In this segment, we will cover WEP (Wired Equivalent Privacy), which is the oldest encryption method and can be easily compromised. WEP employs the RC4 encryption algorithm, in which each packet is encrypted by the router or access point before being transmitted into the air. Upon receiving the packet, the client can reverse the encryption and restore it to its original form using the key. Put another way, the router encrypts and sends the packet, while the client receives and decrypts it. The same process occurs when the client sends something to the router, where the packet is first encrypted with the key, sent to the router, and decrypted since it has the key. If a hacker captures the packet in transit, they will receive the packet but won’t be able to decipher its contents since they don’t have the key.
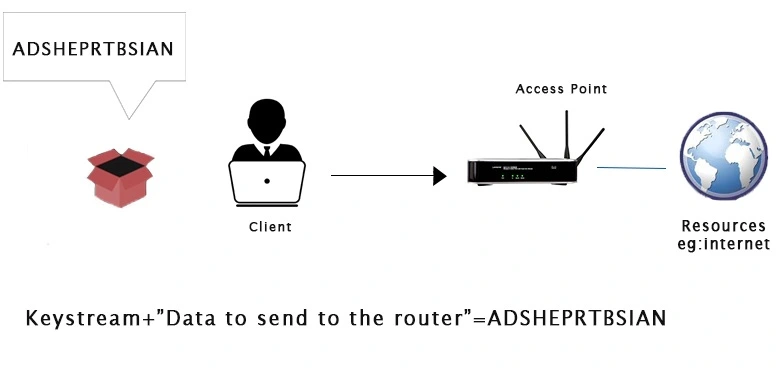
Every packet transmitted over the air is associated with a distinctive keystream that is produced by utilizing a 24-bit Initialization Vector (IV). The IV, which is an arbitrary number, is incorporated in plain text format within each packet and is not subjected to encryption. In the event of an interception of the packet, the content remains unreadable due to encryption, but the plain text IV can be accessed.
Due to its short length (only 24-bit) and transmission in plain text, the Initialization Vector (IV) presents a significant weakness in the security of WEP. In a busy network, with numerous packets being transmitted, the IV may start to repeat, rendering it insufficient to ensure secure communication. As the IVs begin to repeat, the key stream can be deciphered, making WEP susceptible to statistical attacks.
The tool commonly known as “aircrack-ng” can be utilized to determine the key stream necessary to crack WEP. By collecting a sufficient number of repeated IVs, the tool can effectively crack WEP and provide access to the network key.
Explore more about ethical hacking, including topics such as the WEP Introduction, by following us @ tutorials.freshersnow.com.
