The screenshot given displays the web interface of Metasploit community, and we can log in using the username and password set during the installation process.
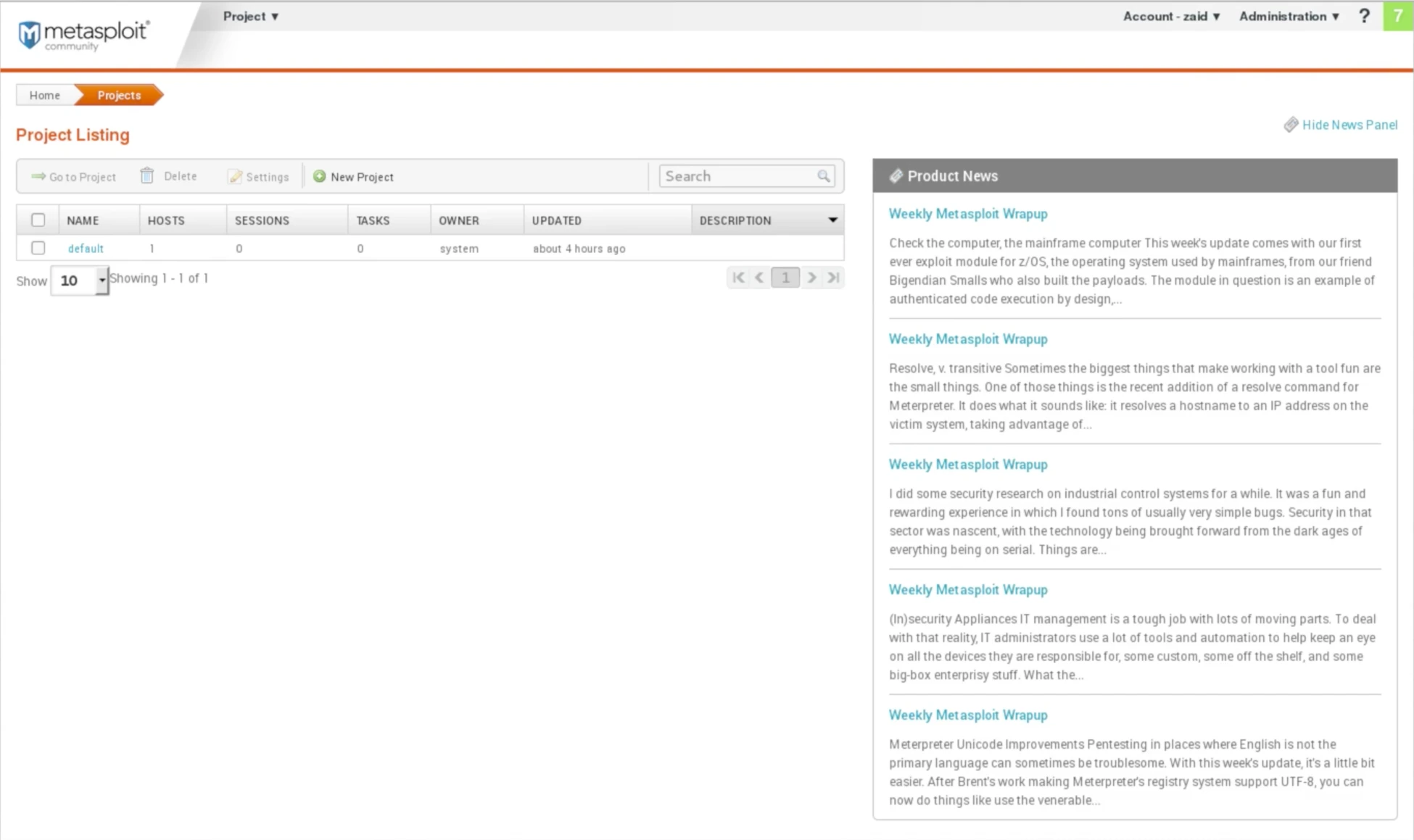
After logging in, we can access our account and navigate to user settings or log out, as well as check for software updates.
Upon the first login, the tool will prompt us to enter the activation key which will be sent to the email address we provided during the download. It is important to ensure that the email address we entered is valid.
