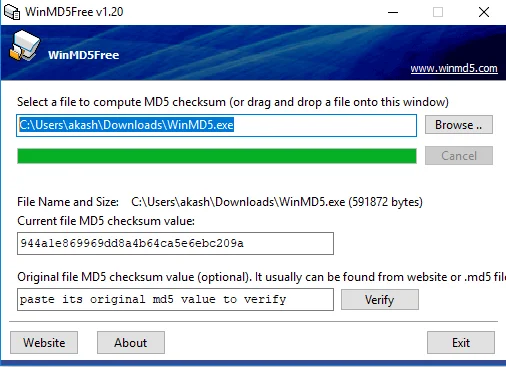
We hope the information provided about Protecting Against Delivery Methods has been useful. For more insights into Ethical Hacking, you can follow us at tutorials.freshersnow.com.
