After the scan completes, we will be redirected to the Assets page where we can view the results. As shown in the screenshot, the scan detected one asset running Ubuntu, and the required skill level to hack into this asset is “Novice“.
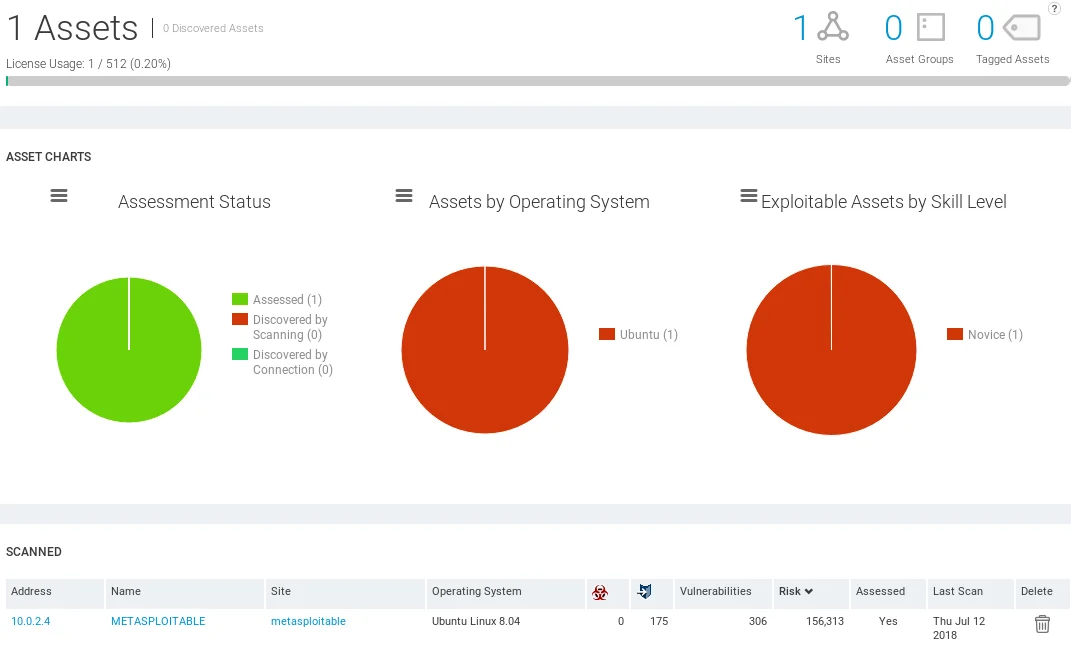
The previous screenshot illustrates that Nexpose provides a greater amount of information compared to Metasploit Community, indicating that it is a more sophisticated vulnerability management framework.
As shown in the screenshot, the scan was conducted on the “METASPLOITABLE” target, which is a Global site running Ubuntu Linux 8.04. The scan detected no malware but did uncover 175 exploits and 306 vulnerabilities. While Metasploit Community only found 1 exploitable vulnerability and 8 modules, Nexpose found many more vulnerabilities and exploits.
By examining the interface, we can observe the risk factor and the date of the previous scan, while scrolling down reveals the Operating System, which is Ubuntu Linux 8.04, as well as the list of Software that is currently installed on the target computer.