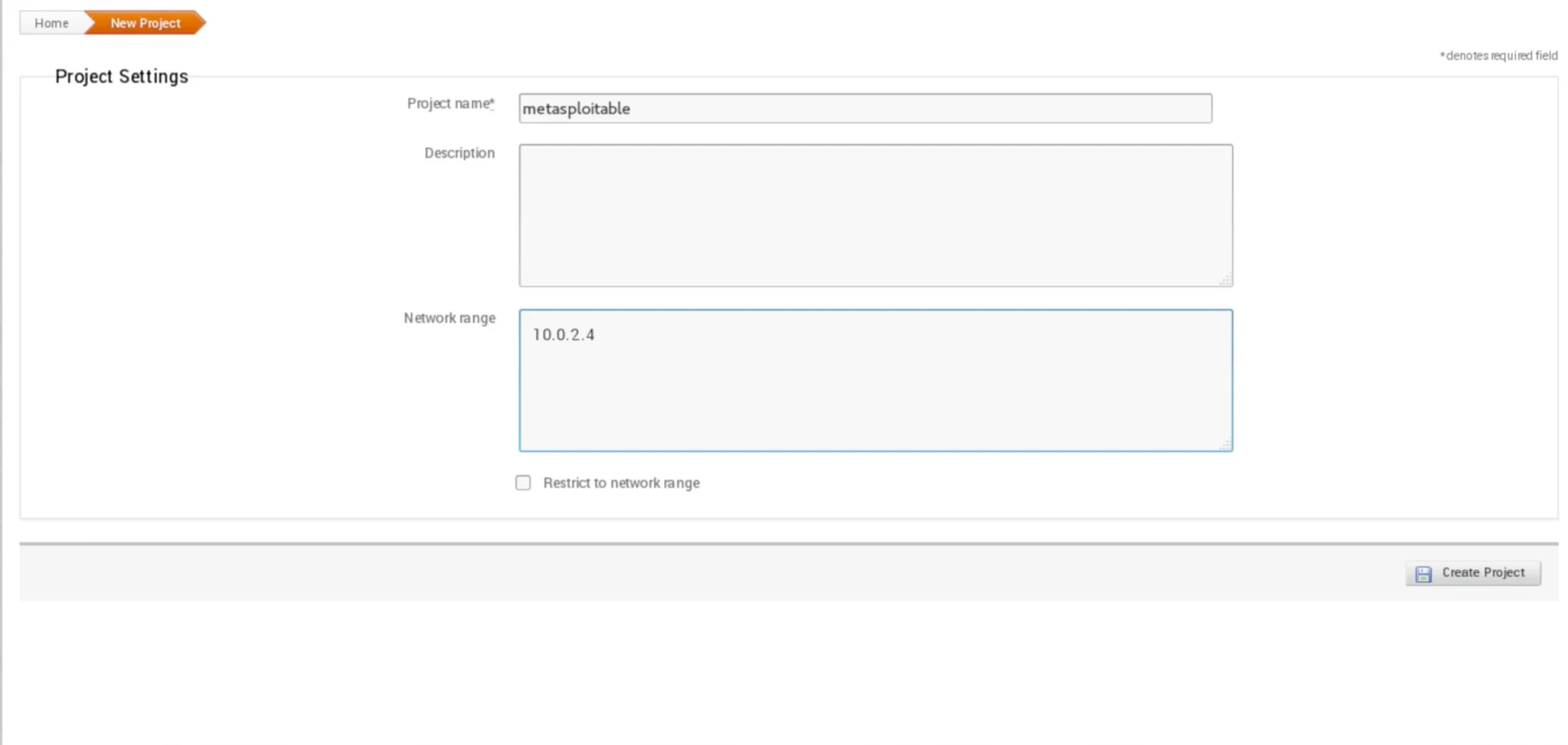
To begin a scan, we can create a new project by clicking on Project and selecting New Project. For the project name, we will use “metasploitable” and leave the Description field blank. The Network range can be set to the same range we used with Zenmap, which is 10.0.2.1-254. However, for this scan, we will only target 10.0.2.4, which is the IP address of the Metasploitable machine.
The next step is to click on Create Project to confirm the project details, as shown in the screenshot above, where we have set the project name as “metasploitable,” left the description empty, and specified the target network range as 10.0.2.4.
To start a scan on the created project, we need to click on the Scan button located on the left side of the screen. Before launching the scan, we can set some advanced options by clicking on the Show Advanced Options button. For instance, we can exclude certain IP addresses from the search by specifying them in the exclude-address field. Additionally, we can customize Nmap arguments, add or remove TCP ports, and adjust the scan speed. The tool also offers UDP service discovery to identify installed services on specific ports. Furthermore, we can set up credentials for authentication, but it is not necessary in our case. Lastly, we can assign a tag to the target computer.
The current settings will be left unchanged, and the scan will be initiated without modifying any of them to keep it simple. After the scan completes, we will explore the discovered information and see what actions can be taken.
Thanks for choosing this portal to know about MSFC Scan. To gather useful information regarding Ethical Hacking, do follow us @ tutorials.freshersnow.com.
