In this segment, we will explore the functionality of a DNS server. DNS, or Domain Name System, is responsible for translating a domain name, such as www.google.com, into the corresponding IP address of the server where the website is hosted. As a MITM, we have the ability to run our own DNS server, enabling us to intercept and manipulate DNS requests. This means that when a user requests to visit a specific website, such as Google.com, we can direct them to a different IP address that we control, resulting in them being redirected to a completely different website than the one they intended to visit. For instance, we can create a fake website and redirect requests from a legitimate domain, such as xyz.com, to our fraudulent site.
In order to execute this attack, our initial step will be to redirect the target users to our local web server, which will be hosted on our Kali machine. We have the flexibility to redirect the user traffic to any destination, but for the purposes of this exercise, we will redirect it to our local web server. Starting the Apache web server is a straightforward process since it is pre-installed on the Kali machine. By executing a single command, we can initiate the web server and it will become operational, allowing us to receive and serve web traffic.
![]()
The web server file is located in the directory /var/www/html. To access this file, we will launch the file manager and navigate to the aforementioned directory. Upon browsing the web server, the displayed page will resemble the provided screenshot.
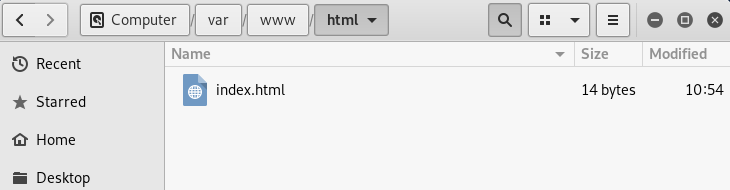
The provided image depicts a fully functional website that has been installed and configured on the web server. Upon accessing our web server’s IP address (i.e., 10.0.0.11) via a web browser, the index.html page will be displayed to the user.
In order to configure the DNS server that is integrated with MITMf, we will utilize the text editor, Leafpad. Following this, we will execute the command shown below to proceed with the configuration process.
![]()
Upon executing the aforementioned command, we will proceed to scroll down to the section containing A records, as illustrated in the provided screenshot. A records are responsible for translating domain names to their corresponding IP addresses.

Our target for this DNS configuration will be xyz.com, with a wildcard (*) designated to match any subdomain associated with this domain. This will redirect any subdomain under xyz.com to our designated IP address, 10.0.0.11. Alternatively, we may choose to redirect traffic to any other IP address, such as Google’s, by providing the appropriate IP in place of 10.0.0.11. After saving and closing the modified configuration file, we will execute a command similar to the one utilized in previous sections, with the addition of an extra option, “–dns“. The updated command is as follows:
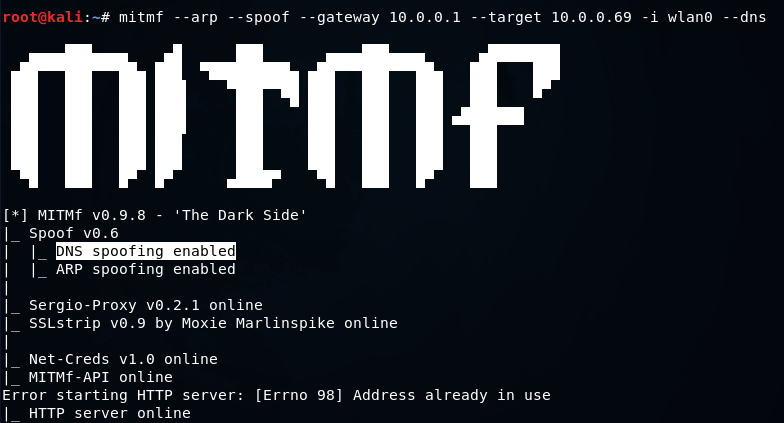
As depicted in the provided screenshot, we observe that DNS spoofing has been successfully enabled. To test this, we will attempt to access xyz.com from the target system and subsequently be redirected to our website displaying a simple text. However, this redirection can be utilized to induce the target to download a file or access a fake page with the intention of stealing sensitive information such as credentials.
DNS spoofing can be leveraged to serve fake updates to the target or carry out a range of attacks, making it a versatile tool. The method we just learned is just the basic approach to DNS spoofing. We can combine it with other techniques or ideas to execute more powerful attacks.
For more updates like DNS Spoofing, do follow us tutorials.freshersnow.com.
