The image depicts the outcome of using the dirb tool, which has successfully detected various files. While some of these files were already familiar to us, the tool has unearthed several additional ones.
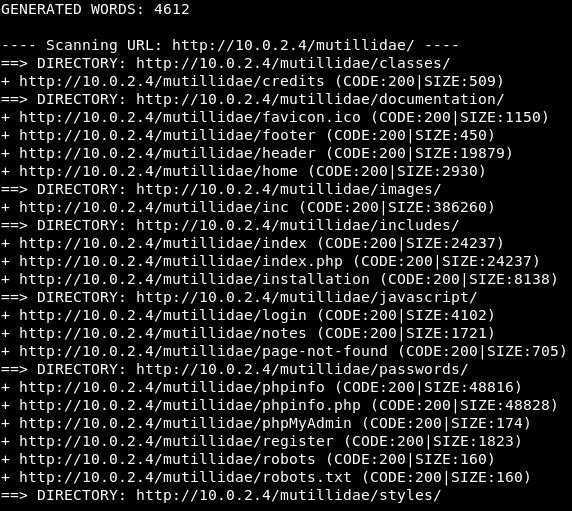
Based on the displayed screenshot, it is evident that favicon.ico is an icon file, while index.php functions as the main index page. Furthermore, the footer and header files are presumably utilized for styling the page. Moreover, our examination has revealed the presence of a login page.
If we manage to exploit a complex vulnerability to obtain the target’s username and password, we may face the challenge of locating the login page on the website. In such situations, tools like dirb can come in handy. One file that can provide valuable information is the phpinfo.php file, which displays a comprehensive overview of the PHP interpreter running on the web server. The screenshot reveals that this file contains a wealth of information.
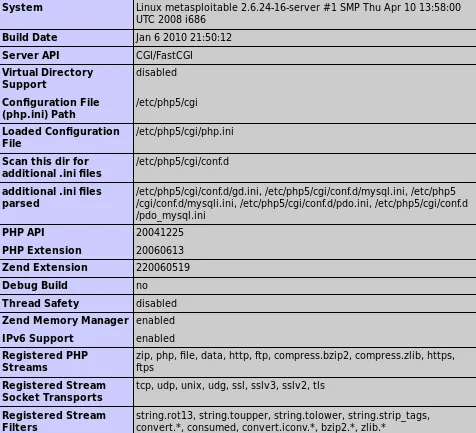
The preceding details are of great significance as they aid in familiarizing ourselves with several directories. By analyzing the provided screenshot, we can determine that the system is currently utilizing php5. Additionally, we can deduce that the configuration is saved in the .cg1 file, while .ini files are conventionally deployed as configuration files for PHP. Armed with this information, we can efficiently locate all the storage locations for such files.
Upon further scrolling, we will come across data pertaining to the system’s installed permissions. Moreover, it is apparent that MySQL has been installed, indicating that the system is currently leveraging MySQL.
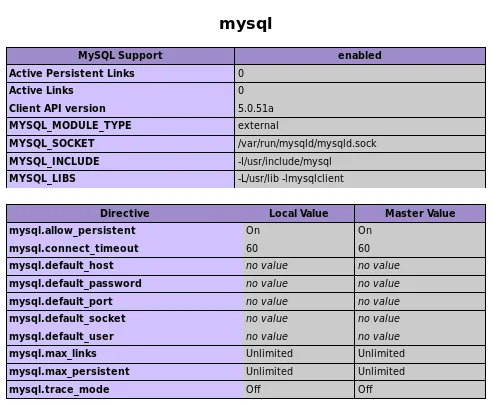
The provided screenshot contains valuable information regarding the storage locations of different types of configurations. Furthermore, it presents the modules and extensions that PHP is currently employing, thereby establishing the significance of the phpinfo.php file. In the following screenshot, we have accomplished the task of locating the phpMyAdmin login, which serves as the gateway for accessing the database.
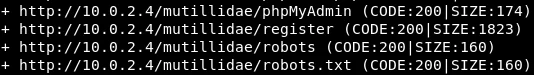
The robots.txt file is a crucial document that imparts instructions to search engines, outlining how the website should be handled. It typically features a list of files that ought not to be indexed or visible to the public. Hence, if we gain access to the robots.txt file, we can potentially unearth the information that the website administrator is striving to hide. Based on the displayed screenshot, we can conclude that the administrator has prohibited Google and us from accessing the “passwords” directory and “config.inc” file, alongside several other files.
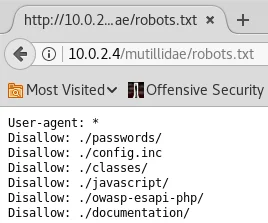
In the subsequent screenshot, we will examine the information contained in the ./passwords and ./config.inc files.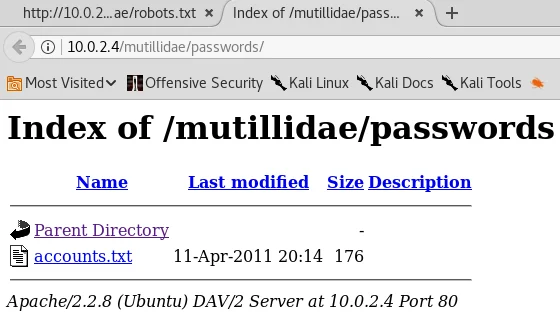
The displayed screenshot demonstrates the presence of an “accounts.txt” file that contains a series of usernames and corresponding passwords. By examining its contents, we can determine that an “admin” user with the password “adminpass” has been created. Furthermore, we have discovered the password for the “adrian” user, which is “somepassword.” In the following screenshot, we have achieved the task of uncovering several usernames and passwords.
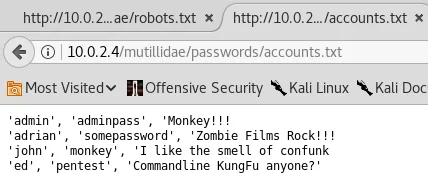
While the actual usage of the discovered usernames and passwords remains unclear, we have nevertheless retrieved valuable data. The config.inc file is yet another significant document that provides vital information. As shown in the given screenshot, it includes essential details required to establish a database connection, such as parameters $dbhost, $dbuser, $dbpass, and $dbname.
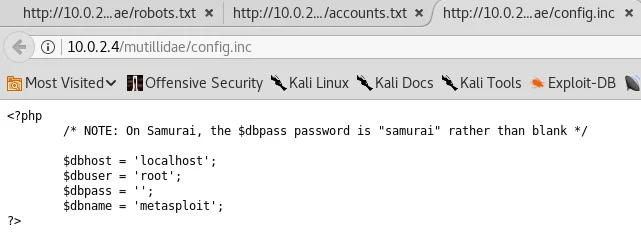
Based on the displayed screenshot, we can observe that the login credentials for the database include a username “root” and a blank password. With this information at hand, we can proceed to use the commands illustrated in the preceding screenshot to initiate a connection to the database. If the connection is successful, we should be able to access the database.
While the purpose of the obtained login credentials is unclear, we can add them to a list to attempt logging into the admin account, or store them in a list for future use in case of a brute-force attack.
If you wish to acquire additional information related to Ethical Hacking, such as Analyzing and Discovering Files, please follow us @ tutorials.freshersnow.com.
