“Creating Wordlist” To generate a wordlist that we can use to crack the WPA key from the captured handshake, we need to utilize a tool known as “crunch.” Essentially, a wordlist is a compilation of words that aircrack-ng will attempt to match against the handshake until it succeeds in finding the correct WPA key. The effectiveness of the wordlist determines the likelihood of cracking the WPA key. It is important to note that if the password is not in our wordlist, we will not be able to determine the WPA key.
Using the crunch tool, we can create a custom wordlist that will contain a comprehensive range of potential passwords. The syntax for using crunch involves inputting specific parameters such as the minimum and maximum length of the words, character sets to use, and any specific patterns or rules to follow. Once the crunch tool generates the wordlist, we can then feed it into aircrack-ng to begin the process of attempting to crack the WPA key.
crunch [min] [max] [characters] -o [FileName]
or
crunch [min] [max] [characters] -t [pattern] -o [FileName]
where
- crunch is the name of the tool.
- [min] specifies the minimum number of characters for the password to be generated.
- [max] specifies the maximum number of characters for the password.
- -t is optional. It specifies the pattern.
- -o option specifies the filename where the passwords are going to be stored.
- The “characters” parameter is used to indicate the specific set of characters that we want to include in the password for our wordlist. This can encompass a variety of options such as lowercase and uppercase letters, numbers, and symbols. By specifying the desired character sets, we can create a wordlist that includes all possible combinations of these characters within the defined length parameters. This allows for a more comprehensive and targeted approach to cracking the WPA key, increasing the chances of success.
The “-t” option in crunch is particularly useful when we have prior knowledge about a part of the password that we’re trying to guess. For example, if we have observed someone entering their password and we know that it begins with the letter “a” and ends with the letter “b”, we can utilize the “pattern” option in crunch to create a wordlist that specifically generates passwords that follow this pattern. By incorporating all possible combinations of characters within the specified parameters, we can optimize the wordlist to target a more focused set of potential passwords, increasing the chances of successfully cracking the WPA key.
To generate a custom wordlist using crunch, we will specify a minimum length of 6 and a maximum length of 8 characters. In addition, we will use the “12ab” character set to create all possible combinations of passwords within this length range. These generated passwords will be stored in a file named “test.txt”. The command for this process would be formulated as follows:
![]()
The below output will be shown on executing the command:
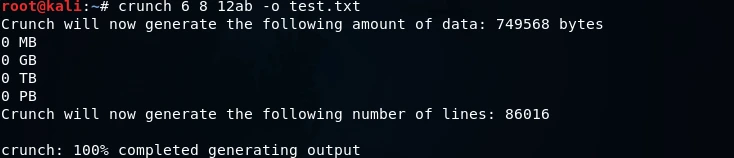
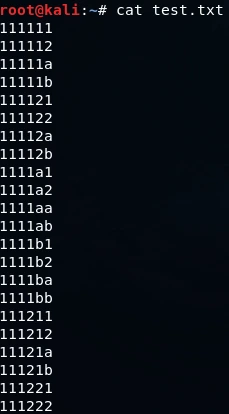
By utilizing the “cat test.txt” command, we can display all of the passwords that have been generated and stored in the “test.txt” file. The contents of this file will be output in the command line interface, allowing us to visually inspect the list of generated passwords. The provided screenshot displays an example of what this output may look like.
To utilize the “pattern” option in crunch, we will first set a password length range of a minimum of 5 characters and a maximum of 5 characters. Next, we will specify a character set consisting of “abc12”. Then, we will add the “-t” option and input the pattern “a@@@b”. This will generate all possible password combinations that begin with the letter “a” and end with the letter “b”, with any combination of characters in between. The final step will be to specify the output file using the “-o” option and naming it “sample.txt”. The command for this process would be constructed as follows:
![]()
Below is the output:
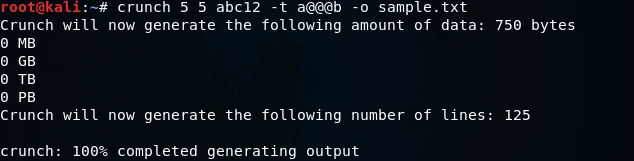
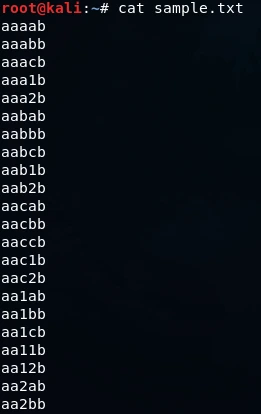
After generating the passwords using the command provided, a total of 125 possible combinations were generated, all of which consist of five characters and begin with the letter “a” and end with the letter “b”. The output of these generated passwords can be displayed by utilizing the “cat sample.txt” command in the command line interface. The accompanying screenshot shows an example of this output, demonstrating that all passwords indeed follow the specified pattern.
By utilizing the crunch tool, we can generate a custom wordlist that will be utilized in the next step of the process. The generated wordlist, along with the captured handshake file, will be used to attempt to determine the actual WPA key through the process of cracking.
We hope that this article has provided you with ample information regarding the process of creating a wordlist. If you are interested in learning more about the field of ethical hacking, we encourage you to follow our daily updates @ tutorials.freshersnow.com for further insights and resources.
