Once Veil-Evasion is successfully installed, we can explore its various commands, which are relatively simple and easy to use, as shown in the accompanying screenshot. The available commands include “exit“, which allows us to exit the program, “info“, which provides information about a specific tool, “list “, which displays a list of available tools, “update“, which is used to update Veil-Evasion, and “use“, which enables us to utilize a specific tool.
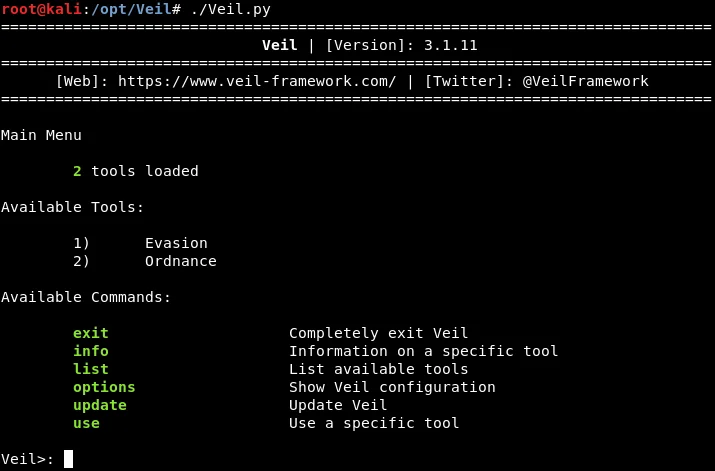
Based on the above screenshot, Veil comprises of two primary tools:
- Evasion: This tool generates a backdoor that is difficult to detect.
- Ordnance: This tool creates payloads utilized by Evasion, making it more of a secondary tool.
The payload is a code segment that performs a specific task as per our requirements. In this instance, it facilitates a reverse connection, enabling the download and execution of something on a targeted computer. To activate the required tool, we are using the “use” command. In this case, we intend to use “Evasion,” so we will execute the command “use 1.” Once Veil-Evasion has loaded, the command prompt should display something resembling the following output.
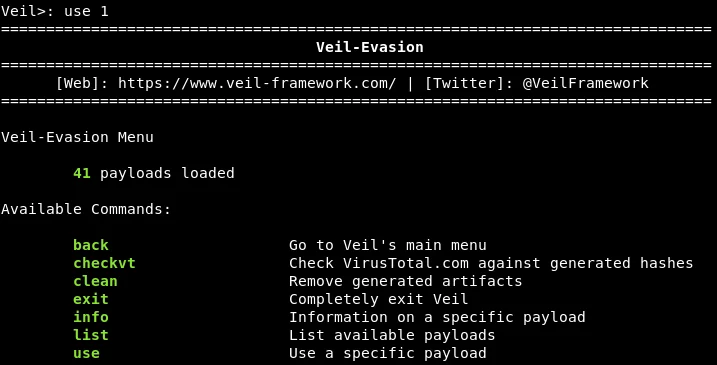
As illustrated in the previous screenshot, Veil-Evasion provides users with a comprehensive list of available commands that can be executed using the tool. To access the list of available payloads, we can use the appropriate command, which reveals a total of 41 unique payloads. From this list, we have identified three specific payloads, which are denoted by their corresponding index numbers. The highlighted payloads, which we intend to use, are as follows: “15) go/meterpreter/rev_https.py“.
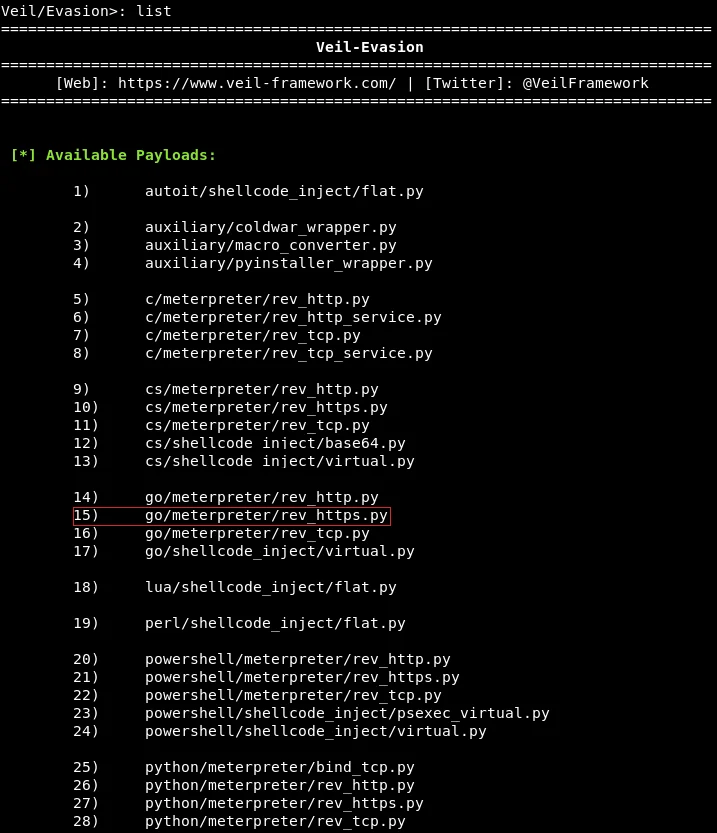
As demonstrated in the previous screenshot, the initial section of a payload’s name specifies the programming language used to wrap it. The available languages include CS, Python, GO, C, PowerShell, and Ruby. For this example, we will employ the go language.
The second component of the payload is the payload type, indicating the type of code that will execute on the target network. In this instance, we will utilize Meterpreter, a payload created by Metasploit, which is a comprehensive framework frequently used for hacking. Since Meterpreter operates in memory, it is tough to detect and does not leave a significant footprint. With Meterpreter, we can acquire complete control of the target computer, permitting us to browse through the file system, install or download files, and perform numerous other operations.
In Veil-Evasion, the third part of a given payload’s name represents the method that will be utilized to establish a connection to the target machine. In the case of the highlighted payload, “rev_https” is the designated method, which stands for “reverse HTTPS”. This indicates that the connection will be established through the use of the HTTPS protocol. Within the list of available payloads, there are several examples of other methods, such as “rev_tcp“, which creates a reverse TCP connection, as illustrated in the previous screenshot.
In a reverse connection, the target machine establishes a connection to the attacker’s machine through a backdoor. This technique circumvents antivirus programs because the connection is directed to the attacker’s machine rather than the target computer. In the current example, we will employ port 80 or 8080, which many websites use, to make the connection appear as a harmless website connection.
Thank you for choosing this page to gain insight into the Overview of Payloads. For further information on the subject of Ethical Hacking, we encourage you to follow us at tutorials.freshersnow.com.