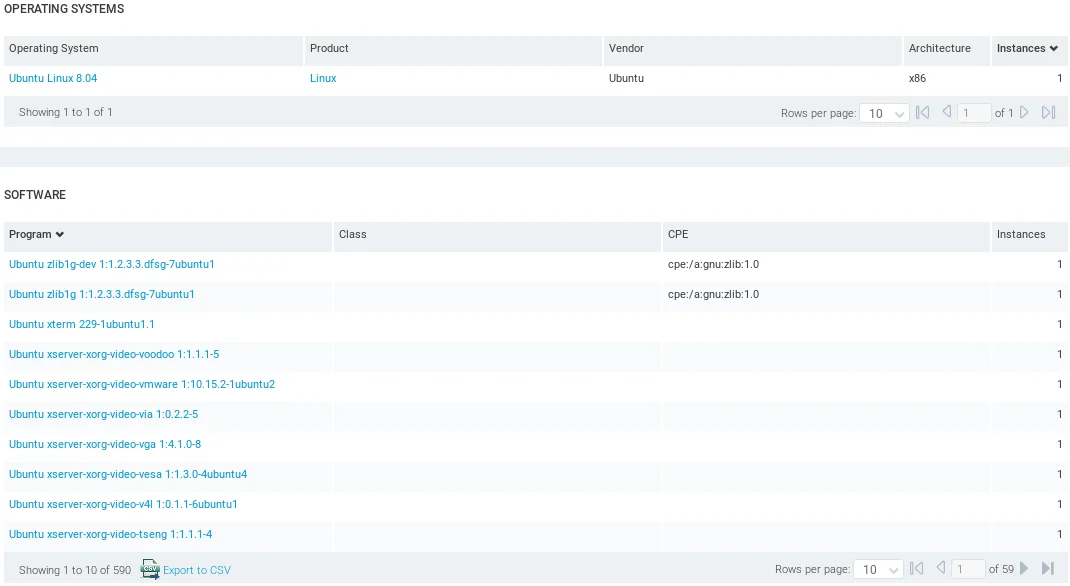
Local exploits can be very helpful to escalate our privileges after gaining initial access to a target. For instance, a local buffer overflow can be used to increase our privileges from a normal user to root, allowing us to perform additional actions in the post-exploitation phase.
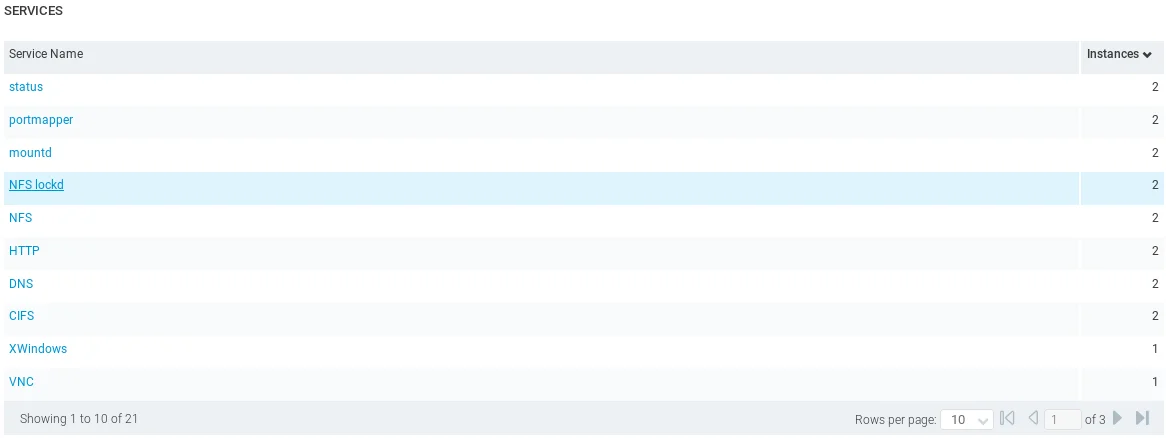
Upon scrolling further down, we can view the services that are present on the target computer, including HTTP, DNS, and others, as well as the status indicating that they are operational.
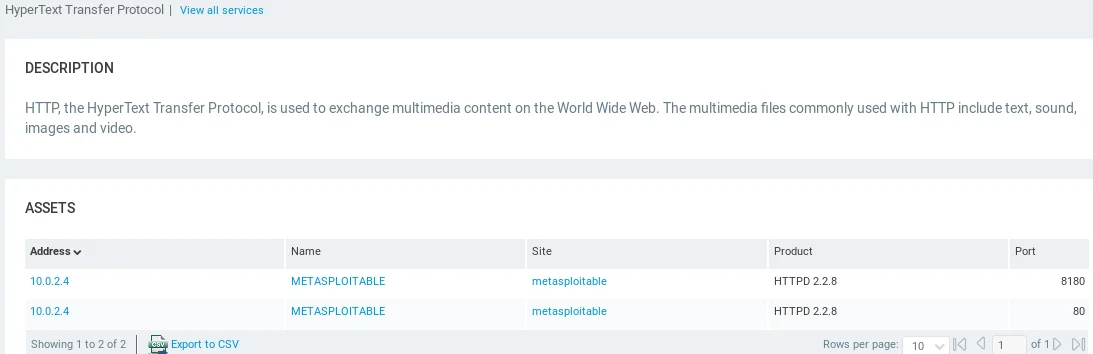
Clicking on any of the listed services will provide additional information about them. For instance, clicking on the HTTP service will display a description of the service as well as the ports on which it is running. The provided screenshot shows that HTTP is running on both port 80 and port 8180.
