In this section, we will explore the process of obtaining information regarding the technologies utilized by a target website. We will accomplish this by utilizing a website known as Netcraft (https://www.netcraft.com), entering the target website address, selecting our intended target as isecur1ty.org, and clicking on the arrow icon as illustrated in the screenshot.
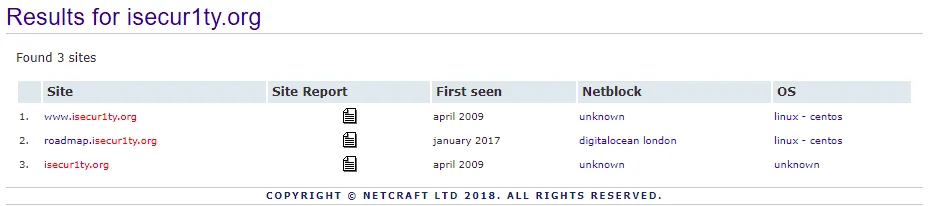
Next, you should proceed by selecting the “Site Report” option, which is indicated in the screenshot provided, after entering the target website address and selecting your intended target as isecur1ty.org. This step is crucial in obtaining a detailed report on the technology stack employed by the target website.
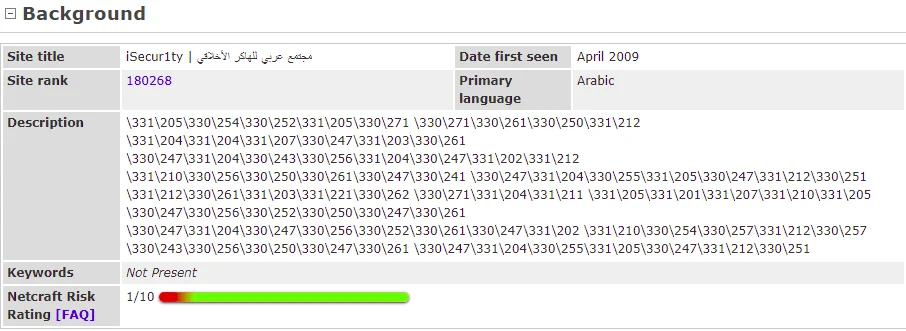
The screenshot displays fundamental details such as the Site Title, Site Rank, Description, Keywords, and the date of the website’s creation. These key pieces of information provide a basic overview of the target website and are readily visible in the provided screenshot.
As we scroll down the page, we are presented with additional details such as the website, Domain, IP address, and Domain registrar responsible for registering the isecur1ty.org domain. This information is crucial in gaining a more in-depth understanding of the target website and its underlying infrastructure.
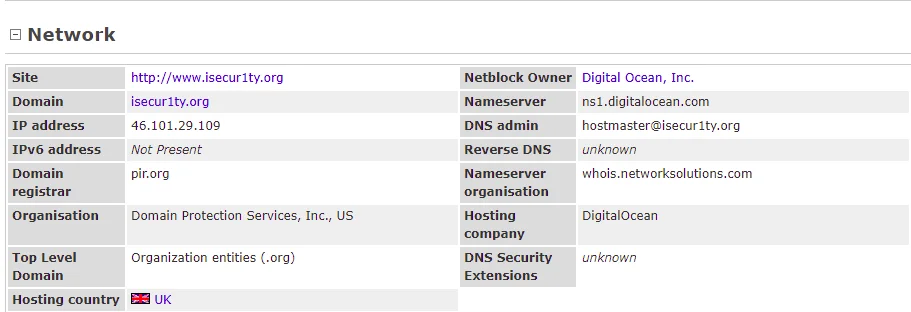
Typically, the preceding screenshot would display details regarding the organization associated with the target website. However, in this case, this information is not available as isecur1ty.org has enabled privacy protection. Ordinarily, one would expect to see additional information such as the website owner’s contact information, location, and other pertinent details.
