In the previous section, we demonstrated how to crack a WEP key on a busy network. However, cracking a WEP key on a network that is not busy could be a challenge. The number of data packets captured will increase at a very slow rate in such a network. To overcome this issue, we can fake as an access point (AP) with no clients connected or an AP with a client connected but not using the network heavily.
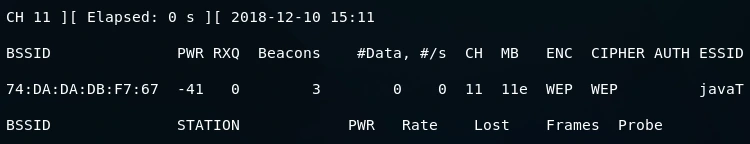
For example, let’s consider the network, but this time we will disconnect all clients to simulate a less busy network. When we run airodump against this target AP, we can see that no clients are connected, and the #Data remains at 0.
In this section, we will discuss how to crack a WEP key on a network with 0 data packets.
To overcome this issue, we can use packet injection to inject packets into the network traffic. This will prompt the AP to create new packets with new IVs, which we can capture. However, prior to injecting packets, we need to authenticate our device with the target AP. Since APs have a list of all connected devices, they will ignore any packets coming from unconnected devices. If a device without the key sends a packet to the router, the router will simply ignore it without analyzing its contents. Therefore, before injecting packets, we need to authenticate ourselves with the router using a technique called fake authentication.
In the previous section, we used airodump to capture information about the target access point. To successfully perform packet injection, we need to authenticate our device with the target AP, which we can achieve through fake authentication. Once we have conducted fake authentication, the AUTH field in airodump output should change from blank to OPN, indicating that we have successfully authenticated our device with the target AP. To conduct fake authentication, we can use the following command:
![]()
To obtain our MAC address, we will execute the “ifconfig wlan0” command. Next, with aireplay-ng, we will perform a –fakeauth attack, specifying the type of attack and the number of packets we wish to send (i.e. –fakeauth 0). We will also use the -a flag to specify the target network (i.e. 74:DA:DA:DB:F7:67) and the -h flag to specify our MAC address.

In the given command, “wlan0” refers to the Wi-Fi card’s name that we are using. The intention of using “aireplay-ng” is to initiate a fake authentication attack that allows us to authenticate our MAC address, granting us permission to inject packets into the target network. To perform this attack, we use the following arguments: “0,” signifying the execution of the attack only once, “-a” followed by the MAC address of the Access Point (AP), and “-h” followed by the MAC address of the device we want to perform the fake authentication. Lastly, we use “wlan0,” the name of the Wi-Fi card we’re using in monitor mode. Upon entering this command, we will execute the attack.
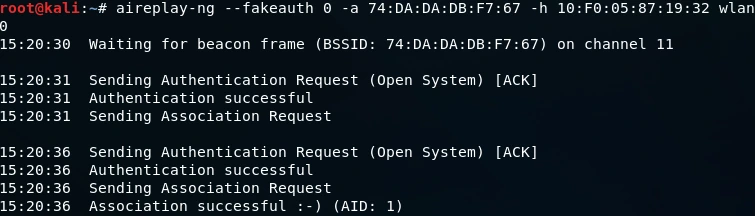
The depicted image reveals that an authentication request was transmitted by -a, which was verified as successful. Consequently, the network was rendered open, and our client was displayed as a network-connected client, albeit not physically connected. Nevertheless, we have obtained authentication with the network and established an association with it, enabling us to inject packets into the AP. As a result, any requests that we transmit to the network will be received by it.
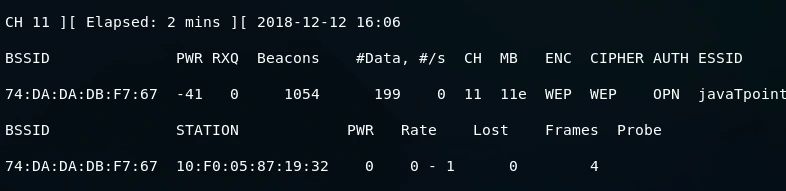
The information provided about the Fake Authentication Attack may be helpful to some users. However, it is important to note that this attack may be used for malicious purposes, and it is crucial to use this knowledge ethically and legally. Engaging in ethical hacking activities can help improve cybersecurity by identifying vulnerabilities and promoting better security practices. To stay informed about ethical hacking and related topics, it is recommended to follow @ tutorials.freshersnow.com.