To examine the vulnerabilities in more detail, we can navigate to the Vulnerabilities page by scrolling up.
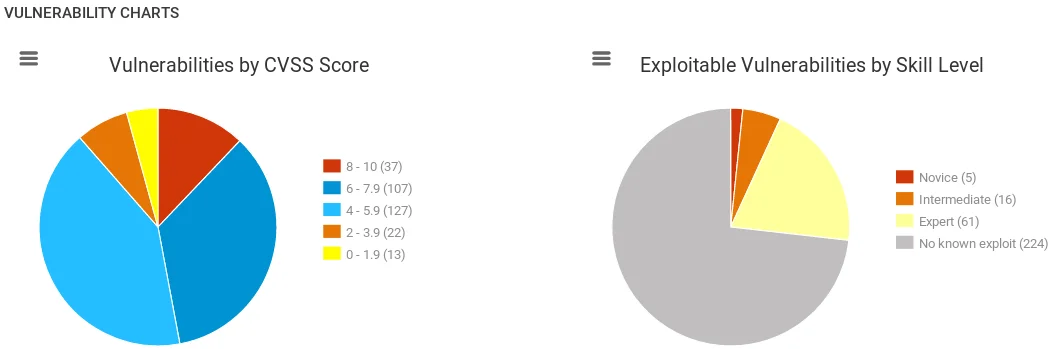
The screenshot above displays a graph that categorizes vulnerabilities based on their risk level and the level of skill required to exploit them. On the left side of the graph, vulnerabilities are sorted by their risk level, while on the right side they are sorted based on the skill level needed to exploit them. Further down the page, a comprehensive list of all vulnerabilities can be viewed and navigated using the arrow buttons.
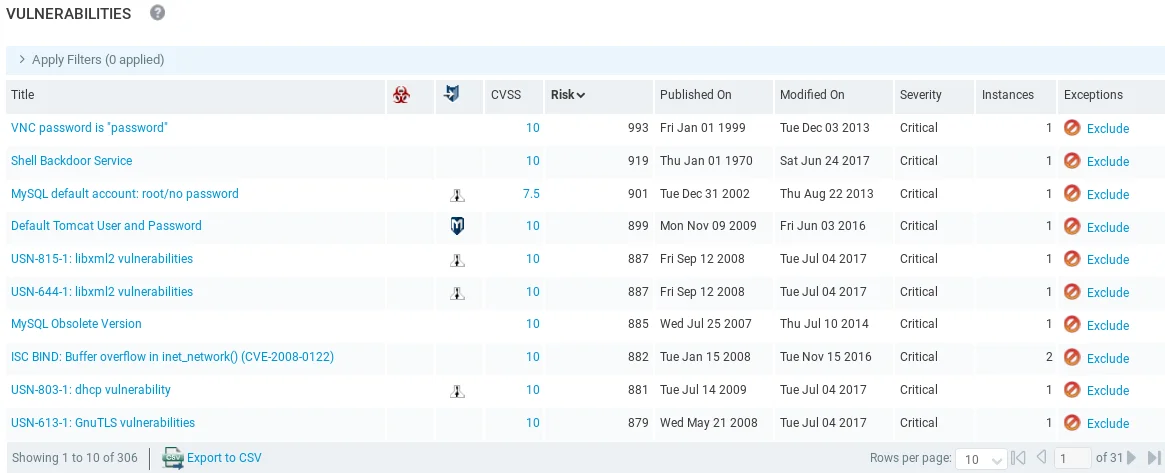
The vulnerabilities listed at the top are ordered by risk, and although they don’t have exploitation using a tool, we can still see if there is exploitation under the exploit icon or if there is any malware under the malware icon.