Upon examining the previous screenshot, we can determine that the target website is hosted in the UK, as well as identify its Nameserver, which is ns1.digitalocean.com. If we navigate to ns1.digitalocean.com, we will discover that it is a website that provides web hosting services. This information is essential in understanding the technological infrastructure utilized by the target website.
It is common knowledge that the company in question provides web hosting services, and in the event of a worst-case scenario, it may be attempted to gain access to isecur1ty by potentially hacking into ns1.digitalocean.com.
By continuing to scroll down, we can observe the Hosting History of the companies that isecur1ty has utilized. As indicated, the latest hosting company is employing Linux with Apache, the same server we previously identified in section two, operating with Unix mod_ssl and other add-ons.
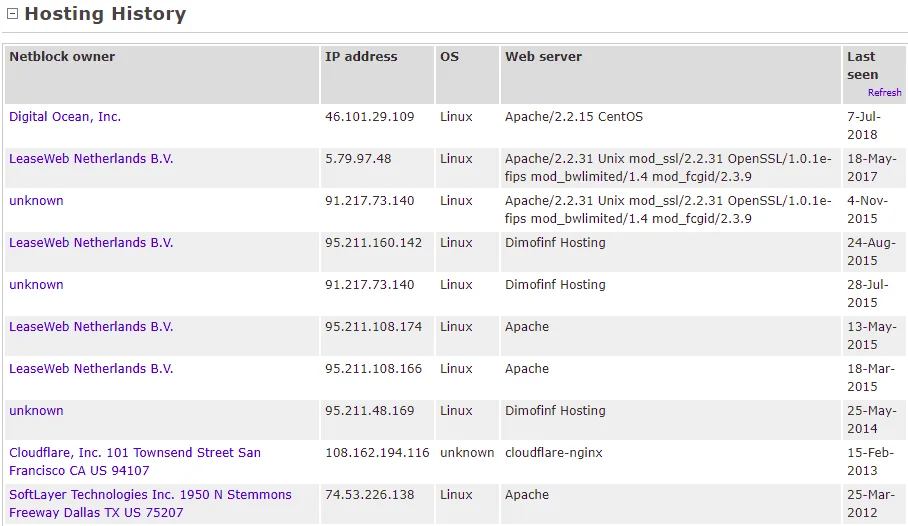
Identifying and leveraging this information is crucial in identifying potential security vulnerabilities and exploits on the target system, making it an integral part of the reconnaissance process.
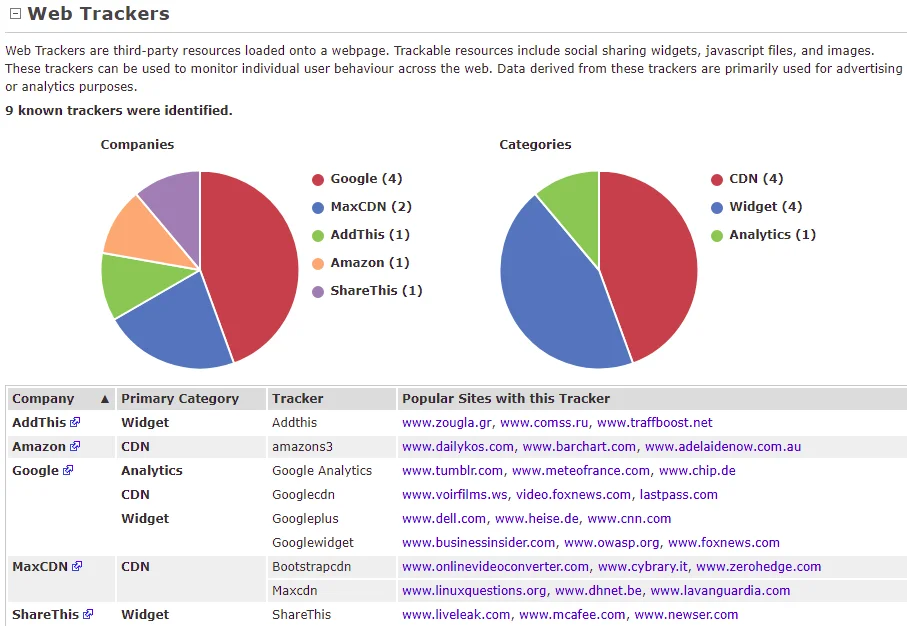
By scrolling down to the Web Trackers section, we can identify the third-party applications being used on the target website, such as MaxCDN, Google, and other Google services. This information could potentially assist us in discovering vulnerabilities and gaining unauthorized access to the target computer, as illustrated in the provided screenshot.
