This section will focus on subdomains, which are commonly found in URLs, such as subdomain.target.com. Subdomains are frequently used by websites for specific groups of users or customers, such as beta.facebook.com or mobile.facebook.com. They are often not visible on search engines or advertised, making them a potential target for hackers seeking to exploit vulnerabilities in these subdomains. Additionally, large websites often use subdomains for testing and development purposes, such as beta.facebook.com, which may contain experimental features that have not yet been implemented on the main site. Subdomains may have more vulnerabilities than the main website, making them attractive targets for hacking attempts. In this section, we will explore methods for discovering subdomains, both advertised and hidden, to gain insights into our target.
We will be utilizing a tool called “knock” to aid us in this section. This tool is user-friendly and does not require any installation. We simply need to download it by running a git command that includes the tool’s URL, as follows: “git clone [URL of tool].”
![]()
After the download is complete, we will utilize the “cd” command to navigate the downloaded directory, where we will then be able to view the presence of a “.py” file, as demonstrated in the following example:
To execute the file, we will use the command “python knockpy.py” and then input the website for which we seek to obtain the subdomains, in this case, “isecur1ty.org“. Therefore, the complete command will be as follows: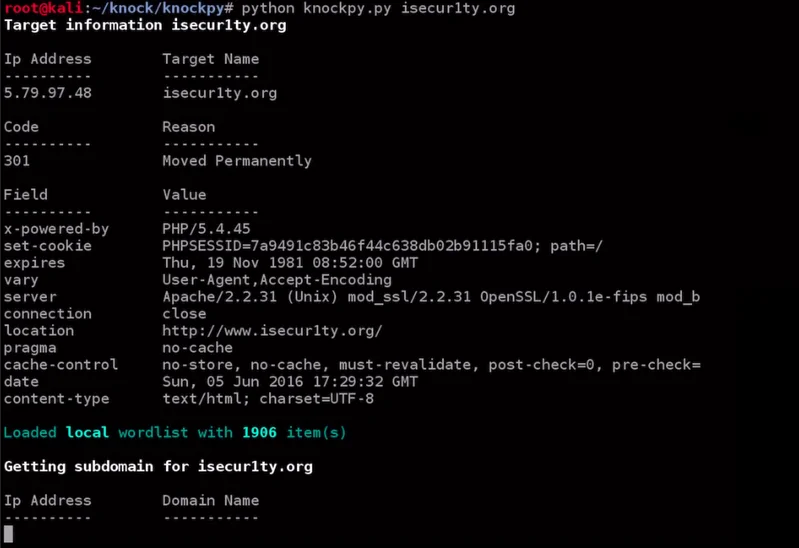
After performing a brute-force and Google-based subdomain search using the Knock tool for isecur1ty, it will display any subdomains associated with isecur1ty that we can test the security of and explore what is installed on them. We may also be able to gain access to the website through these subdomains. The tool will show the results of the scan, and in the screenshot provided, it appears that seven subdomains were found that were not advertised.
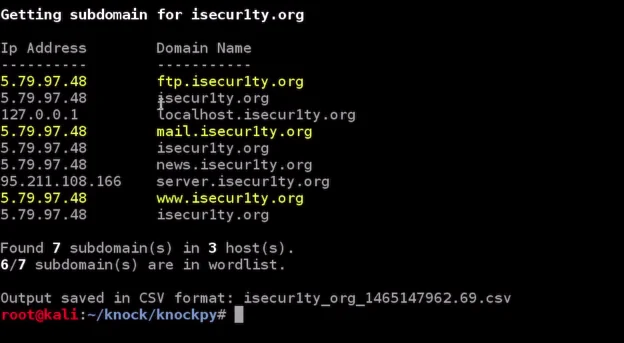
In the list of subdomains found by the knock tool, we discovered interesting subdomains such as ftp.isecur1ty.org, localhost.isecur1ty.org, mail.isecur1ty.org, and news.isecur1ty.org. The latter was especially noteworthy because it contained a beta version of a script that was still under development. If a hacker discovered this subdomain, they would have had a high chance of finding a vulnerability in the script and gaining access to the entire website.
The aforementioned process emphasizes the significance of information gathering, as it can assist in acquiring access to websites. Neglecting this phase may result in missing out on critical details such as a comprehensive script with a plethora of vulnerabilities or essential login pages such as an admin login or an employee login page.
We hope the information shared about Discovering Subdomain has been helpful. For more insights on ethical hacking, we encourage you to follow us daily @ tutorials.freshersnow.com.
