In this section, we will explore the two distinct approaches for attacking websites:
- The techniques for attacking a website that we have acquired can be applied. Since a website is installed on a computer, we can attempt to hack it using the same methods employed for any other computer. Server-side attacks can also be utilized to determine the operating system, web server, or other applications that are installed. If any vulnerabilities are discovered, they can be exploited to gain access to the computer.
- Client-side attacks present another method of infiltration. As websites are maintained and operated by human administrators, exploiting vulnerabilities in their systems can lead to acquiring their login credentials. With these credentials, access can be obtained to the admin panel or the Secure Socket Shell (SSH), which in turn can provide entry to the servers used to manage the website.
If the preceding approaches are unsuccessful, one may attempt to test the web application, as it is essentially an installed application on the website. In this case, the primary target may not be the web application itself, but rather a person who is utilizing the website on a computer that is inaccessible. Thus, it may be possible to penetrate the website, and subsequently reach the desired target through this alternate means.
Given that all devices and applications are interconnected, we can leverage one to gain an advantage and then navigate to another computer or location. In this segment, we will not be concentrating on client-side or server-side attacks; rather, we will be exploring techniques for testing the security of web applications themselves.
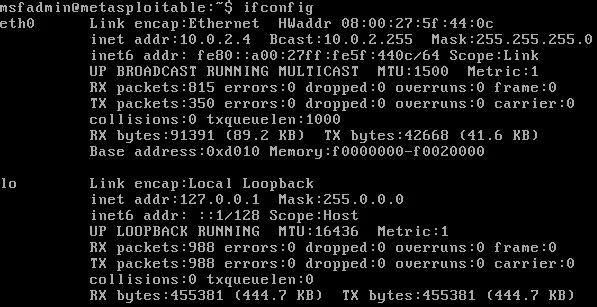
If we select the Metasploitable machine as our target, running the “ifconfig” command will reveal its IP address as 10.0.2.4, which is depicted in the screenshot provided.
By examining the /var/www directory, it is possible to observe all of the website’s stored files, as depicted in the accompanying screenshot:
![]()
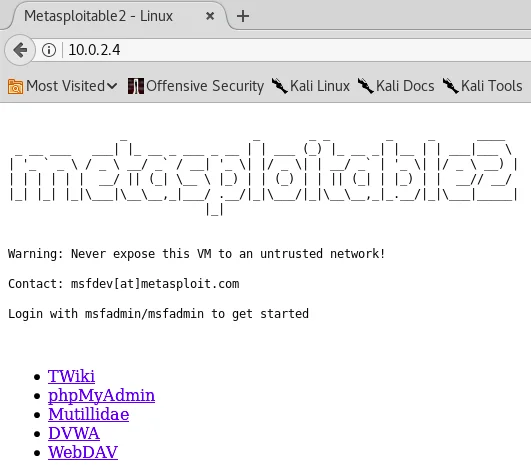
The screenshot displays a phpinfo.php page, along with dvwa, mutillidae, and phpMyAdmin. If we access any computer on the same network and open a web browser, we can enter the IP address of 10.0.2.4 to access the Metasploitable website, as depicted in the provided screenshot. A website is essentially an application installed on a web server, and any of the Metasploitable websites can be accessed and used to evaluate their security.
