In this section, we will focus on server-side attacks, which can be performed without user interaction and can be used against web servers or personal computers. To demonstrate these attacks, we will target our Metasploitable device. The reason for targeting this device is that if we were to target a personal computer that is not on the same network as us, we would only be able to obtain information about the router that the computer is connected to, rather than about the computer itself. This is because the computer’s IP address would be hidden behind the router.
In the case of targeting a web server, we can access it directly on the internet using its IP address. For this attack to work on a personal computer, the person must have a real IP address and be on the same network as us. If we are able to ping the person, we can use all of the information-gathering methods and attacks that we will learn about.
Before proceeding with the attack, we will check the network settings of our Metasploitable device to ensure that it is set to NAT and is on the same network as our Kali machine, which will be used as our attacking machine. By running the command “ifconfig” on the Metasploitable machine, we can view its IP address, as shown in the screenshot below:
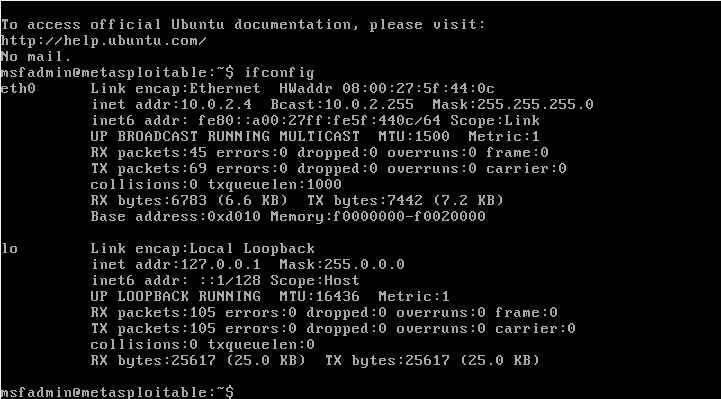
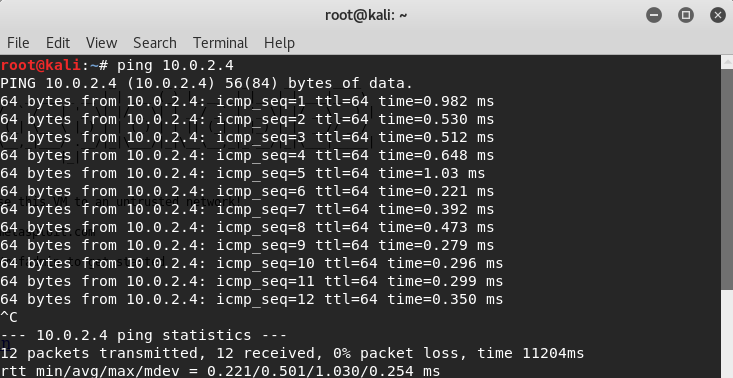
The IP address of the Metasploitable device can be seen in the previous screenshot, and it is 10.0.2.4. After verifying the network settings, we can check if the Kali machine can ping the Metasploitable device, and in the next screenshot, it can be observed that the ping command is receiving responses from the machine. Having established communication with the device, we can proceed to test its security as shown in the subsequent screenshot.
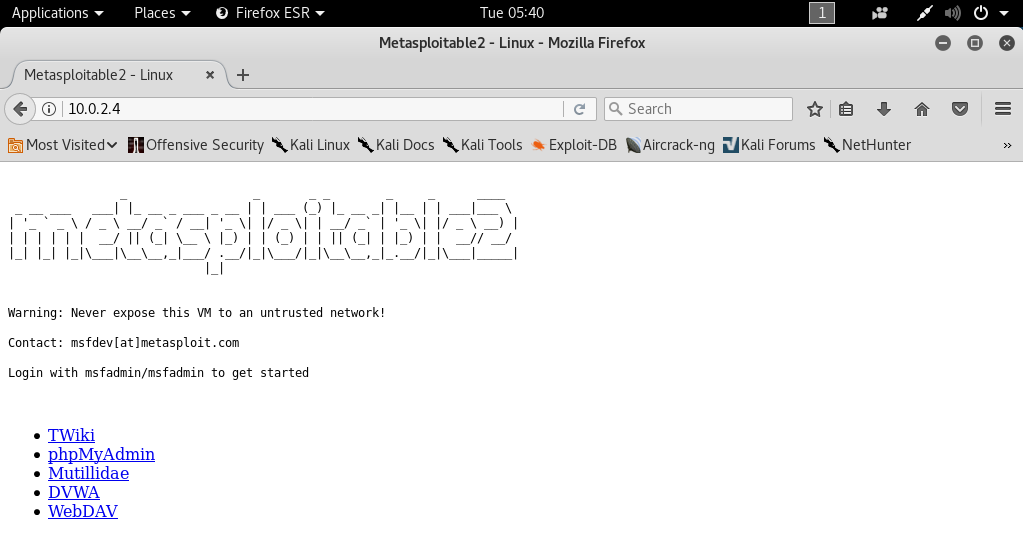
It’s worth noting that these attacks and methods can be used against any computer that can be pinged, including normal computers, web servers, websites, and individuals. To illustrate this, we can look at the Metasploitable machine, which is a virtual machine that can be used for any purpose. By using the -ls command, we can list it and even install a graphical interface, allowing us to use it similar to the Kali machine. The Metasploitable machine also has a web server that hosts websites, which we can browse and examine to perform pen testing in future chapters, as depicted in the screenshot.
Server-side attacks can be applied to any computer that can be pinged, and this includes both servers and personal computers. However, server-side attacks are more effective against servers as they generally have real IP addresses. If we want to target a personal computer, we need to make sure it’s on the same network as ours, and we can ping it to execute these attacks.
We are pleased that you have chosen this page as a resource to learn about Server-Side Attacks. We hope that the information provided here will be beneficial to you. To expand your knowledge on Ethical Hacking, be sure to follow us @ tutorials.freshersnow.com.
