To crack WPA or WPA2, the first step is to capture the handshake from the target AP. Once the handshake is captured, the next step is to have a wordlist containing potential passwords that can be used to crack the key for the target AP. With both the handshake and wordlist ready, aircrack-ng can be used to initiate the cracking process. Aircrack-ng takes each password from the wordlist and combines it with the name of the target AP to create a Pairwise Master Key (PMK) using an algorithm called PBKDF2. The PMK is then compared with the captured handshake. If the PMK is valid, the password used to create it is the correct password for the target AP. If the PMK is invalid, aircrack-ng moves on to the next password in the wordlist.
To proceed with the cracking of WPA or WPA2, the next step is to use aircrack-ng. This involves providing the file name that contains the captured handshake, which is wep_handshake-01.cap, along with the -w option, and the name of the wordlist file, which is text.txt.
![]()
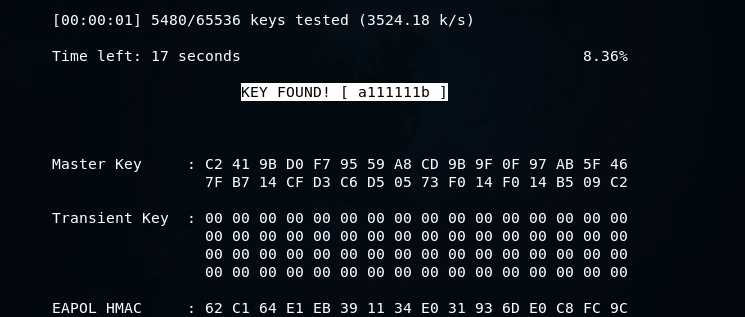
Upon clicking Enter, aircrack-ng will systematically go through the list of passwords and attempt to generate a PMK by combining each password with the name of the target AP. Subsequently, it will compare each PMK with the captured handshake. If the PMK is valid, then the password used to create it is the correct password for the target AP. If the PMK is invalid, aircrack-ng will move to the next password in the list.
From the provided screenshot, it is evident that aircrack-ng was successful in finding the key.
We recommend that learners follow our updates regularly @ tutorials.freshersnow.com to gain more insight into topics related to Ethical Hacking, such as Wordlist Cracking.