To access the DVWA page, we need to enter the login credentials of “admin” for the username and “password” for the password. Upon successfully entering these credentials, we are granted access, as demonstrated in the accompanying screenshot.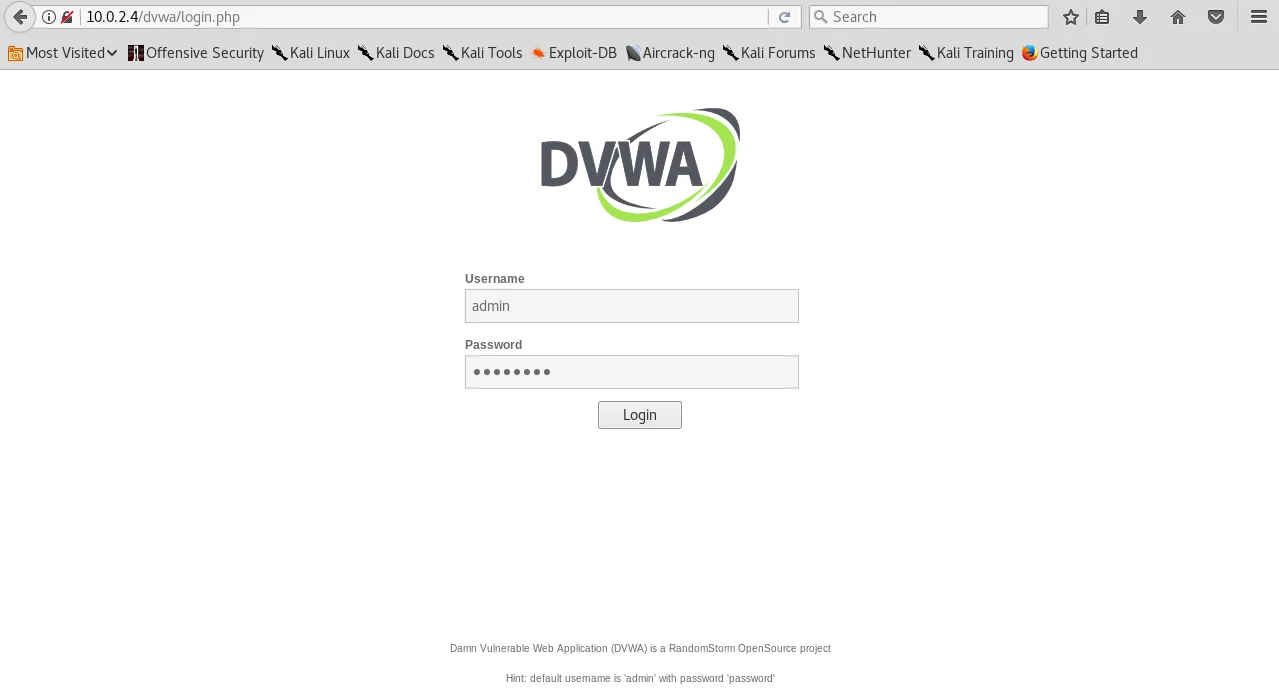
After successfully logging in, the security settings can be modified through the DVWA Security tab, as illustrated in the following screenshot:
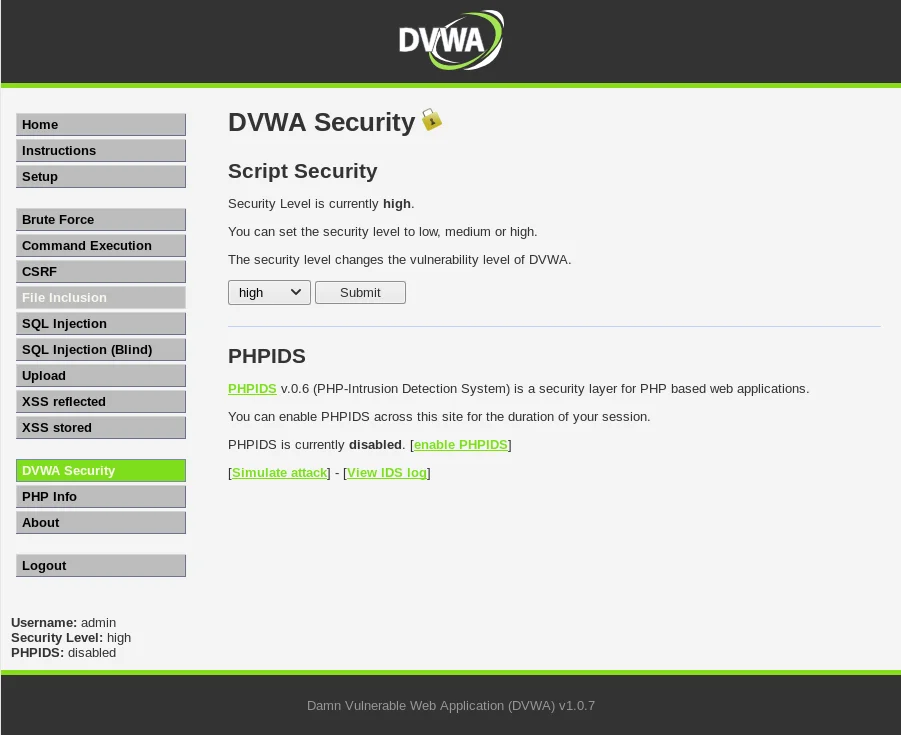
Navigate to the Security tab within DVWA and adjust the Script Security setting to “b” before submitting the changes.
