“Man in the Middle Attacks” In this section, we will discuss the dangers of man-in-the-middle (MITM) attacks, which are considered among the most pernicious types of attacks on a network. A MITM attack is only possible if the attacker has already gained access to the network. The attack involves redirecting the flow of packets between clients and the router to the attacker’s device, allowing them to read, modify, or drop any transmitted packets. The efficacy of a MITM attack is due to the difficulty of protecting against it, which is related to the operation of the ARP protocol.
ARP has two primary security vulnerabilities. Firstly, it trusts the responses of each ARP request, which means that any device on the network can masquerade as another device by lying in their ARP responses. Secondly, clients accept ARP responses even when they did not make a request, making it easier for attackers to interfere with the normal flow of packets by sending unsolicited responses, redirecting traffic to the attacker’s device. To perform a MITM attack, the attacker will use a technique known as ARP poisoning or ARP spoofing, which involves sending fake ARP messages to the network. As a result, clients are misled into believing that the attacker’s device is the router, allowing the attacker to intercept and alter the packets moving through the network.
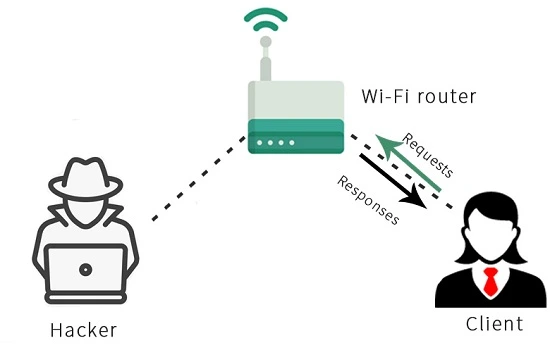
In this section, we will explore how a MITM attack works using a technique called ARP poisoning or ARP spoofing. The following diagram shows a typical Wi-Fi network, where a client sends a request to the Wi-Fi router, which in turn fetches the requested information from the internet and sends it back to the Client as a response.
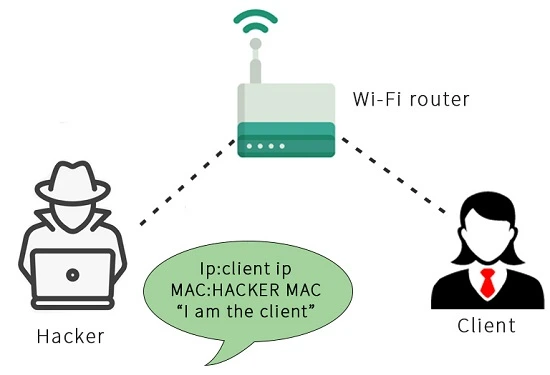
The process of MITM attack is carried out through the transmission of packets. The attacker sends an ARP response to the Client, allowing them to send responses to the Client without it asking for them. The attacker claims that their IP address is the router IP address. For example, if the router’s IP address is 192.168.0.1, the attacker will inform the Client that the device with the IP address 192.168.0.1 has their MAC address. Therefore, the Client will assume that the attacker is the router.
As a result of the ARP response we sent, the Client will begin to send packets to our device instead of the router. This redirection of packets is illustrated in the following diagram:

After that, we will perform the opposite on the Wi-Fi router. We will send an ARP response to the router, informing it that our IP address is the Client’s IP address, and that we have the MAC address of the Client. This way, the router will start sending packets to us instead of sending them to the actual Client. This will complete the MITM attack and we will be able to intercept, read, and modify the packets sent between the Client and the router.
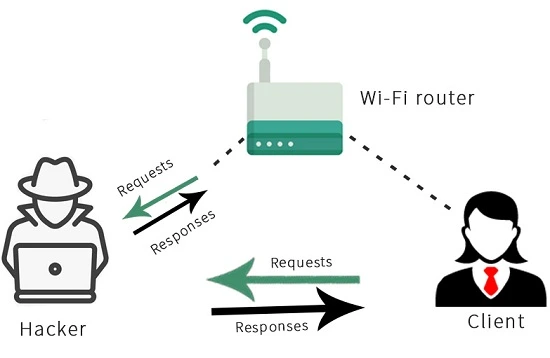
In summary, the MITM attack works by intercepting the communication between the Client and the Wi-Fi router, by sending fake ARP responses to both the Client and the router. By pretending to be the router to the Client and the Client to the router, we can control and manipulate the traffic between them, allowing us to read, modify, and drop packets at will. This attack is particularly dangerous because it can be carried out even if the network is encrypted, and it can be difficult to detect and prevent.
In the diagram, we can see that when the client wants to access Google.com, it will send the request to our device instead of sending it directly to the Wi-Fi router. Our device, acting as the router, will receive the request and forward it to the actual router. The router will then send the request to Google’s server and get the response. However, instead of sending the response directly to the client, the router will send it to our device, which will modify the response and forward it to the client. Since we have access to the data being transmitted between the client and the server, we can read or modify the data as we wish. The client is completely unaware of what is happening, and the attack is carried out without their knowledge.
When the Wi-Fi router receives a request from a client to access a website like Google.com, it will send the response to our device instead of directly to the client. As a result, every packet of information sent between the client and the website will pass through our device. Because we possess the key to decrypt the information, we are able to read, modify, or discard these packets. This means that we have the ability to intercept and manipulate the data being transmitted between the client and the website.
I understand that you have got the right information on MITM attacks in the article. If you would like to learn more about ethical hacking, please follow us @ tutorials.freshersnow.com.
