“Capturing the handshake” To obtain the WPA key, the first step is to capture the handshake, which can be done by using airodump-ng. This process is similar to how it is done for WEP-encrypted networks. By executing the command, all the networks in the vicinity can be captured.
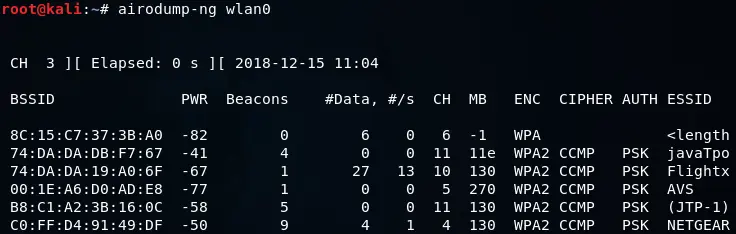
Next, we will execute airodump-ng command to target the network by specifying the –bssid as 74:DA:DA:DB:F7:67, along with the channel number 11 using the –channel option. Additionally, we will include the –write option to save all captured packets to a file named wpa_handshake, and finally, we will set the wireless card to monitor mode by specifying it as wlan0. The complete command would look like this:
![]()
After running this command, we will be able to capture packets from the WPA-encrypted javaTpoint network along with information about the clients connected to the network.
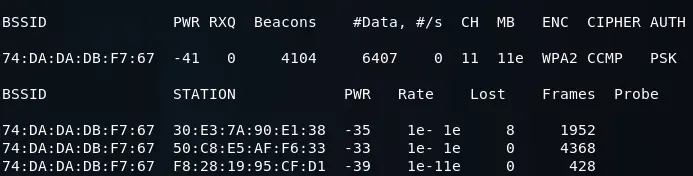
There are two methods to capture the WPA handshake. The first method involves waiting for a device to connect to the network and then capturing the handshake. The second method involves using a deauthentication attack, which we previously discussed in the Pre-connection attacks section, to force connected devices to disconnect and then capturing the handshake when they reconnect.
A deauthentication attack can be used to forcibly disconnect any device within the range of our Wi-Fi network. By executing this attack for a brief period, we can cause a device to be disconnected from the network for a few seconds, during which it will automatically attempt to reconnect. This reconnection process is typically unnoticed by the device user. By intercepting the connection attempt, we can capture the handshake packets that are sent whenever a device connects to a target network.
To execute a basic authentication attack using aireplay-ng, we first use the command “aireplay-ng –deauth” followed by the name of the attack and the number of authentication packets (4 in this case) to send to the AP in order to disconnect the targeted device from it. Next, we specify the MAC address of the target AP using the -a option, and the MAC address of the client device we want to disconnect using the -c option. Finally, we add the name of the Wi-Fi card being used, which in this case is wlan0.
![]()
In the accompanying screenshot, it is evident that we have successfully captured the WPA handshake without any indication of disconnection or change in the targeted device.
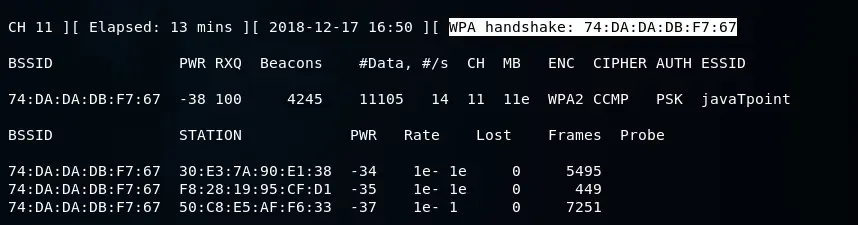
Since the disconnection caused by the deauthentication attack was very brief, there was no indication or alert of the disconnection, making it unlikely for the device user to have noticed it. This allowed us to successfully capture the WPA handshake. To determine the WPA key, we can use a wordlist and apply it against the captured handshake.
We believe that the information provided here on Handshake Capturing has been useful to you. If you are interested in gaining further knowledge on Ethical Hacking, we invite you to follow us @ tutorials.freshersnow.com for more information.