From the screenshot, it is evident that the VNC password has been found to be “password,” and we can attempt to connect to the target computer through the VNC service. This service is analogous to Remote Desktop as it provides complete access to the computer’s desktop. Moreover, we have already used the backdoor Shell Backdoor Service that is currently running.
Next, we will explore potentially exploitable vulnerabilities by clicking on the exploit icon, and we can observe that all of them are marked with an M logo, indicating that they can be exploited using Metasploit.
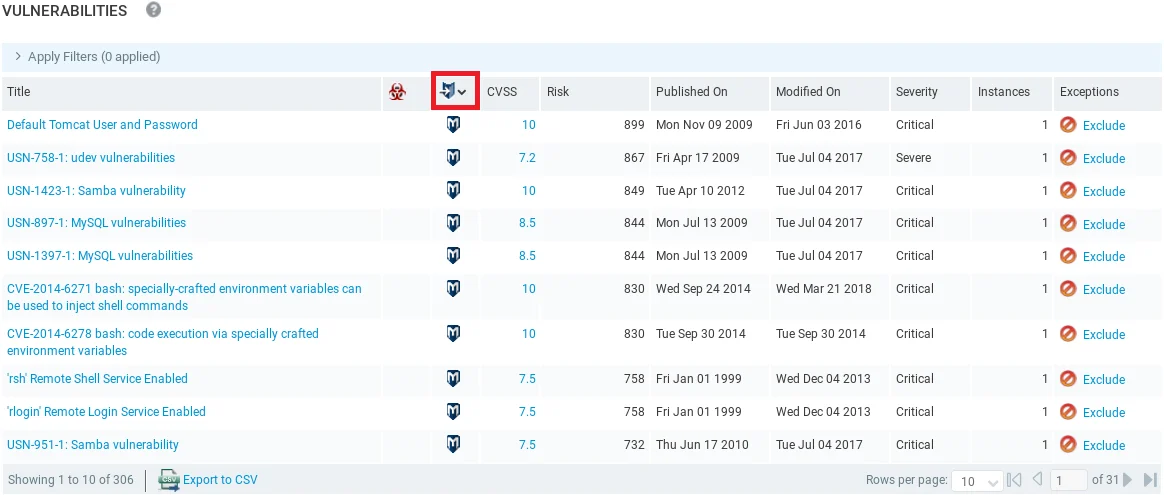
The above screenshot displays the description of the Default Tomcat User and Password vulnerability that we have not previously explored, while in the previous screenshot we had seen the Remote Shell Service and Remote Login Service vulnerabilities that were already discussed.
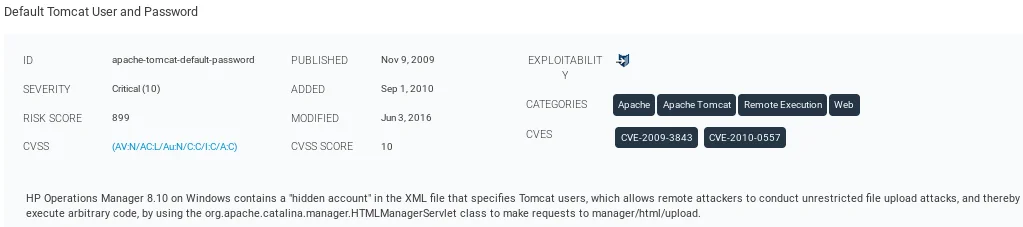
The subsequent screenshot displays the active port, which is 8180, and it also provides an explanation as to why the system is considered to be susceptible to this particular exploit.
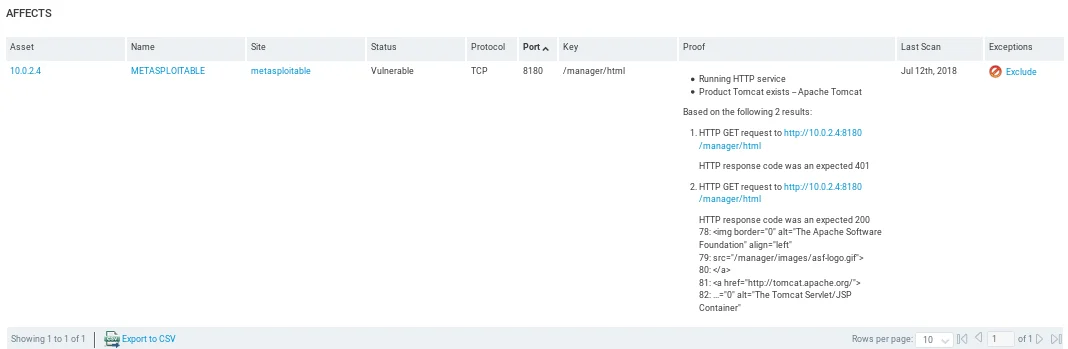
Upon scrolling down, the vulnerability details page provides us with information on how to exploit the vulnerability.
