Routers
Routers serve as hardware devices that facilitate the transmission of data packets between disparate networks by serving as gateways at their interconnecting points. For instance, to link a local area network (LAN) to an internet service provider (ISP), one may employ a router, thus enabling network access to the internet.

Working of Routers
The router examines the source and destination IP addresses of each packet before consulting the routing table to determine the appropriate network path for the data to travel towards its destination. The router selects the most efficient path if multiple routes are available to reach the destination IP address. However, if the destination IP is not listed in the routing table, the router will forward the packet to the default router. If the packet lacks a destination, it will be discarded.
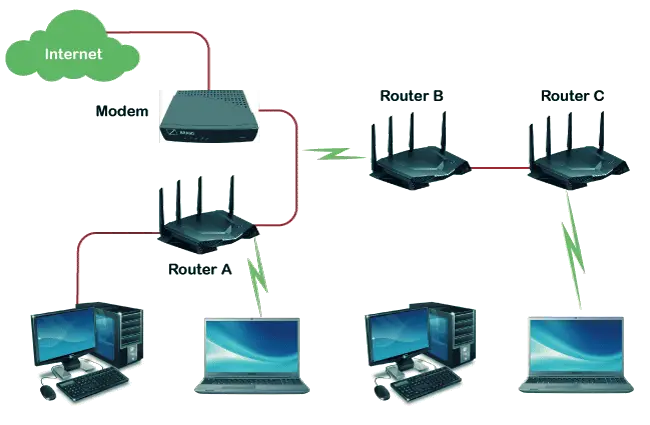
In most cases, routers are equipped with multiple ports to enable simultaneous connections of multiple devices to the internet. The routing table is utilized by the router to determine the source of incoming traffic and the appropriate destination for data transmission. Typically, Internet Service Providers (ISPs) provide routers to their subscribers and assign them public IP addresses, which are used to identify devices on the internet. Private IP addresses are assigned to individual devices such as laptops, desktops, TVs, media boxes, and network copiers by the router, thereby ensuring their protection. Without unique private IP addresses, the router would be unable to identify the device making the request.
Importance of Router
There are several advantages of utilizing a router, including:
- Ethernet is the most widely used type of network, although others such as Token Ring and ATM also exist. To ensure data cannot be directly communicated, different methods are employed to encapsulate the data or packets within the network. Routers play a critical role in translating packets that originate from different networks, enabling them to understand and communicate with one another.
- To prevent a broadcast storm, routers are utilized. Without a router, a broadcast would be transmitted to every port of every device on the network, overwhelming the devices if there are numerous broadcasts. Routers divide a network into several smaller subnets, which are linked by the router. The router blocks the broadcast from transmitting between subnets, preventing chaos in the network caused by a large number of broadcasts.
Security features of Routers
Routers provide various security features such as:
- To avoid unauthorized access, password-protected networks can be established.
- Secured routers can mitigate the risk of malware attacks.
- Protected data can be ensured by utilizing secure routers.
- Sophisticated routers can offer supplementary protection against DoS attacks.
Firewall
A network firewall functions as a barrier that safeguards a private LAN by separating it from the internet. Its main objective is to prevent data leakage and protect sensitive information. Without a firewall, routers merely pass traffic between networks indiscriminately. Conversely, a firewall scrutinizes traffic, blocking any unauthorized data from being transmitted outside. By segmenting regular and critical data within the LAN, a network firewall can reduce the likelihood of internal breaches. Furthermore, the firewall can quantify the number of threats that have been blocked, preventing outside users from accessing the private network. If remote access is permitted, a Demilitarized Zone (DMZ) can be established using the firewall’s built-in option. This configuration designates a directory on the gateway computer, similar to a Demilitarized Zone. Additionally, some firewalls offer virus protection, although installing anti-virus software on each computer is recommended.
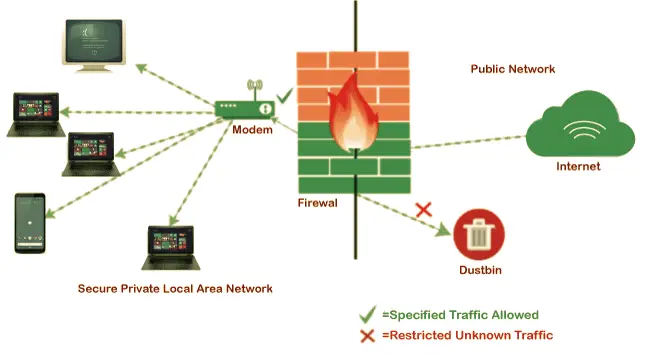
Working of Network Firewall
Certain hardware firewalls permit the user to set up blocking rules based on criteria such as UDP or TCP protocols, as well as IP addresses and ports, thereby enabling the user to prohibit access to undesired IP addresses and ports. In addition to hardware firewalls, software applications and services provide another type of firewall that functions like a proxy server, linking two separate networks. The use of both a hardware and software firewall in combination enhances security and efficiency.
Importance of Firewall
- A home computer can be safeguarded using a firewall, while a hardware firewall should be employed if multiple computers exist in a network. If using a public computer, it is important to comply with the network administrator’s regulations.
- The purpose of a firewall is to safeguard an organization against cyber-attacks. By restricting traffic to authorized sources, a firewall can protect internal programs with exploitable vulnerabilities from harm by limiting the flow of traffic that passes through the network’s perimeter.
- A firewall acts as a boundary between the internal and external networks, providing a clear demarcation. Through filtering, a firewall solution enables easy access to external services for users within the network, while also enforcing access requirements for external computers attempting to connect to internal computers.
Security features of the firewall
- Suspicious traffic can be identified by employing a hardware firewall.
- The hardware firewall can obstruct data packets that appear questionable.
- Employing the NGFW firewall’s content analysis feature can help identify data leaks.
- A firewall can offer a secure network environment for multiple individuals to interact, such as in online video games.
- Employing a firewall can safeguard private information, such as online banking credentials and social security numbers.
We hope that you have gained a better understanding of Routers and Firewalls through this article. For further insights into the world of Ethical Hacking, be sure to follow us @ tutorials.freshersnow.com.