The Technology tab provides a detailed breakdown of the various technologies utilized by the target website, allowing us to gain a more comprehensive understanding of its underlying technological infrastructure
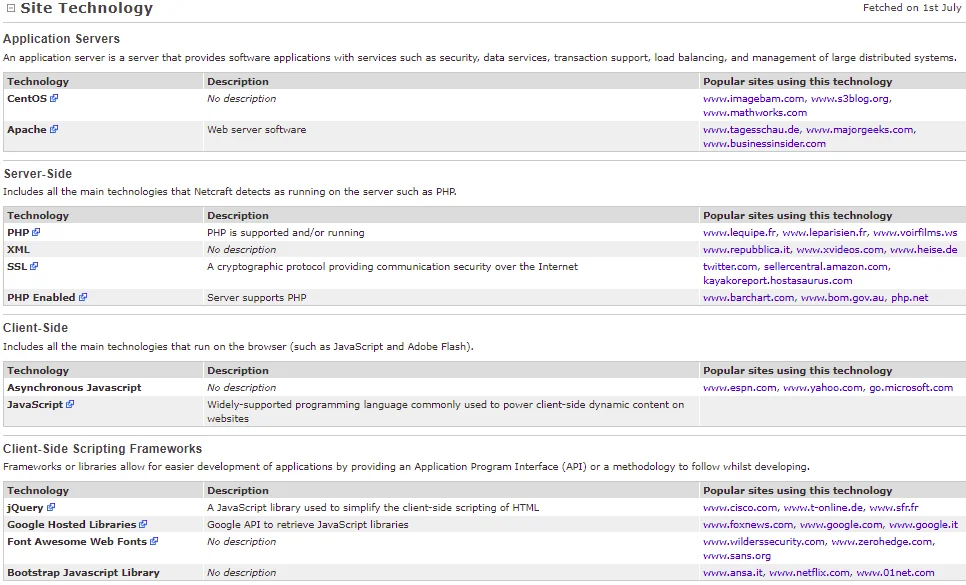
From the previous screenshot, it is evident that the target website is utilizing the Apache web server. The Server-Side section of the Technology tab reveals that the website is programmed using PHP, allowing it to comprehend and execute PHP code. If successful in executing code on the target website in the future, it should be delivered in the form of PHP code. When generating payloads on tools such as Metasploit or Veil-Evasion, it is necessary to create them in PHP format to ensure the target website can interpret and run them. This information is essential in crafting a targeted exploit for the vulnerable system.
According to the screenshot, it seems that the website has support for JavaScript. Therefore, any JavaScript code that is run on the website will be executed on the client-side, which means that it will run on the devices of the users who are browsing the website. On the other hand, PHP is a server-side language, so any PHP code that is executed will be run on the server. It’s important to note that jQuery is simply a framework for JavaScript and operates in the same manner as other JavaScript code.
Based on the provided screenshot, it appears that the website is utilizing WordPress Self-Hosted software. This information can be obtained through Netcraft, which has the ability to detect and display any web applications being used by the website.