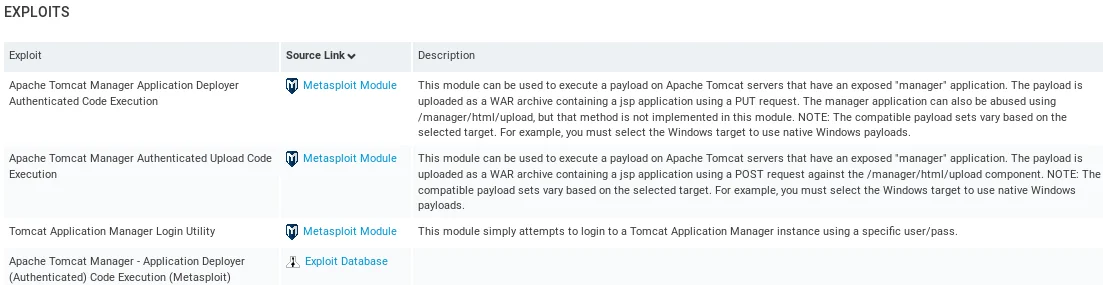
The screenshot shows three modules that are associated with the vulnerability, which can be used to verify its existence or to exploit it. Clicking on any of the Exploit links under the Source column will take us to the Rapid7 page that we previously used for searching.
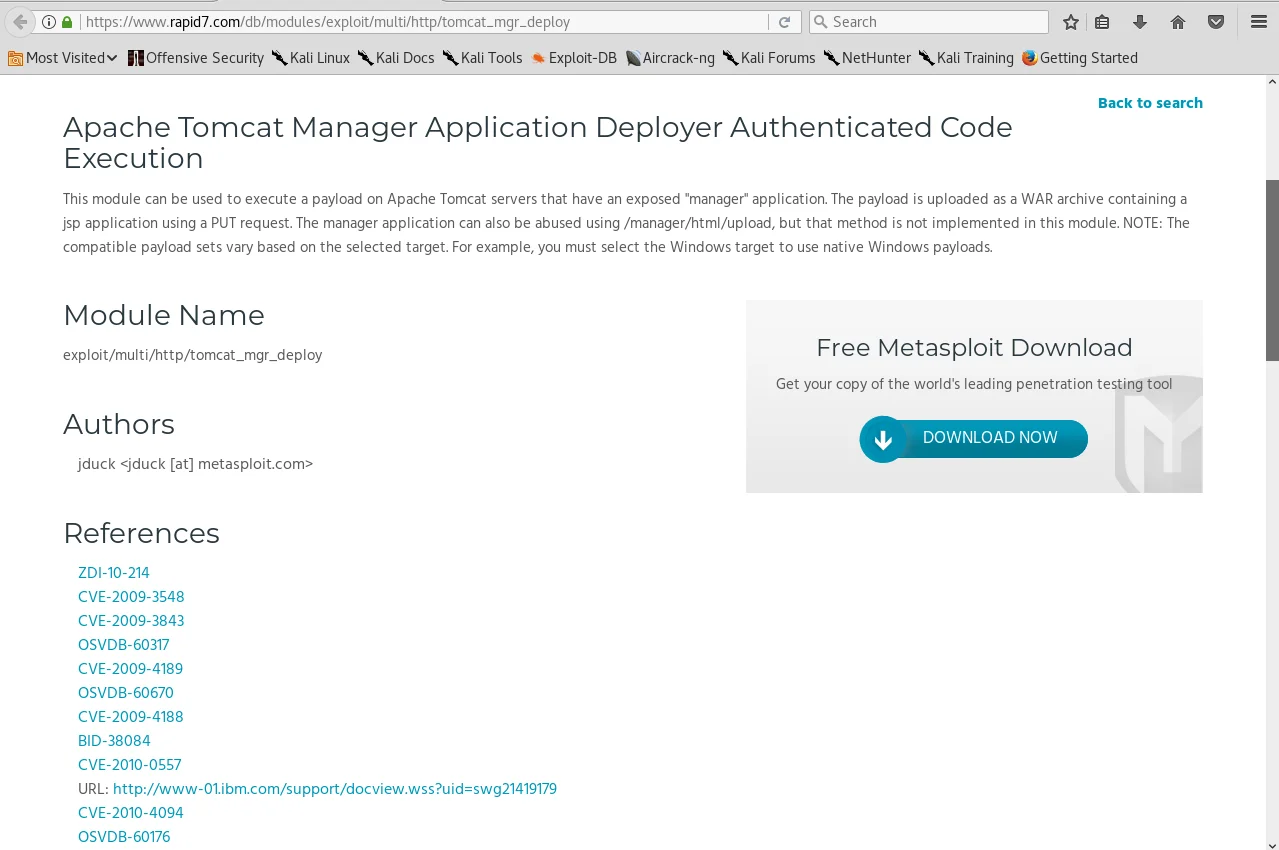
The above image showcases the name of the module, which can be effortlessly copied and pasted into Metasploit, followed by running “show options” and then executing it similarly to the way we did in the Metasploit basics section. Additionally, by scrolling down, we can also view the REFERENCES for this specific exploit.
The bottom of the page provides us with the REMEDIATIONS section, which outlines how to fix the exploit.
