As a result of the successful fake authentication attack, the target access point will now accept packets that we send to it. This paves the way for packet injection attacks, which will enable us to increase the amount of data and ultimately crack the WEP key.
One of the methods of packet injection is ARP request replay. This method involves capturing an AP packet and then injecting it back into the traffic, which will force the AP to generate a new packet with fresh IVs. We can then capture the new packets, inject them back into the traffic, and repeat the process until we have enough data to crack the WEP key. By employing this method, we can significantly increase the amount of data available for analysis and enhance our chances of successfully cracking the WEP key.
Launch airodump-ng using the following command:
![]()
To store all the captured packets into a file named arp-request-reply-test, we will include the “–write” command in our command line. Once executed, we will observe that the target network has zero data, no associated clients, and no traffic, rendering it useless as we cannot crack its key.
To resolve the issue, we will execute a fake authentication attack, as described in the Fake Authentication section. This will enable us to inject packets into the target network, which will then be accepted. The next step is the ARP request reply phase, where we will inject packets into the network, triggering the creation of new packets with new IVs. The following command will be utilized to accomplish this task:
![]()
The subsequent command is analogous to the previous one, except that it employs “–arpreplay” instead of “–fakeauth,” and includes “-b” for BSSID. By executing this command, we wait for an ARP packet, capture it, and reinject it into the air. This process continues as we capture and reinject subsequent ARP packets, and as a result, the AP generates new packets with new IVs. We repeat this process repeatedly, causing the AP to generate a continuous stream of new packets with different IVs. Upon completion of this command, the following output will be displayed:
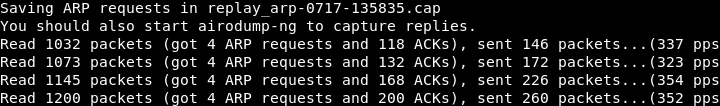
The wireless adapter, “wlan0,” is currently waiting for an ARP packet. Upon receiving an ARP packet transmission in the network, the adapter captures and retransmits the packet. This process forces the access point to generate a new packet with a new IV, which we continue to capture and retransmit. Once the data reaches 9000 or more, we can use the “aircrack-ng” tool to crack it by executing the following command:
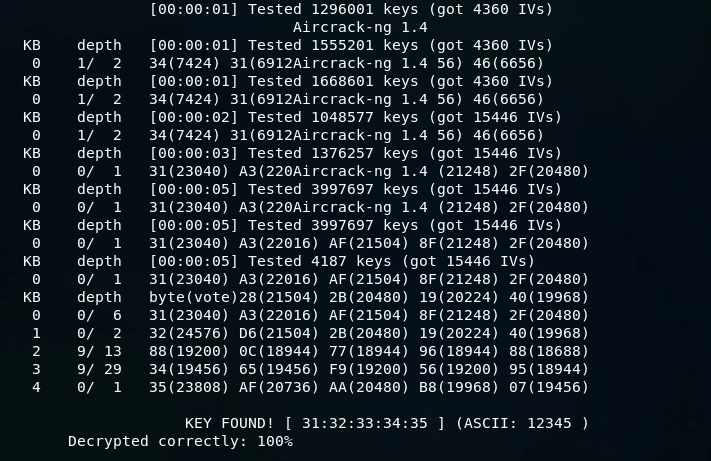
![]()
Upon executing the aforementioned command, the output will display the cracked WEP key, indicating that we have successfully compromised the security of the target wireless network.
To stay informed regarding the details such as the ARP Request Replay Attack, please visit our website frequently @ tutorials.freshersnow.com.