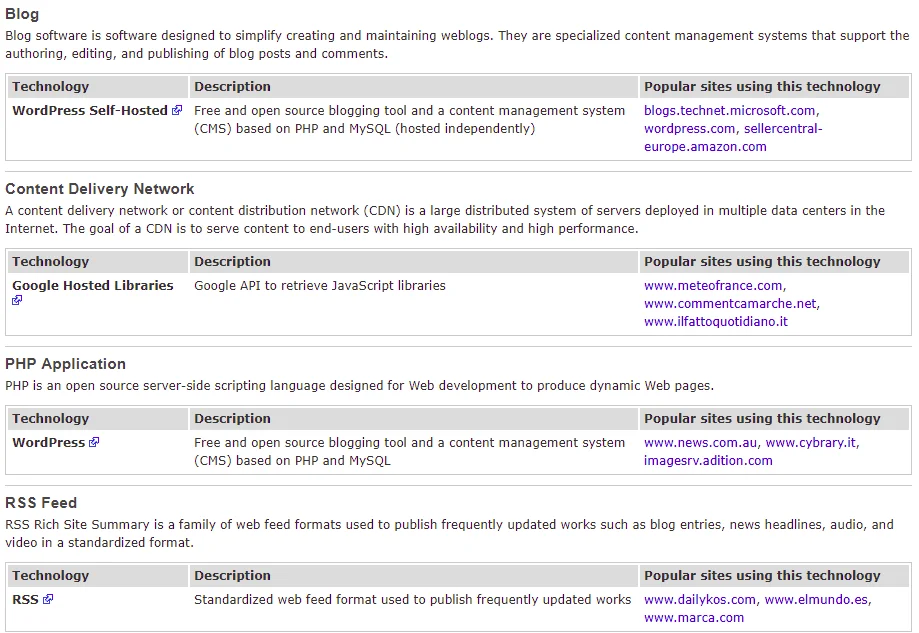
WordPress is an open-source web application, and there are numerous websites employing this technology. If we are fortunate enough to discover a pre-existing vulnerability in the web application, it can be leveraged to target the website successfully. A useful resource for identifying existing WordPress exploits is https://www.exploit-db.com/. By performing a search for WordPress on this site, a wealth of exploits related to WordPress can be found, offering potential avenues for exploiting the target website.
Information gathering is a powerful tool that can be used to find various details about the target. In this case, we need to ensure that we have the same WordPress version as the target. Moreover, we can obtain other important details such as the use of HTML5 and CSS by the website by scrolling further down. The following screenshot illustrates this.
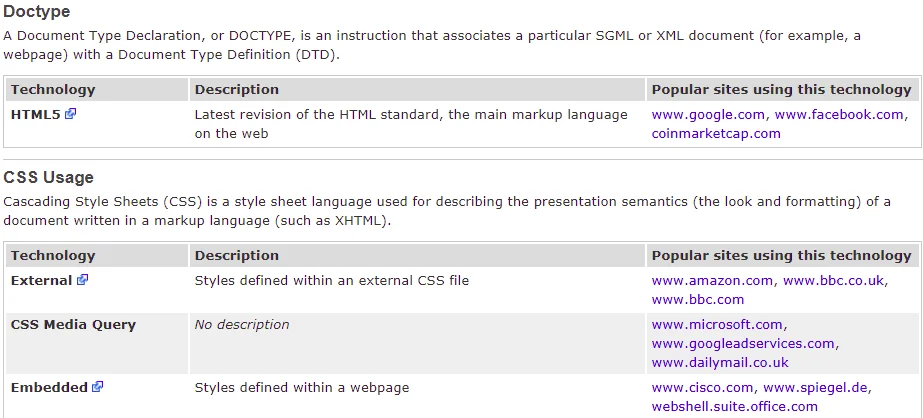
Consequently, Netcraft is employed to acquire information about the website. Through this, we obtained knowledge that the website is utilizing PHP and JavaScript, and operates on WordPress, which can potentially be exploited. By scrolling up, we also discovered the website’s web hosting provider. In extreme situations, we may attempt to breach the web hosting server and gain access to our intended target.
If you’re interested in learning more about topics such as Netcraft in the field of ethical hacking, we encourage you to visit our website @ tutorials.freshersnow.com regularly for additional information and updates.