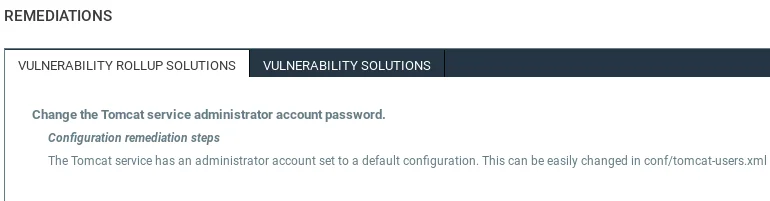
The remediation for this vulnerability involves changing the administrator password and avoiding the use of default configurations.
We will now proceed to the Reports tab to produce reports for each scan that we perform.
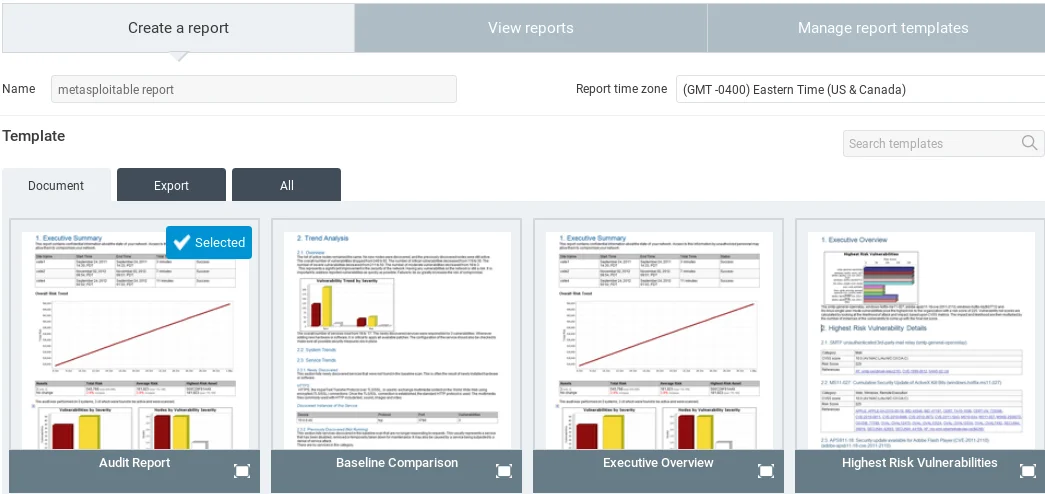
The screenshot displays three types of report templates available: Audit Report with detailed information for programmers, Executive Report with less information suitable for managers, and Simple Report. Any of these templates can be selected and named according to user preference. In this example, the report is named “Metasploitable Report.” Underneath the template selection, users can choose the desired format for the report.