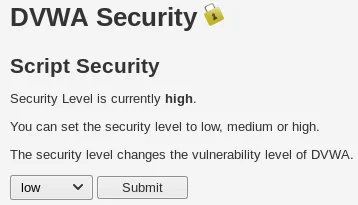
For the upcoming section, we will maintain the Script Security setting on “low.” Given that this is an introductory course, we will only cover the fundamental methods for identifying web application vulnerabilities in both DVWA and the Mutilliidae web application.
To access the Mutillidae web application using the same method employed to reach the DVWA web application, it is imperative to verify that the Security Level is set to 0, as demonstrated in the accompanying screenshot:
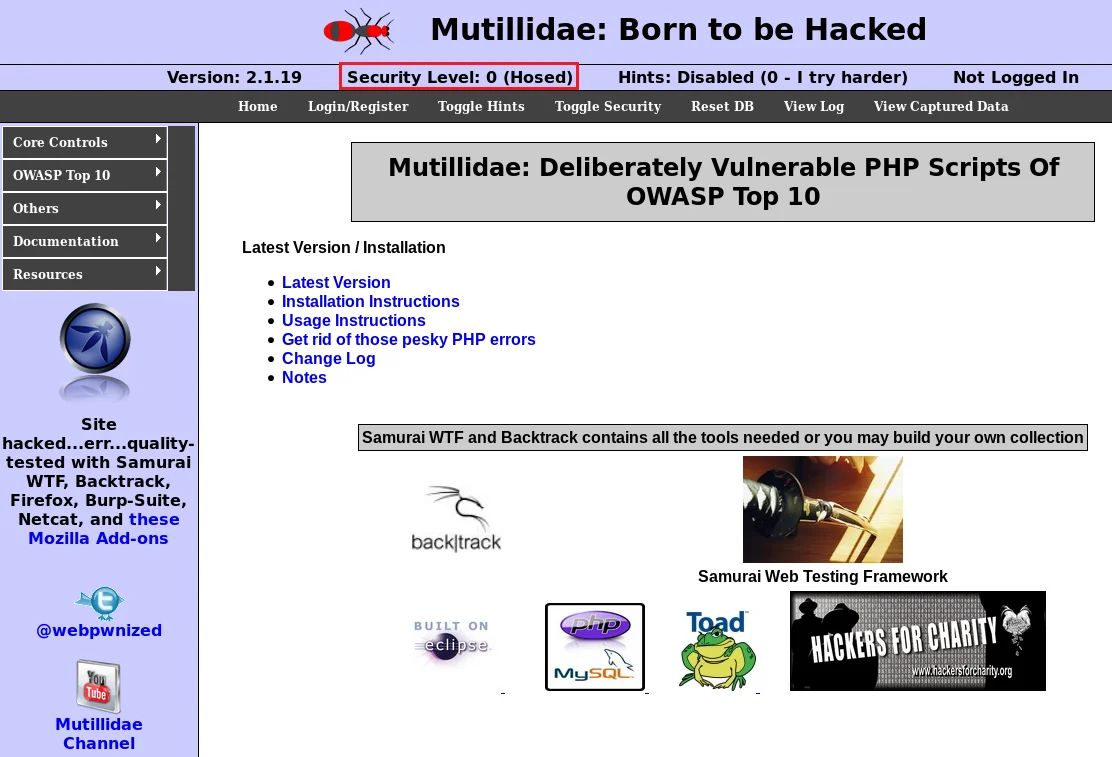
By selecting the Toggle Security option on the page, it is possible to alternate the Security Level.
For additional knowledge and a more comprehensive understanding of Attacking a Website in Ethical Hacking, we recommend following our website @ tutorials.freshersnow.com on a daily basis.