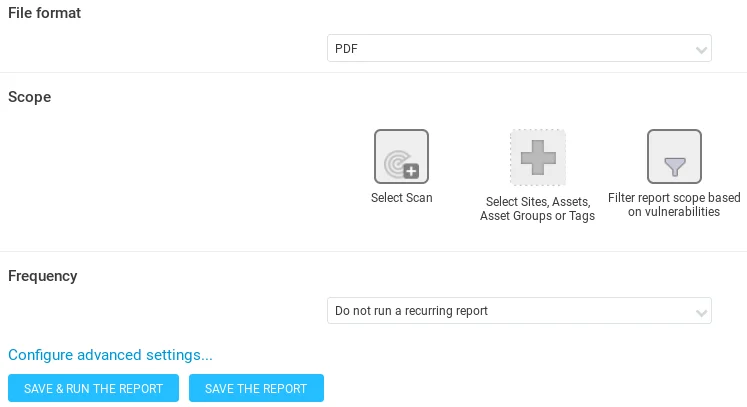
In the previous screenshot, the format for the report has been set to PDF. To generate a report, we need to click on the “Select Scan” option, then select the desired scan for which we want to generate a report, and finally select “metasploitable.”
Click on SAVE & RUN THE REPORT to generate the report.
It is also possible to set up an automatic report generation to coincide with each scan. For instance, if we perform a scan every week, we can configure a weekly report to be generated automatically. After generating a report, we can download it by clicking on the report and take a look at its contents.
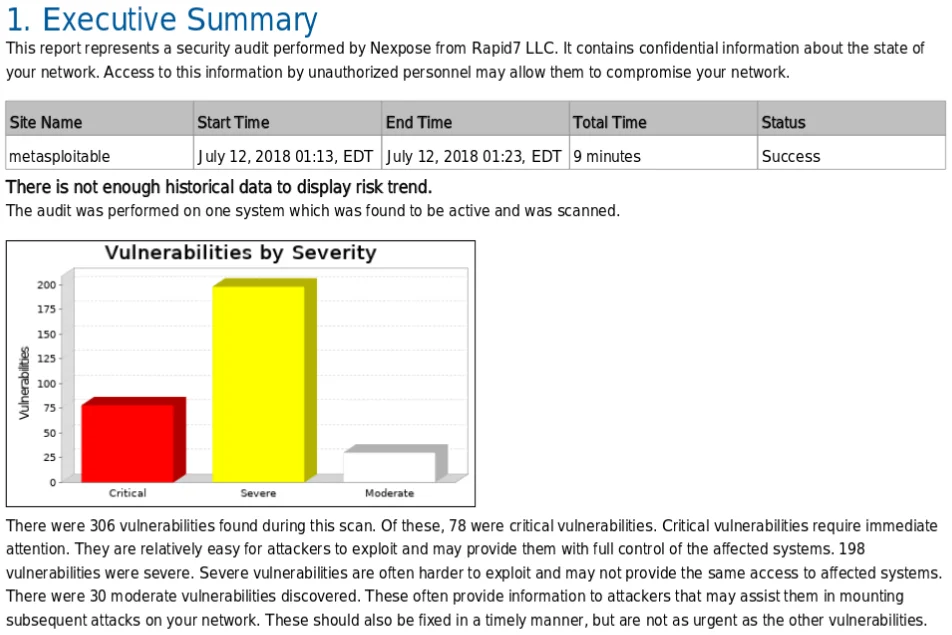
The screenshot above displays an executive report which includes the date, report title, and a summary of the discovered exploits. It contains less technical details and more graphical representations of the risks found, making it suitable for executives to understand the criticality of the vulnerabilities.
The preceding screenshot highlights that Nexpose is significantly more advanced and provides a greater amount of detail. It is intended for larger companies with extensive infrastructure, where it is crucial to ensure that all software is up-to-date, installed correctly, and there are no vulnerabilities that can be exploited.
To know more about Nexpose Analysis, make sure that you follow us @ tutorials.freshersnow.com.
